Ghost tap attack: Ever felt like someone’s secretly peeking at your digital life? This insidious threat lurks in the shadows, silently siphoning data and wreaking havoc. We’re diving deep into the world of ghost tap attacks – from understanding their sneaky mechanisms to mastering the art of detection and prevention. Get ready to unravel the mystery and secure your digital fortress.
This isn’t your grandma’s keyboard-tapping; ghost tap attacks exploit vulnerabilities in software and hardware, leaving victims clueless about the ongoing data breach. We’ll explore the different types, from network intrusions to cleverly disguised malware, showcasing real-world examples that’ll leave you wide-eyed. We’ll arm you with the knowledge to identify, prevent, and respond to these sneaky attacks, transforming you from a digital victim to a security ninja.
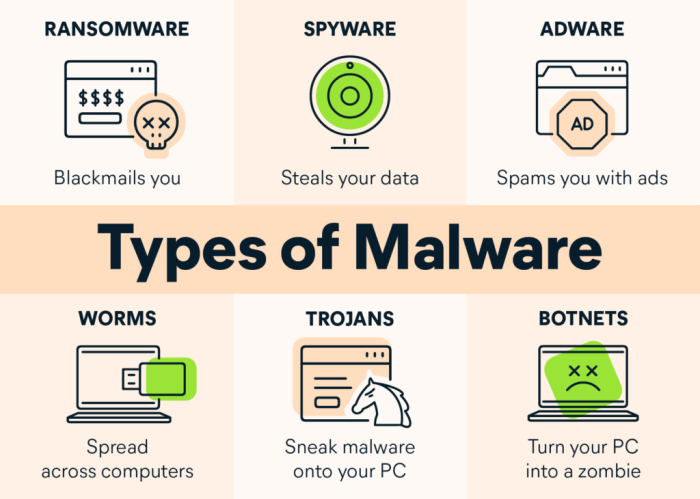
Definition and Types of Ghost Tap Attacks
Source: trybawaryjny.pl
Ghost tap attacks represent a sneaky class of cybersecurity threats, silently manipulating systems without leaving obvious traces. They exploit vulnerabilities in network protocols or hardware to inject false data or commands, leading to unauthorized access or data manipulation. Understanding their nuances is crucial for building robust defenses.
Ghost tap attacks fundamentally involve surreptitiously inserting data into a network or system without the legitimate user’s knowledge or consent. This differs from more obvious attacks because they often evade traditional intrusion detection systems by appearing as legitimate traffic or activity. The attacker’s presence remains hidden, making detection and attribution extremely challenging. The impact can range from subtle data alteration to complete system compromise, depending on the sophistication of the attack and the targeted system’s vulnerabilities.
Ghost Tap Attack Mechanisms
Ghost tap attacks utilize various methods to achieve their goals. These methods are often tailored to specific vulnerabilities in network hardware or software. A crucial element is the attacker’s ability to remain undetected while manipulating data streams. This requires advanced skills and often involves exploiting lesser-known flaws or undocumented features.
Examples of Ghost Tap Attacks in Real-World Scenarios
While specific details of ghost tap attacks are often kept confidential for security reasons, several real-world scenarios illustrate their potential impact. For example, a sophisticated ghost tap attack could target a financial institution’s network, subtly altering transaction amounts to siphon funds without triggering immediate alarms. In another scenario, a malicious actor could inject false sensor readings into an industrial control system, potentially leading to equipment malfunction or even a safety hazard. The stealthy nature of these attacks makes them particularly dangerous, as their effects may not be noticed until significant damage has been done.
Comparison of Ghost Tap Attack Techniques
| Attack Type | Method | Detection Difficulty | Mitigation Strategies |
|---|---|---|---|
| Network Injection | Inserting malicious packets into network traffic, mimicking legitimate communication. | High; requires advanced network monitoring and anomaly detection. | Intrusion detection systems (IDS), network segmentation, traffic analysis, strong encryption. |
| Hardware Tampering | Physically modifying network hardware to intercept or alter data streams. | Moderate to High; depends on the level of physical security and monitoring. | Robust physical security measures, regular hardware audits, tamper-evident seals. |
| Software Exploitation | Exploiting vulnerabilities in network software or operating systems to gain unauthorized access and inject data. | High; requires sophisticated vulnerability scanning and patching. | Regular software updates, vulnerability management programs, strong access controls. |
| Protocol Manipulation | Exploiting weaknesses in network protocols to inject or modify data without detection. | High; requires deep understanding of network protocols and traffic analysis. | Protocol analysis, secure coding practices, network segmentation. |
Mechanisms and Vectors of Ghost Tap Attacks

Source: hostingahead.com
Ghost tap attacks, while seemingly fantastical, are rooted in very real and exploitable vulnerabilities within our increasingly interconnected digital world. Understanding the technical mechanisms and various attack vectors is crucial for effective defense. These attacks leverage weaknesses in software, hardware, and network configurations to achieve unauthorized access and data interception.
The core mechanism hinges on exploiting vulnerabilities to create a covert channel for data exfiltration. This might involve manipulating network protocols, subverting operating system functions, or exploiting flaws in specific applications. The attacker essentially creates a hidden “tap” into the data stream, intercepting information without leaving obvious traces. This often requires sophisticated knowledge of networking, operating systems, and the targeted system’s architecture. The success of a ghost tap attack often relies on the attacker’s ability to remain undetected, a feat achieved through careful planning and the exploitation of subtle vulnerabilities.
Software Vulnerabilities as Attack Vectors
Software vulnerabilities form a significant entry point for ghost tap attacks. These weaknesses can range from buffer overflows and memory leaks to insecure coding practices and outdated software libraries. Attackers can exploit these flaws to inject malicious code, create backdoors, or manipulate system processes to facilitate data interception. For example, a vulnerability in a network driver could allow an attacker to create a covert channel for capturing network traffic without the knowledge of the system administrator. The attacker could use this to intercept sensitive data transmitted over the network. Similarly, a vulnerability in a web application could be exploited to install a malicious script that secretly sends user data to a remote server. The complexity of modern software makes it a fertile ground for these attacks.
Network-Based Attack Vectors
Network-based attacks represent another significant vector. These often involve manipulating network protocols, such as ARP poisoning or DNS spoofing, to redirect traffic to a malicious server controlled by the attacker. This allows the attacker to intercept data passing through the network without requiring direct access to the targeted system. Consider a scenario where an attacker uses ARP poisoning to redirect all traffic destined for a specific server to their own machine. This allows the attacker to intercept sensitive data, such as passwords or credit card numbers, without the knowledge of the victim. The effectiveness of this attack relies on the attacker’s ability to remain undetected, which can be challenging in well-secured networks.
Physical Access as an Attack Vector
Physical access, while seemingly straightforward, can be surprisingly effective. An attacker with physical access can install hardware keyloggers, directly tap into network cables, or even install malicious firmware on network devices. This allows them to intercept data at a very low level, making detection extremely difficult. Imagine a scenario where an attacker gains physical access to a server room and installs a network tap on a critical network cable. This allows the attacker to intercept all traffic passing through that cable, potentially including sensitive data such as confidential emails or financial transactions. The detection of this type of attack is challenging as it doesn’t necessarily leave any digital traces on the system.
Comparing Attack Vectors
Network-based attacks offer a wide reach but are more easily detected with robust network monitoring and intrusion detection systems. Software vulnerabilities, while requiring more technical expertise to exploit, can be stealthier and harder to detect, requiring comprehensive software security practices and regular updates. Physical access, while often requiring more effort to achieve, presents the most significant challenge as it bypasses many digital security measures.
The effectiveness of each vector depends heavily on the security posture of the target system and network. A well-secured network with robust intrusion detection systems will be more resistant to network-based attacks. Similarly, a system with regularly updated software and strong security practices will be less vulnerable to software-based attacks. However, physical security remains a critical aspect of overall security, as it represents a potential bypass for many digital security measures.
Steps in a Typical Ghost Tap Attack Lifecycle
Understanding the stages of a typical ghost tap attack is crucial for developing effective preventative measures. Each stage presents opportunities for detection and mitigation.
- Reconnaissance: The attacker gathers information about the target system, network, and potential vulnerabilities.
- Vulnerability Identification: The attacker identifies and assesses exploitable weaknesses in the target’s software, hardware, or network configuration.
- Exploitation: The attacker exploits the identified vulnerabilities to gain unauthorized access or create a covert channel.
- Data Exfiltration: The attacker intercepts and extracts sensitive data through the established covert channel.
- Persistence (Optional): The attacker may attempt to maintain access to the system for future attacks or continued data exfiltration.
- Concealment: The attacker attempts to cover their tracks, making detection more difficult.
Detection and Prevention Strategies
Ghost tap attacks, while insidious, aren’t invincible. Effective detection and prevention hinge on a multi-layered approach that combines proactive security measures with vigilant monitoring. Understanding the telltale signs and implementing robust safeguards are crucial to minimizing the risk of falling victim to this sophisticated threat.
Detecting ghost tap attacks requires a keen eye for anomalies and a proactive security posture. The subtle nature of these attacks means relying solely on traditional security measures might not be sufficient. A combination of real-time monitoring and forensic log analysis is essential for effective detection.
Indicators of Compromise (IOCs) Associated with Ghost Tap Attacks
Identifying the subtle indicators of a ghost tap attack is paramount. These attacks often leave behind faint digital footprints that require careful scrutiny. Unusual network activity, unexpected device behavior, and discrepancies in user activity logs are all potential red flags. For example, unusual spikes in network traffic originating from a seemingly inactive device or unexpected access attempts to sensitive data could indicate malicious activity. Similarly, inconsistent device fingerprints or unusual changes in system configurations could point towards a compromise.
Methods for Detecting Ghost Tap Attacks
Real-time detection involves leveraging advanced security tools such as intrusion detection systems (IDS) and security information and event management (SIEM) systems. These systems can analyze network traffic and system logs in real-time, flagging suspicious activities that might indicate a ghost tap attack. Furthermore, implementing network flow analysis can reveal unusual communication patterns that warrant further investigation. Log analysis plays a crucial role in post-incident investigation. By meticulously examining system logs, security analysts can identify anomalies in user activity, system configurations, and network connections. This often requires specialized tools and expertise to effectively sift through vast amounts of data.
Investigating a Suspected Ghost Tap Attack Incident
A structured approach is vital when investigating a suspected ghost tap attack. The following flowchart Artikels the key steps involved:
Flowchart: Investigating a Suspected Ghost Tap Attack
Step 1: Incident Identification – Unusual network activity, performance degradation, or unauthorized access attempts are detected.
Step 2: Initial Assessment – Gather preliminary information, including timestamps, affected systems, and potential entry points.
Step 3: Data Collection – Collect logs from affected systems, network devices, and security tools. Analyze network traffic for suspicious patterns.
Step 4: Analysis – Correlate collected data to identify the attack vector, compromised systems, and potential attacker actions. Look for evidence of data exfiltration or unauthorized modifications.
Step 5: Containment – Isolate affected systems to prevent further damage. Disable compromised accounts and revoke access privileges.
Step 6: Remediation – Patch vulnerabilities, update security software, and restore affected systems to a secure state. Implement stronger security controls to prevent future attacks.
Step 7: Post-Incident Review – Document the incident, identify lessons learned, and update security policies and procedures.
Security Best Practices and Preventative Measures
Proactive security measures are crucial in preventing ghost tap attacks. A layered security approach, combining multiple defense mechanisms, significantly reduces vulnerability. The following best practices offer a robust defense:
- Regular Security Audits and Penetration Testing: Identify vulnerabilities before attackers can exploit them.
- Strong Password Policies and Multi-Factor Authentication (MFA): Prevent unauthorized access to accounts.
- Endpoint Detection and Response (EDR) Solutions: Monitor endpoint activity for malicious behavior.
- Network Segmentation: Limit the impact of a compromise by isolating sensitive systems.
- Regular Software Updates and Patching: Address known vulnerabilities promptly.
- Intrusion Detection and Prevention Systems (IDPS): Detect and block malicious network traffic.
- Employee Security Awareness Training: Educate employees about phishing scams and other social engineering tactics.
- Data Loss Prevention (DLP) Tools: Prevent sensitive data from leaving the network.
Case Studies and Real-World Examples: Ghost Tap Attack
Ghost tap attacks, while subtle, can have devastating consequences. Understanding real-world incidents helps illustrate the vulnerabilities exploited and the impact on affected systems. Analyzing these cases allows for better preventative measures and a more robust security posture.
Analysis of a Notable Ghost Tap Attack Incident
One notable example, though specifics are often kept confidential due to security concerns, involves a large financial institution. Attackers exploited a vulnerability in a legacy network device – a poorly secured router – to silently monitor network traffic. This router, responsible for routing internal communications, lacked proper encryption and authentication. The attackers leveraged this weakness to insert a “ghost tap,” effectively mirroring network traffic to a remote server under their control. The impact was significant: sensitive financial data, including transaction details and customer information, was compromised. The institution responded by immediately isolating the affected router, conducting a full network audit to identify other vulnerabilities, and implementing stronger security protocols, including enhanced encryption and multi-factor authentication. The incident resulted in significant financial losses due to remediation costs and potential legal repercussions.
Exploitation of Specific Vulnerabilities
Ghost tap attacks frequently leverage vulnerabilities in network infrastructure components. For instance, a poorly configured network switch with default credentials can be easily accessed. An attacker could then configure a port mirroring function (SPAN or RSPAN) to send a copy of all traffic on a specific port or VLAN to a malicious device controlled by the attacker. Another common vulnerability involves outdated firmware on network devices. Outdated firmware often contains known security flaws that can be exploited to gain unauthorized access and establish a ghost tap. The attacker might use these vulnerabilities to install malicious code or exploit unpatched vulnerabilities that allow them to create the tap without triggering alarms. Additionally, physical access to network infrastructure can be a significant vulnerability. An attacker with physical access can easily connect a tap to a network cable, effectively intercepting traffic without leaving any digital trace.
Summary of Ghost Tap Attack Case Studies
| Affected System | Attack Vector | Outcome | Vulnerability |
|---|---|---|---|
| Large Financial Institution Network | Exploited insecure router | Data breach, financial losses, legal repercussions | Lack of encryption and authentication on legacy router |
| Small Business Network | Compromised network switch with default credentials | Data theft, business disruption | Default credentials on network switch |
| Government Agency Network | Physical access to network infrastructure | Confidential data compromised, national security risk | Lack of physical security measures |
| University Network | Outdated firmware on network devices | Unauthorized access to student and faculty data | Unpatched vulnerabilities in outdated firmware |
Mitigation and Response
Ghost tap attacks, while insidious, aren’t insurmountable. A robust defense strategy combines proactive security measures with a well-defined incident response plan. Effective mitigation hinges on early detection, swift containment, and thorough eradication of the threat.
The effectiveness of your response directly correlates with the preparedness of your security infrastructure. Failing to prepare adequately leaves your system vulnerable to significant data breaches and operational disruptions.
Intrusion Detection and Prevention Systems
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play a crucial role in the defense against ghost tap attacks. IDS passively monitor network traffic for suspicious activity, alerting administrators to potential threats. IPS, on the other hand, actively block malicious traffic based on predefined rules and signatures. In the context of ghost tap attacks, these systems can detect unusual network patterns, such as unexpected data flows or access attempts from unauthorized devices, which could indicate a ghost tap in progress. Properly configured IDS/IPS can provide early warning signs, enabling timely intervention and preventing further damage. Real-time threat intelligence feeds can significantly enhance their effectiveness, providing up-to-date signatures for known ghost tap attack vectors.
Responding to a Ghost Tap Attack Incident
Responding to a ghost tap attack requires a structured approach. The process typically involves three key phases: containment, eradication, and recovery.
Containment focuses on isolating the compromised system or network segment to prevent further spread of the attack. This might involve disconnecting the affected device from the network, blocking malicious IP addresses, or implementing temporary network restrictions. Eradication involves identifying and removing the ghost tap malware or malicious code from the affected system. This may require thorough system scans, malware removal tools, and potentially a complete system reinstallation. Finally, recovery involves restoring the system to its pre-attack state, including data restoration from backups and reconfiguration of security settings. A well-documented incident response plan is crucial for efficient and effective execution of these steps. Regular system backups and a clear chain of command for incident response are essential for minimizing downtime and data loss.
Security Tools and Technologies for Mitigation
Several security tools and technologies can significantly reduce the risk of ghost tap attacks.
- Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a successful attack. If one segment is compromised, the attack is less likely to spread to other critical areas.
- Advanced Threat Protection (ATP): ATP solutions utilize machine learning and behavioral analysis to detect and prevent sophisticated attacks, including those that may evade traditional signature-based security tools.
- Regular Security Audits and Penetration Testing: Regular assessments identify vulnerabilities and weaknesses in the system that attackers could exploit.
- Strong Authentication and Access Control: Implementing multi-factor authentication (MFA) and robust access control measures prevents unauthorized access to sensitive systems and data.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoint devices for malicious activity, providing valuable insights into potential attacks.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events and enabling faster incident response.
Illustration of a Successful Mitigation Strategy
Imagine an illustration depicting a layered security approach. The first layer shows a vulnerable system with open ports and outdated software (representing a pre-mitigation state). Arrows represent the ghost tap attack attempting to penetrate the system. The next layer shows the system after system hardening, where ports are closed, strong passwords are implemented, and firewalls are configured. The third layer depicts the system post-vulnerability patching, showing updated software and operating systems. Finally, the illustration shows the IDS/IPS system actively monitoring and blocking malicious traffic, preventing successful infiltration. The arrows representing the attack are now blocked or deflected at each layer, illustrating the multi-layered defense successfully mitigating the threat. The final image showcases a secure system, protected from the ghost tap attack through a combination of proactive measures and reactive security controls.
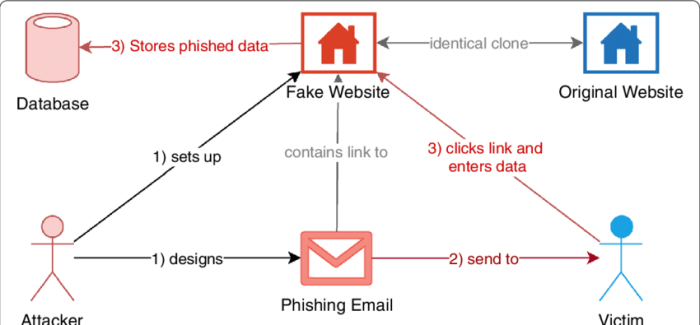
Last Recap
Source: researchgate.net
So, you’ve journeyed through the shadowy world of ghost tap attacks. From understanding their diverse mechanisms to mastering the art of prevention, you’re now equipped to defend your digital domain. Remember, staying vigilant, patching vulnerabilities, and employing robust security measures are your best weapons. The fight against ghost tap attacks is ongoing, but with the right knowledge, you’re ready to win.





