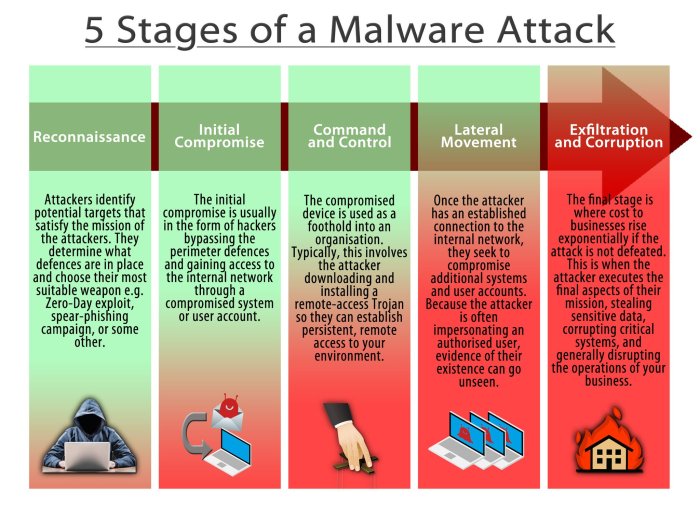
Malware persistence mechanisms used by hackers are the sneaky strategies they employ to keep their malicious software running even after a reboot. Think of it like a digital cockroach – incredibly hard to squash. This isn’t just about annoying pop-ups; we’re talking about full-blown control of your system, data theft, and potentially crippling your entire online presence. We’ll dive deep into the various techniques hackers use, from hiding in plain sight to hijacking your system’s core functions. Get ready to understand how these digital ninjas stay hidden and what you can do to fight back.
From fileless malware that lives only in your computer’s memory to registry entries that quietly execute malicious code every time you log in, the methods are diverse and constantly evolving. We’ll explore the different ways hackers achieve persistence – infecting boot sectors, manipulating system services, and even embedding themselves within seemingly harmless files. Understanding these techniques is the first step towards building a robust defense against these persistent threats. We’ll break down each method, explaining how it works, the risks involved, and – crucially – how to detect and mitigate these attacks.
Fileless Malware Persistence
Fileless malware represents a sophisticated evolution in malicious code, bypassing traditional antivirus detection methods by residing entirely within a system’s memory. Instead of relying on files stored on the hard drive, it leverages legitimate system tools and processes to execute its malicious payload, making detection and removal significantly more challenging. This approach allows for greater stealth and makes it difficult for security solutions to identify and quarantine the threat.
Fileless malware achieves persistence through various techniques that exploit the system’s functionalities without leaving a trace on the disk. This means the malware doesn’t create any new files on the system, making it incredibly difficult for traditional antivirus software to detect. This evasion tactic renders many signature-based detection methods useless, requiring more advanced behavioral analysis to identify the threat.
Techniques for Fileless Persistence
Fileless malware primarily employs two main strategies for persistence: leveraging legitimate system tools and memory injection. Using legitimate tools involves manipulating existing system utilities, such as PowerShell or Windows Management Instrumentation Command-line (WMIC), to execute malicious commands. This disguises the malware’s activity within the normal system processes, making it harder to detect. Memory injection, on the other hand, directly injects malicious code into the memory space of running processes, enabling the malware to execute without ever touching the hard drive. This method is particularly effective at evading detection, as the malware’s code exists only in RAM.
Evading Traditional Antivirus Software
The key to fileless malware’s success lies in its ability to evade traditional antivirus software. Since it doesn’t create files on the system, signature-based detection mechanisms—which rely on identifying known malware signatures within files—are rendered ineffective. Instead, fileless malware relies on obfuscation techniques, polymorphism, and the use of legitimate system tools to mask its malicious activity. Behavioral analysis, which monitors the system for suspicious actions, is crucial for detecting fileless malware, but even this approach can be challenging due to the malware’s ability to blend in with legitimate system processes.
Comparison of Fileless Persistence Techniques
While both leveraging legitimate system tools and memory injection achieve fileless persistence, they differ in their methods and detection challenges. Using legitimate tools offers a degree of stealth by hiding malicious actions within seemingly benign processes. However, it may leave more traces of activity that can be identified through careful log analysis. Memory injection, on the other hand, is more difficult to detect because it leaves no files and operates entirely within the system’s memory. The choice of technique depends on the malware’s goals and the level of stealth required.
Examples of Fileless Malware and Their Persistence Mechanisms
The following table provides examples of fileless malware and their associated persistence techniques:
| Malware Name | Persistence Method | Operating System Targeted | Detection Challenges |
|---|---|---|---|
| PowerShell Empire | PowerShell scripts, memory injection | Windows | Obfuscation, use of legitimate tools, dynamic code execution |
| Ursnif | Registry manipulation, memory injection | Windows | Advanced evasion techniques, polymorphic behavior |
| Emotet | Registry manipulation, fileless execution using legitimate tools | Windows | Rapid mutation, sophisticated anti-analysis techniques |
| Dridex | Registry manipulation, DLL injection | Windows | Use of legitimate processes, network communication obfuscation |
Registry-Based Persistence
Malware often leverages the Windows Registry, a hierarchical database storing system configuration information, to establish persistent infection. This allows the malware to automatically re-execute itself even after a system reboot, ensuring its continued presence and operation. Understanding how malware manipulates the registry is crucial for effective security measures.
Registry manipulation for persistence involves creating or modifying specific registry keys and values that trigger the execution of malicious code upon system startup or other defined events. This method is favored by many attackers due to its relative simplicity and effectiveness. However, it’s not foolproof, and skilled defenders can detect and remove these registry entries.
Registry Keys and Values Commonly Modified
Malware commonly targets several registry keys to achieve persistence. These keys are associated with program startup, run commands, and other system events. Modifying values within these keys allows the malware to inject its own execution commands. Examples include the `Run`, `RunOnce`, `RunServicesOnce`, and `User Shell Folders` keys within `HKEY_CURRENT_USER` and `HKEY_LOCAL_MACHINE`. The specific key used depends on the desired persistence scope (user-level or system-wide) and the trigger for execution. The value data within these keys typically contains the path to the malicious executable or a script designed to execute it.
Creating and Modifying Registry Entries
The process involves using system calls or APIs to interact with the registry. Malware might create a new registry key and value, or modify an existing one. For example, a malicious program could add a new value to the `Run` key under `HKEY_CURRENT_USER`, pointing to its own executable file. Upon user login, the system would automatically execute this file. This process is often performed with elevated privileges to avoid access restrictions. Sophisticated malware may also employ techniques to obfuscate its registry entries, making detection more challenging.
Advantages and Disadvantages of Registry-Based Persistence
Using the registry offers advantages such as relative ease of implementation and the ability to achieve both user-level and system-wide persistence. It’s a well-established method, and many tools and techniques are available to facilitate this type of persistence. However, registry modifications are readily detectable by security software, making this method less stealthy than others. Furthermore, improper registry manipulation can lead to system instability or crashes, potentially alerting the user or administrator to the presence of malware.
Hypothetical Scenario: Registry-Based Persistence
Imagine a hypothetical piece of ransomware, “CryptLock,” that infects a system. During its execution, CryptLock first checks for administrator privileges. If it has them, it proceeds to create a new registry value under `HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run`. The value name is randomly generated, and the value data points to a hidden encrypted copy of the ransomware executable located in the `%System32%` directory. This ensures the ransomware automatically restarts with the system, even after a reboot, and makes removal more difficult as the location is a protected system directory. The encryption ensures that even if the registry entry is detected, the ransomware itself remains hidden and functional. This is a simplified example; real-world ransomware employs far more sophisticated techniques for persistence and evasion.
Boot Sector and Master Boot Record (MBR) Infection
Deep in the heart of your computer, before the operating system even loads, lies the Master Boot Record (MBR) and the boot sector. These crucial areas are responsible for initiating the boot process, and unfortunately, they’re prime targets for persistent malware. An infection here means the malware loads *before* your antivirus even has a chance to run, making it incredibly difficult to remove.
Malware infects the boot sector or MBR by overwriting critical parts of these sectors with its own code. This malicious code can range from simple boot loaders that launch the main malware payload to complex routines that actively hide or disrupt the normal boot process. The methods employed are often sophisticated, exploiting vulnerabilities in the boot process or using rootkit techniques to remain undetected. Think of it like replacing the instruction manual for your computer with a rogue version that subtly steers the system towards the attacker’s goals.
Consequences of Boot Sector or MBR Infection
A compromised boot sector or MBR can lead to a range of severe consequences, impacting both system stability and data integrity. System instability manifests as boot failures, system crashes, and unpredictable behavior. The malware might display custom boot messages, redirect the boot process to a different location (potentially leading to data loss or ransomware execution), or simply prevent the system from booting altogether. Data integrity is also at risk, as the malware could potentially modify or delete files, encrypt data (ransomware), or even steal sensitive information before the operating system even loads. Imagine your computer refusing to start, displaying a cryptic message, or worse, encrypting all your files – this is the reality of a boot sector infection.
Challenges in Removing Boot Sector Malware
Removing malware from the boot sector is significantly more challenging than removing it from other locations on the hard drive. Traditional antivirus software often operates *after* the operating system has loaded, rendering them ineffective against boot sector infections. The infected sector is also extremely sensitive; any attempt to modify it incorrectly could lead to complete data loss or render the system unbootable. Furthermore, boot sector malware often employs techniques to hide its presence and resist removal attempts, requiring specialized tools and expertise for remediation. This is like trying to fix a broken engine while the car is still running – extremely risky and requiring precision.
Analyzing a System with Suspected Boot Sector Infection
Analyzing a system suspected of having a boot sector infection requires a methodical approach, utilizing specialized tools and caution. First, carefully observe the boot process for any unusual messages or delays. Next, use a bootable antivirus or malware scanning tool (from a reputable source) on a separate system to create a bootable media (like a USB drive). Boot from this media instead of the potentially infected hard drive. This allows the scanning of the MBR and boot sector without loading the potentially compromised operating system. Finally, if malware is detected, carefully follow the instructions provided by the chosen tool for remediation. Remember, incorrectly attempting to repair the boot sector can lead to catastrophic data loss, so proceeding with caution and ideally seeking professional assistance is crucial. This is akin to performing delicate surgery – a precise and careful approach is essential.
Persistence through System Services
Malware authors often exploit legitimate system services to establish persistent infection. This method allows malware to execute automatically upon system startup, often remaining undetected for extended periods. By leveraging existing system infrastructure, the malware blends seamlessly into the operating system’s normal functionality, making it harder to identify and remove.
System services, or daemons, are programs that run in the background, providing essential functions to the operating system. Malware can hijack these services by creating new ones that execute malicious code or by modifying existing services to include malicious payloads. This provides a robust and stealthy persistence mechanism.
Examples of Abused System Services, Malware persistence mechanisms used by hackers
Several system services are frequently targeted by malware due to their privileged access and frequent execution. These services offer a convenient avenue for persistent infection. Understanding these common targets is crucial for effective threat detection and response.
- Windows Management Instrumentation (WMI): WMI provides a powerful interface for managing and monitoring system resources. Malware can create persistent event subscriptions that trigger malicious code execution.
- Scheduled Tasks: The Task Scheduler allows users to automate tasks. Malware can create new scheduled tasks that execute malicious code at specific intervals or upon certain events.
- Services Control Manager (SCM): The SCM manages all system services. Malware can install itself as a new service, ensuring its automatic execution at startup.
- Driver Execution: Malware can install malicious device drivers, which are loaded by the operating system during startup and have high privileges.
Creating or Modifying a Service for Malicious Purposes
The process of establishing persistence through system services often involves creating a new service or modifying an existing one. This typically involves several steps, each carefully designed to evade detection.
The creation of a new malicious service might involve using tools like sc.exe (on Windows) to create a new service entry in the registry. This entry specifies the path to the malicious executable, startup type (automatic), and other relevant parameters. The malware then ensures the malicious executable is placed on the system and configured for execution. Modifying an existing service involves similar steps but instead of creating a new entry, the malware alters the existing service’s executable path to point to the malicious code. This can be done through direct registry manipulation or through exploitation of vulnerabilities in the service itself. The malicious code within the modified service will then execute whenever the service is started.
Identifying and Analyzing Suspicious Services
Identifying malicious services requires careful examination of the system’s service list and registry entries. Several indicators can suggest malicious activity.
Suspicious services often exhibit unusual characteristics such as:
- Unknown or unexpected service names: Names that are obfuscated or don’t correspond to known legitimate services.
- Unusual paths to executable files: Executable files located in unusual directories or with unusual names.
- High privileges: Services running with elevated privileges are more dangerous if compromised.
- Uncommon startup types: Services set to start automatically are more likely to be malicious if not known legitimate ones.
- Recent creation timestamps: Newly created services should be investigated thoroughly.
Analyzing suspicious services involves examining the executable file itself using tools like a sandbox environment or a reverse engineering tool to determine its functionality. Checking the service’s registry entries for suspicious values and cross-referencing the service name and executable path with known malware databases are also important steps. Furthermore, examining the service’s dependencies and network connections can provide additional clues.
Persistence via Scheduled Tasks and Startup Programs
Source: computersolve.com
Malware authors cleverly exploit the features designed for legitimate software automation to achieve persistence. By manipulating scheduled tasks and startup programs, malware ensures its execution even after a system reboot, making eradication significantly more challenging. This persistence mechanism is incredibly effective due to its integration within the operating system’s core functionality, often remaining hidden in plain sight.
Malware employs various techniques to embed itself within the system’s startup processes. These methods range from subtly modifying existing entries to creating entirely new scheduled tasks and startup items. The locations where this malicious code is placed are often well-hidden, making manual detection difficult even for experienced users. Understanding these techniques is crucial for effective malware prevention and removal.
Methods of Creating or Modifying Scheduled Tasks and Startup Programs
Malware can create new scheduled tasks using the Windows Task Scheduler, configuring them to run at specific intervals or upon system startup. This often involves creating a new task with a seemingly innocuous name, masking its malicious intent. Alternatively, existing scheduled tasks might be modified, with the malware altering their commands to execute malicious code instead of the original program. This manipulation often goes unnoticed, as the task’s name and apparent purpose remain unchanged. In addition, malware might leverage scripting languages like PowerShell or VBScript to create and manage these tasks, further obscuring its actions. For instance, a script could be scheduled to run daily, downloading and executing a payload from a remote server.
Common Locations for Malware in the Startup Sequence
Malware commonly targets several locations to ensure its persistence through startup programs. The Windows Registry holds several keys dedicated to startup applications, such as the `Run` key under `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion` and `HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run`. These registry keys are frequently exploited, with malware adding its own entries pointing to malicious executables or scripts. Furthermore, the Startup folder located in the user’s profile directory (`%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup`) is another common target. Files placed here are automatically executed upon user login. The persistence mechanism also extends to other locations, including the `Startup` folder within the `All Users` profile, affecting all users on the system. This broadens the malware’s reach and increases its chances of survival.
Effectiveness of Scheduled Tasks vs. Startup Programs
Both scheduled tasks and startup programs provide effective persistence mechanisms, but they offer slightly different advantages. Scheduled tasks offer greater flexibility, allowing malware to execute at specific times or intervals, even if the user is not logged in. This makes detection more difficult, as the malware’s activity might not be immediately apparent. Startup programs, on the other hand, are typically executed upon user login, offering immediate access to system resources. The choice between these two methods often depends on the malware’s specific goals and the capabilities of the attacker. A sophisticated malware might even employ both methods for redundancy, ensuring its persistence regardless of user activity or system state.
Indicators of Compromise (IOCs) for Malicious Scheduled Tasks and Startup Entries
Identifying malicious entries requires careful examination. A list of indicators that may suggest malicious activity includes:
- Unfamiliar or suspicious task names or program names.
- Tasks or programs with unusual execution times or triggers.
- Tasks or programs with paths pointing to unusual or unknown directories.
- Tasks or programs with excessive system resource consumption.
- Tasks or programs that execute commands or scripts with suspicious behavior.
- Tasks or programs associated with known malicious software.
- Unexpectedly high number of scheduled tasks or startup programs.
- Tasks or programs that attempt to connect to unknown or suspicious network locations.
- Tasks or programs that modify system files or registry settings without user consent.
- Tasks or programs that create or modify other scheduled tasks or startup entries.
Analyzing these indicators can significantly aid in identifying and removing persistent malware.
Network-Based Persistence: Malware Persistence Mechanisms Used By Hackers
Source: twimg.com
Malware doesn’t always need to reside directly on a victim’s machine to maintain its grip. Network-based persistence allows malicious actors to maintain control and access even after a system reboot or software update. This is achieved by establishing a persistent connection between the infected system and a remote server controlled by the attacker. This persistent connection acts as a backdoor, providing ongoing access for nefarious activities.
Network-based persistence leverages various techniques, primarily utilizing backdoors and remote access tools (RATs). These tools establish a covert communication channel between the compromised system and a command-and-control (C&C) server. The C&C server acts as a central hub, allowing the attacker to remotely manage the infected system, deploy further malware, exfiltrate data, or carry out other malicious actions. Think of it as a persistent, invisible string connecting the attacker to the victim’s system, no matter what happens on the victim’s end.
Examples of Network-Based Persistence Mechanisms
Several methods facilitate network-based persistence. For instance, malware might create a reverse shell, establishing an outbound connection to a C&C server. This allows the attacker to execute commands on the compromised system remotely. Another common method involves using legitimate network services for malicious purposes, like tunneling commands through seemingly innocuous protocols such as SSH or HTTPS. This makes detection significantly more challenging. Furthermore, some malware utilizes domain generation algorithms (DGAs) to generate a constantly evolving list of domains, making it difficult to block all communication channels. Imagine a hydra, with many heads (domains) constantly regenerating. Blocking one head (domain) only temporarily stops the connection.
Challenges in Detecting and Mitigating Network-Based Persistence
Detecting network-based persistence presents a unique set of hurdles. Traditional antivirus solutions primarily focus on local file system analysis, often missing the subtle network communications associated with these persistent connections. Network traffic analysis is crucial, but the use of encryption and legitimate protocols makes identifying malicious traffic challenging. Behavioral analysis, examining unusual network activity patterns, becomes a more effective approach. Furthermore, the dynamic nature of some network-based persistence techniques, like DGAs, requires advanced threat intelligence and proactive measures to stay ahead of the attackers.
The Role of Command-and-Control (C&C) Servers
C&C servers are the central nervous system of network-based persistence. They act as the control point for the attacker, receiving commands from the compromised systems and sending instructions back. These servers can be located anywhere in the world, often using techniques to obfuscate their location and identity. The attacker can use the C&C server to update the malware, deploy new modules, or switch communication methods to evade detection. Think of it as the hacker’s control room, remotely managing their network of compromised machines. Neutralizing the C&C server is a critical step in disrupting a network-based persistence attack, but finding and disabling them is often a complex undertaking, requiring significant technical expertise and resources.
Data Persistence Techniques

Source: cyberselves.org
Malware doesn’t just want to wreak havoc; it wants to stick around. Data persistence techniques are the sneaky ways malware achieves this longevity, embedding itself within seemingly innocent files and data streams to evade detection and ensure its continued operation. This is a far cry from the more obvious persistence methods like registry entries or scheduled tasks; it’s a game of hide-and-seek at the digital level.
Malware employs several sophisticated methods to achieve persistence by hiding within data. These methods often involve manipulating legitimate files or creating seemingly benign data streams to conceal malicious code. This makes detection and removal significantly more challenging, demanding advanced analysis techniques.
Data Hiding and Encryption Techniques
Malware can cleverly embed itself within the data streams of various file types, using techniques that blend malicious code with legitimate data to evade detection. One common method is to insert malicious code within the metadata of a file, such as a document or image. This metadata often contains information like author details, creation date, or s, and the malware can insert its code within this section, making it harder to spot using standard antivirus scanners. Another technique involves using steganography, which hides data within other data. For instance, malware could modify the least significant bits of an image file to encode its malicious payload without visibly altering the image. Encryption further complicates matters, rendering the embedded malware unintelligible unless the decryption key is known. This layered approach – embedding within metadata and then encrypting – significantly increases the difficulty of detection.
Challenges in Identifying and Removing Data-Persistent Malware
Identifying and removing malware that uses data persistence techniques presents significant challenges. Traditional antivirus software often struggles to detect such cleverly hidden payloads, requiring more advanced techniques like static and dynamic analysis. Static analysis involves examining the file’s structure and code without executing it, while dynamic analysis involves monitoring the file’s behavior during execution. The encrypted nature of many payloads adds another layer of complexity, requiring specialized decryption tools and expertise. Even if detected, removing the malware without damaging the host file can be incredibly difficult, potentially requiring the entire file to be replaced. The sheer volume of data involved in many files makes this a time-consuming and resource-intensive process.
Example: Malware Hidden within a JPEG Image
Imagine a JPEG image file. JPEGs use a specific format to store image data, including metadata like EXIF (Exchangeable Image File Format) data. Malware could be injected into the EXIF data, appearing as just another metadata entry alongside camera model and date information. This data is often overlooked by casual users and even some security software. Furthermore, the malware payload itself could be encrypted, making it appear as random data within the EXIF section. To further complicate detection, the malware could modify the image slightly, changing only a few bits here and there to ensure that the visual representation of the image remains unchanged, while the embedded malware remains active and operational. The visual representation would be essentially unchanged to the naked eye, and even many image viewers would not display any anomalies. Removing the malware would require specialized tools to identify and extract the malicious code from the EXIF data, potentially requiring the rebuilding of the EXIF section of the file.
Final Summary
So, the digital battlefield is far from static. Hackers are constantly refining their persistence techniques, making the fight against malware an ongoing arms race. Understanding the diverse strategies they employ – from the subtle to the brutally effective – is critical for staying ahead of the curve. While complete eradication might seem like a utopian dream, by understanding these mechanisms, we can significantly improve our defenses, bolster our security posture, and minimize the impact of a successful breach. Stay vigilant, stay informed, and stay safe.





