Domain based message authentication reporting conformancedmarc – Domain Based Message Authentication Reporting & Conformance (DMARC): Ever wondered how to stop those pesky phishing emails pretending to be from your favorite bank? DMARC is your secret weapon. This isn’t your grandpappy’s email authentication; we’re talking about a robust system that uses SPF and DKIM to verify sender legitimacy, giving you a serious edge in the ongoing email security arms race. Think of it as adding a digital fingerprint to your emails, ensuring only genuine messages reach your inbox (and your customers’ inboxes).
This guide dives deep into the nitty-gritty of DMARC implementation, from setting up your policies (p=reject, anyone?) to interpreting those sometimes-cryptic reports. We’ll cover everything from the technical details—SPF and DKIM, we’re looking at you—to practical advice and real-world examples. Get ready to level up your email security game.
DMARC Explained
DMARC, or Domain-based Message Authentication, Reporting & Conformance, is like adding a super-powered security system to your email domain. It helps protect your brand’s reputation and your recipients’ inboxes from phishing and spoofing attacks. Think of it as the ultimate email authentication trifecta, ensuring that only legitimate emails from your domain actually reach your recipients’ inboxes.
DMARC builds upon two existing email authentication protocols: SPF and DKIM. It doesn’t independently authenticate emails; instead, it leverages the results of SPF and DKIM checks to determine how to handle emails that fail these checks. This means it’s crucial to have SPF and DKIM properly configured before implementing DMARC.
SPF and DKIM: The Foundation of DMARC
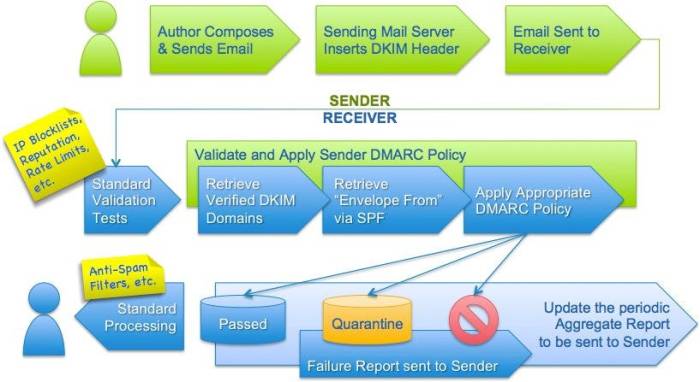
SPF, or Sender Policy Framework, verifies the sender’s IP address. It essentially creates a list of authorized mail servers that are allowed to send emails on behalf of your domain. If an email purports to come from your domain but is sent from an unauthorized IP address, SPF will flag it as potentially fraudulent. DKIM, or DomainKeys Identified Mail, uses digital signatures to verify the email’s content hasn’t been tampered with during transit. It ensures the message hasn’t been altered since it left your mail server. DMARC uses the results of these two checks to make informed decisions about how to handle emails.
Implementing DMARC: A Step-by-Step Guide
Implementing DMARC involves a phased approach to minimize disruption and allow time for adjustments. Here’s a typical implementation plan:
1. Publish SPF and DKIM records: Before even thinking about DMARC, ensure your SPF and DKIM records are correctly configured and working. This forms the foundation upon which DMARC relies.
2. Start with `p=none`: Begin with a DMARC policy of `p=none`. This instructs receiving mail servers to simply report any authentication failures to you, without taking any action (like quarantining or rejecting emails). This allows you to analyze the reports and identify potential issues before implementing stricter policies.
3. Monitor and Analyze Reports: Regularly review the DMARC reports generated by receiving mail servers. These reports detail the authentication results of emails sent from your domain. This helps pinpoint any configuration errors or unauthorized senders.
4. Transition to `p=quarantine`: Once you’ve analyzed the reports and addressed any issues, you can move to a `p=quarantine` policy. This instructs receiving mail servers to quarantine emails that fail authentication checks. This allows you to catch potentially fraudulent emails before they reach the recipient’s inbox, giving you a chance to investigate further.
5. Finally, Implement `p=reject`: The most stringent policy is `p=reject`. This instructs receiving mail servers to reject emails that fail authentication checks outright. This provides the strongest protection against spoofing and phishing attempts.
DMARC Policy Examples
The core of DMARC is its policy tag (`p=`). Here are the three main policy options:
* `p=none`: This is the initial and safest starting point. Receiving mail servers will report authentication results but will not take any action on failing emails. Example: `v=DMARC1; p=none; rua=mailto:dmarc_reports@yourdomain.com;`
* `p=quarantine`: Emails that fail authentication will be quarantined by receiving mail servers. Example: `v=DMARC1; p=quarantine; rua=mailto:dmarc_reports@yourdomain.com;`
* `p=reject`: Emails that fail authentication will be rejected by receiving mail servers. Example: `v=DMARC1; p=reject; rua=mailto:dmarc_reports@yourdomain.com;`
Remember to replace `dmarc_reports@yourdomain.com` with your actual reporting email address. The `rua` tag specifies where DMARC reports should be sent. Properly configuring these settings is crucial for effective DMARC implementation.
DMARC Reporting and Analysis: Domain Based Message Authentication Reporting Conformancedmarc
Understanding DMARC reports is crucial for maintaining email deliverability and protecting your brand’s reputation. These reports provide invaluable insights into how your email authentication is performing and highlight potential issues that need addressing. By analyzing these reports, you can proactively prevent email spoofing and improve the overall security of your email infrastructure.
Sample DMARC Report
A DMARC report, whether aggregate or forensic, contains a wealth of information. A simplified example of an aggregate report might include the following fields: `recordVersion`, `reportID`, `dateRange`, `orgName`, `email`, `policyPublished`, `adkim`, `aspf`, `p`, `sp`, `identifiers`, `authResults`, `count`, and `policy`. The `policyPublished` field shows your declared DMARC policy (e.g., `p=reject`). `adkim` and `aspf` indicate the results of DKIM and SPF checks respectively. The `count` field represents the number of emails that matched the specified selector. The `identifiers` field contains details about the sending email addresses. The `authResults` section shows authentication results (pass, fail, neutral) for each email. The `policy` field shows the action taken (quarantine or reject) based on the authentication results and your DMARC policy. This data allows you to pinpoint authentication failures and track their evolution over time. A detailed report would also include further granular information about the source IPs and domains.
DMARC Report Codes and Their Meanings
Understanding the codes within DMARC reports is key to effective analysis. The following table Artikels some common codes and their interpretations:
| Code | Meaning | SPF Result | DKIM Result |
|---|---|---|---|
| pass | Both SPF and DKIM checks passed. | pass | pass |
| fail | Either SPF or DKIM check failed. | fail | pass/fail |
| softfail | Authentication failed, but the email was not rejected. | fail/neutral | fail/neutral |
| neutral | Neither SPF nor DKIM checks could be performed. | neutral | neutral |
Interpreting DMARC Aggregate Reports
Aggregate reports provide a summarized overview of your email authentication performance over a specific period. By analyzing the `count` of `pass`, `fail`, `softfail`, and `neutral` results, you can quickly identify authentication issues. A high number of `fail` or `softfail` results indicates a need for investigation. For example, a large number of `fail` results might point to incorrect SPF or DKIM records, while a high `softfail` count might suggest the need to transition from `p=quarantine` to `p=reject` to strengthen your email security. Analyzing the `identifiers` field allows you to pinpoint specific sending domains or IPs causing the issues.
Aggregate vs. Forensic DMARC Reports
Aggregate reports offer a high-level summary of authentication results, providing valuable trends and overall performance. Forensic reports, on the other hand, delve into individual email messages that failed authentication. They provide detailed information about each email, including headers, body content (sometimes redacted), and the specific reasons for authentication failure. While aggregate reports are ideal for monitoring overall performance and identifying trends, forensic reports are invaluable for troubleshooting specific authentication failures and investigating potential email spoofing attempts. Think of aggregate reports as your monthly financial summary, while forensic reports are like the detailed transaction logs allowing you to trace every single expense.
DMARC Best Practices
Source: medium.com
Successfully implementing DMARC isn’t just about ticking boxes; it’s about securing your email communications and protecting your brand reputation. A well-structured DMARC policy, combined with consistent monitoring and proactive problem-solving, is key to reaping its full benefits. This section Artikels best practices to guide you through the process.
DMARC Implementation Checklist
A methodical approach is crucial for a smooth DMARC implementation. Failing to plan is planning to fail, and this checklist helps avoid common pitfalls.
- Publish a monitoring policy (v=DMARC1; p=none; rua=mailto:your.report@example.com; ruf=mailto:your.forensic@example.com; fo=1): Begin by collecting reports without enforcing any actions. This allows you to analyze your email sending infrastructure and identify potential issues before implementing a rejecting policy.
- Analyze DMARC reports: Carefully examine the reports to understand your email authentication landscape. Identify sources of unauthenticated email and investigate why they’re failing authentication. Pay close attention to the `sp` and `id` fields to pinpoint specific senders and their authentication status.
- Create a phased implementation plan: Don’t jump straight to `p=reject`. Gradually increase your DMARC policy’s strictness. Start with `p=none` for monitoring, then move to `p=quarantine`, and finally to `p=reject`. This phased approach minimizes the risk of legitimate emails being blocked.
- Align with SPF and DKIM: Ensure your SPF and DKIM records are correctly configured and aligned with your DMARC policy. Inconsistencies between these authentication methods can lead to false positives and email delivery issues.
- Regularly review and update your DMARC policy: Your email infrastructure might change over time. Regularly review your DMARC policy to ensure it accurately reflects your current sending practices and addresses any new authentication challenges.
- Maintain comprehensive documentation: Document your DMARC implementation process, including your policy settings, reporting addresses, and any troubleshooting steps taken. This documentation will be invaluable for future reference and maintenance.
Common DMARC Implementation Challenges and Solutions
Several hurdles can arise during DMARC implementation. Understanding these challenges and their solutions is critical for a successful rollout.
- Third-party senders: If you use third-party email marketing platforms or other services to send emails on your behalf, you need to coordinate with them to ensure they correctly implement SPF, DKIM, and align with your DMARC policy. Solutions include working directly with providers to configure their systems or using a dedicated email sending platform that integrates with DMARC.
- Legacy systems: Older email systems might not support modern authentication protocols. Solutions include upgrading these systems or finding alternative ways to authenticate emails sent from these sources. This may involve using a dedicated email relay that handles authentication.
- Incorrectly configured DNS records: Errors in your SPF, DKIM, or DMARC DNS records can lead to authentication failures. Solutions include carefully verifying the correctness of your records and using online tools to validate them.
- Misaligned authentication methods: Inconsistent configurations between SPF, DKIM, and DMARC can cause problems. Solutions include ensuring that all three mechanisms are correctly configured and aligned with each other. Thorough testing is essential.
DMARC Report Monitoring
Regularly monitoring DMARC reports is not optional; it’s essential. These reports provide valuable insights into your email authentication health and help you identify and resolve potential issues before they impact your email deliverability.
By analyzing these reports, you can pinpoint sources of unauthenticated email, understand why they’re failing authentication, and take corrective actions. Ignoring these reports can lead to significant email delivery problems and damage your brand reputation.
Handling DMARC Failures and Authentication Issues
Even with careful planning, DMARC failures can occur. A proactive approach to troubleshooting is crucial.
When encountering DMARC failures, first consult your DMARC reports to identify the source of the problem. This will often pinpoint specific senders or email services causing the issue. Then, depending on the source, you might need to adjust your DNS records, work with third-party providers, or implement additional authentication measures. For example, if a specific third-party email marketing platform is failing authentication, you may need to work with them to ensure they are properly configured to send emails on your behalf.
DMARC and Email Security
DMARC isn’t just another email authentication protocol; it’s the ultimate gatekeeper, significantly bolstering your email security posture and improving your sender reputation. By leveraging the information provided by SPF and DKIM, DMARC empowers email receivers to take decisive action against fraudulent emails, leading to better deliverability and a safer inbox experience for everyone.
DMARC’s impact on email security is multifaceted, improving several key areas. It doesn’t just authenticate emails; it dictates how receiving mail servers should handle emails that fail authentication. This proactive approach drastically reduces the success rate of malicious actors attempting to impersonate your domain.
DMARC Improves Email Deliverability and Reduces Spam
Implementing a robust DMARC policy directly translates to improved email deliverability. When your emails consistently pass DMARC checks, email providers are more likely to trust their authenticity, reducing the chances of them being flagged as spam or landing in junk folders. Conversely, a lack of DMARC implementation can lead to your legitimate emails being mistakenly categorized as spam, harming your sender reputation and potentially losing valuable communication with your audience. For example, a company with a poorly managed email infrastructure might see a significant drop in email open and click-through rates due to their emails being filtered out as spam, directly impacting marketing campaigns and customer communication. Implementing a strict DMARC policy can reverse this trend, resulting in improved engagement metrics.
DMARC’s Role in Combating Phishing and Spoofing Attacks
Phishing and spoofing attacks rely heavily on forged sender addresses to trick recipients into revealing sensitive information or executing malicious actions. DMARC acts as a powerful deterrent by verifying the authenticity of the sender’s domain. By enforcing a policy that rejects or quarantines emails failing authentication, DMARC significantly reduces the effectiveness of these attacks. Imagine a scenario where a phisher attempts to impersonate a major bank. With a properly configured DMARC policy in place, the bank’s email provider can block the fraudulent emails, preventing potential victims from falling prey to the scam. This significantly minimizes the risk of data breaches and financial losses.
The Relationship Between DMARC, SPF, and DKIM
DMARC works in conjunction with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to provide a comprehensive email authentication system. SPF verifies the sender’s IP address, while DKIM verifies the email’s integrity using digital signatures. DMARC acts as the enforcement mechanism, leveraging the results of SPF and DKIM checks to determine how receiving mail servers should handle emails that fail authentication. Think of it as a three-legged stool: SPF and DKIM provide the support, and DMARC provides the stability and direction. All three protocols working together offer a far more robust security system than any single protocol could achieve on its own.
Comparing DMARC’s Effectiveness with Other Email Security Measures
While other email security measures, such as spam filters and anti-virus software, play important roles, DMARC offers a unique advantage by focusing on authentication at the domain level. Spam filters rely on content analysis, which can be bypassed by sophisticated phishing emails. Anti-virus software focuses on detecting malicious attachments and code. DMARC, however, directly addresses the issue of email spoofing and impersonation, offering a more proactive and effective approach to combating email-based threats. The combined use of DMARC with other security measures creates a layered defense, providing maximum protection against a wide range of email-borne threats.
DMARC Implementation Scenarios

Source: trutech.com
Implementing DMARC isn’t a one-size-fits-all affair. The best approach depends heavily on your organization’s email infrastructure and sending practices. Understanding these nuances is key to successfully deploying and reaping the benefits of DMARC. Let’s explore some common scenarios and how to tailor your DMARC policy accordingly.
DMARC Implementation for Marketing Emails
Marketing emails often originate from third-party email service providers (ESPs) or marketing automation platforms. This introduces complexities to DMARC implementation, as you need to coordinate with these external vendors to align their sending practices with your DMARC policy. Failure to do so can lead to legitimate marketing emails being flagged as spam. A robust approach involves carefully selecting ESPs with strong authentication capabilities and clearly defining permitted sending domains and authentication methods in your DMARC record. Regular monitoring and communication with your ESP are crucial to ensure seamless integration and prevent email deliverability issues.
DMARC Implementation for Transactional Emails
Transactional emails, such as password resets or order confirmations, are generally sent directly from your organization’s servers. While this simplifies DMARC implementation compared to marketing emails, it still requires careful consideration of your sending infrastructure. Ensuring that all transactional email servers are properly configured with SPF and DKIM is essential. Your DMARC policy should reflect this, allowing only emails authenticated with SPF and DKIM from your authorized domains. Regular audits of your sending infrastructure can help identify and address any misconfigurations that could lead to DMARC failures.
DMARC Policy Design for a Hypothetical Organization, Domain based message authentication reporting conformancedmarc
Let’s consider “Acme Corp,” a hypothetical organization with multiple email sources: their internal mail servers (acme.com), a marketing ESP (sendgrid.com), and a third-party customer support platform (zendesk.com). Their DMARC policy might look like this:
`v=DMARC1; p=quarantine; rua=mailto:dmarc-reports@acme.com; ruf=mailto:dmarc-forensics@acme.com; sp=none; adkim=s; aspf=s;`
This policy uses `quarantine` for a phased approach, sending suspicious emails to the spam folder. `rua` specifies the address for aggregate reports, and `ruf` for forensic reports. `sp=none` indicates no action for subdomains. `adkim=s` and `aspf=s` require both DKIM and SPF alignment. `acme.com`, `sendgrid.com`, and `zendesk.com` would need to be properly configured for SPF and DKIM.
DMARC Implementation Case Study: Example Organization
* Organization: A large e-commerce company experienced a significant increase in phishing attempts impersonating their brand.
* Challenge: High volume of fraudulent emails damaging brand reputation and potentially exposing customer data.
* Solution: Implemented a DMARC policy starting with `p=none` for monitoring, then gradually moving to `p=quarantine` and finally `p=reject`.
* Results: A dramatic reduction in phishing emails, improved brand reputation, and increased customer trust. Analysis of DMARC reports identified and mitigated vulnerabilities in their email infrastructure. The company also saw an improvement in email deliverability due to the improved email authentication.
DMARC Policy Selection Decision-Making Process
This flowchart illustrates the decision-making process:
[Imagine a flowchart here. The flowchart would start with a decision box: “Is your organization ready for DMARC implementation?” A “Yes” branch would lead to a decision box: “What level of risk tolerance does your organization have?” This would branch into options like “High,” “Medium,” and “Low.” Each risk tolerance level would lead to a recommendation for a specific DMARC policy (e.g., `p=none`, `p=quarantine`, `p=reject`). A “No” branch would lead to a recommendation for further education and preparation.]
Advanced DMARC Techniques
DMARC, while seemingly straightforward, offers a wealth of advanced techniques to fine-tune your email authentication and protection. Mastering these techniques allows for granular control, improved deliverability, and a more robust defense against email spoofing. This section dives into some key areas to elevate your DMARC game.
Successfully implementing DMARC involves understanding its interaction with various email platforms and providers, managing subdomains effectively, and strategically migrating to stricter policies. Ignoring these nuances can lead to significant email deliverability issues and security vulnerabilities.
DMARC and Email Provider Compatibility
Different email providers (Gmail, Outlook, Yahoo, etc.) and platforms (e.g., marketing automation tools, CRM systems) handle DMARC differently. Some may be more lenient with policy enforcement, while others are stricter. Understanding these variations is crucial for a smooth implementation. For instance, while a provider might initially accept a `quarantine` policy, they may later require `reject` for better security. Thorough testing across multiple providers is vital before deploying a stricter DMARC policy. Consistent monitoring of DMARC reports from each provider will highlight potential discrepancies and inform adjustments to your overall strategy. This allows for proactive problem-solving, preventing unexpected email delivery disruptions.
DMARC Subdomain Management
Managing DMARC for subdomains requires a nuanced approach. A single DMARC record for your primary domain (`example.com`) won’t automatically protect subdomains like `mail.example.com` or `marketing.example.com`. Each subdomain needs its own DMARC record, or the parent domain’s record needs to be configured to encompass all subdomains. Failure to properly manage subdomains can leave significant gaps in your email authentication, exposing those subdomains to spoofing attempts. A common strategy is to apply a consistent DMARC policy across all subdomains, aligning with your overall email security strategy. Regular audits of subdomains and their associated DMARC records are crucial for maintaining comprehensive protection.
Migrating to a Stricter DMARC Policy
Migrating to a stricter DMARC policy (from `none` to `quarantine` to `reject`) should be a phased approach. A sudden shift to `reject` can lead to a significant drop in email deliverability as legitimate emails might be rejected. A gradual transition allows for monitoring and adjustment based on DMARC reports. Starting with `none` to analyze your email sending infrastructure, then moving to `quarantine` to observe the impact, before finally implementing `reject`, is a best practice. This methodical approach minimizes disruption and allows for identification and resolution of any underlying issues that might prevent legitimate emails from passing authentication. Careful analysis of reports at each stage is essential for a smooth and successful migration.
Impact of Misconfigured DMARC Records
Misconfigured DMARC records can have severe consequences, ranging from decreased email deliverability to complete email rejection. Errors in syntax, incorrect selectors, or mismatched policies can lead to legitimate emails being marked as spam or blocked altogether. Moreover, an improperly configured DMARC record might not provide any protection, effectively rendering your efforts useless. Regularly reviewing and validating your DMARC records is crucial to prevent such scenarios. Utilizing online DMARC record validators and seeking expert advice can help identify and rectify potential configuration issues before they negatively impact your email communication. The cost of remediation after a significant incident far outweighs the effort of proactive monitoring and validation.
End of Discussion
Source: webnersolutions.com
Mastering DMARC isn’t just about ticking boxes; it’s about building a robust email security posture that protects your brand, your reputation, and your customers. By understanding the nuances of DMARC, implementing it effectively, and diligently monitoring your reports, you’re not just improving email deliverability—you’re actively combating phishing, spoofing, and other malicious email activities. So, ditch the guesswork and embrace the power of DMARC. Your inbox (and your peace of mind) will thank you.