Hackers using sitting ducks attack to hijack domains 1 million domains vulnerable – Hackers using sitting duck attacks to hijack domains—a chilling reality affecting a staggering 1 million domains. This stealthy technique exploits vulnerabilities in domain registration and management, leaving businesses exposed to devastating financial and reputational damage. Imagine your website, your brand, your entire online presence, snatched away in the blink of an eye. This isn’t science fiction; it’s a very real threat impacting businesses of all sizes, from small startups to multinational corporations. We’ll dive deep into how these attacks work, who’s at risk, and what you can do to protect yourself.
The sitting duck attack leverages weaknesses in DNS security and human error. Hackers exploit these vulnerabilities to gain control of domain names, redirecting traffic to malicious sites or simply holding the domain hostage for ransom. The scale of this problem is immense, with a million domains potentially vulnerable. Understanding the mechanics of this attack, identifying potential vulnerabilities, and implementing robust security measures are crucial for survival in today’s digital landscape.
The Sitting Duck Attack
Source: securityonline.info
Domain hijacking is a serious threat, and one insidious method employed by malicious actors is the sitting duck attack. This isn’t a flashy, high-profile hack; instead, it relies on exploiting existing vulnerabilities and a lack of proactive security measures. Essentially, it’s about finding domains that are ripe for the taking, those that are “sitting ducks” waiting to be snatched. We’ll delve into the technical details of this attack vector, examining how it works and what can be done to prevent it.
Sitting Duck Attack Mechanics, Hackers using sitting ducks attack to hijack domains 1 million domains vulnerable
The sitting duck attack leverages weaknesses in domain registration and management practices. Hackers don’t actively break into systems; they identify domains with exploitable vulnerabilities, then exploit those weaknesses to gain control. This often involves targeting less secure registrars, exploiting weaknesses in DNS settings, or preying on human error within the domain management process. The entire process is often surprisingly simple, relying more on reconnaissance and exploiting existing vulnerabilities than on complex technical skills. The success of a sitting duck attack hinges on finding domains with lax security practices and readily available personal information that can be leveraged.
Vulnerabilities Exploited in Sitting Duck Attacks
Several vulnerabilities can make a domain a sitting duck. These include weak or easily guessable passwords for domain control panels, outdated or improperly configured DNS settings (allowing for zone transfers or other exploits), and a lack of two-factor authentication (2FA). Furthermore, phishing attacks targeting domain administrators can be incredibly effective in obtaining login credentials, opening the door for a sitting duck attack. Human error, such as clicking malicious links or falling for social engineering tactics, plays a significant role. The combination of technical vulnerabilities and human fallibility makes many domains vulnerable to this type of attack.
Step-by-Step Execution of a Sitting Duck Attack
A sitting duck attack typically unfolds in several stages. First, the attacker identifies potential targets using automated tools that scan for vulnerable domains. Next, they gather information about the target domain, including its registrar, DNS settings, and contact information. This information is used to formulate an attack strategy, which may involve exploiting weak passwords, phishing the domain administrator, or using other techniques to gain control of the domain. Finally, once control is gained, the attacker redirects the domain’s traffic to a malicious site or uses it for other nefarious purposes, such as distributing malware or engaging in phishing scams.
Stages of a Sitting Duck Attack
| Stage | Description | Tools/Techniques | Vulnerabilities Exploited |
|---|---|---|---|
| Target Identification | Identifying domains with potential vulnerabilities. | Automated scanning tools, WHOIS lookups | Weak security practices, outdated software |
| Information Gathering | Collecting information about the target domain and its administrator. | WHOIS lookups, social engineering, DNS enumeration | Publicly available information, lax privacy settings |
| Exploitation | Gaining control of the domain using the gathered information. | Brute-force attacks, phishing, exploiting DNS vulnerabilities | Weak passwords, outdated DNS configurations, human error |
| Domain Hijacking | Redirecting the domain’s traffic to a malicious site or using it for other malicious purposes. | DNS manipulation, registrar account takeover | Compromised credentials, weak registrar security |
Impact and Scale of the Vulnerability
One million domains vulnerable to a sitting duck attack? That’s not a typo. This isn’t some theoretical threat lurking in the dark corners of the internet; this is a real, present danger with potentially devastating consequences for businesses of all sizes. The sheer scale of this vulnerability demands immediate attention and proactive measures. The potential impact, both financially and reputationally, is staggering.
The consequences of a successful sitting duck attack on a single domain can range from minor inconvenience to catastrophic failure. Imagine a small e-commerce business losing access to its online store for even a few hours. Lost sales, frustrated customers, and damaged brand trust quickly add up. Now, multiply that impact by a million.
Financial and Reputational Damage
The financial repercussions of a widespread sitting duck attack are enormous. For a small business, a temporary website outage could mean lost revenue, potentially leading to business closure. Larger corporations face significantly higher stakes. Data breaches, service disruptions, and legal liabilities can cost millions, not to mention the plummeting stock prices and investor confidence. Reputational damage, equally critical, can be even harder to recover from. Loss of customer trust, negative media coverage, and damaged brand image can have long-term effects, impacting future growth and profitability. Consider the impact on a company like Amazon if even a fraction of its domains were compromised—the economic fallout would be catastrophic.
Hypothetical Scenario: A Large Corporation Under Attack
Let’s imagine GlobalCorp, a multinational conglomerate with hundreds of websites and online services, falls victim to a coordinated sitting duck attack. Simultaneously, their e-commerce platform, customer support portal, and internal communication systems go offline. The immediate impact is a complete disruption of business operations. Customers are unable to make purchases, employees cannot access critical information, and the company loses control of its online presence. Beyond the immediate financial losses, the reputational damage is immense. Negative news spreads rapidly, eroding customer confidence and potentially leading to legal action from affected parties. The recovery process would be long, expensive, and fraught with challenges, potentially impacting GlobalCorp’s market share and long-term viability. This scenario highlights the urgent need for robust security measures to prevent such widespread attacks.
Identifying Vulnerable Domains
With a million domains potentially vulnerable to sitting duck attacks, identifying those at risk is crucial for proactive security measures. This involves understanding the characteristics that make a domain a prime target and recognizing the warning signs. By employing a multi-faceted approach encompassing technical, administrative, and human factors, we can significantly improve our ability to pinpoint vulnerable domains and mitigate potential threats.
Identifying domains susceptible to sitting duck attacks requires a systematic approach. We need to look beyond simple technical vulnerabilities and consider the broader context of domain management and user behavior. This includes assessing the domain’s technical configuration, its administrative practices, and the overall security awareness of those managing it.
Technical Indicators of Vulnerability
Technical vulnerabilities often form the foundation of a successful sitting duck attack. These are weaknesses in the domain’s infrastructure or configuration that attackers can exploit. A lack of proper DNSSEC implementation, for instance, allows attackers to manipulate DNS records, redirecting traffic to malicious servers. Similarly, outdated or poorly configured web servers can create entry points for attackers to gain unauthorized access. Weak or default passwords for administrative accounts also significantly increase the risk. Furthermore, the absence of regular security audits and penetration testing leaves domains exposed to undiscovered vulnerabilities. These technical flaws provide the necessary footholds for attackers to execute their schemes.
Administrative Vulnerabilities
Administrative oversight and security practices play a crucial role in a domain’s susceptibility to attack. Poor password management, infrequent updates to software and security protocols, and a lack of employee training on cybersecurity best practices can all contribute to vulnerability. For example, an organization that uses the same password across multiple accounts presents a significant security risk. If one account is compromised, the attacker gains access to others. Similarly, a failure to implement multi-factor authentication leaves accounts easily accessible. Furthermore, a lack of regular security audits and incident response plans can significantly increase the likelihood of a successful attack. These administrative failures can provide attackers with easy pathways to compromise the domain.
Human-Related Factors
Human error often acts as the weakest link in the security chain. Phishing attacks, social engineering, and simple negligence can all lead to domain compromise. For example, an employee clicking on a malicious link in a phishing email could unintentionally grant an attacker access to the domain’s administrative account. Likewise, poor password hygiene, such as using easily guessable passwords, significantly increases the risk of unauthorized access. Insufficient security awareness training among employees can exacerbate these vulnerabilities, making them more likely to fall victim to social engineering tactics. The human element, therefore, represents a significant area of concern in the context of sitting duck attacks.
Mitigation Strategies and Best Practices
The chilling reality of one million vulnerable domains facing the Sitting Duck attack demands immediate and decisive action. Ignoring this vulnerability isn’t an option; proactive mitigation is the only responsible approach. This section Artikels crucial security measures, robust DNS practices, and essential tools to safeguard your digital assets. Remember, prevention is far cheaper and less stressful than dealing with the aftermath of a successful hijack.
Effective security measures go beyond simply hoping for the best. They require a layered approach, combining technical solutions with diligent operational practices. A single point of failure can unravel even the most sophisticated defenses, so redundancy and diversification are key. The goal is to make your domain a less attractive target, increasing the attacker’s effort and decreasing their likelihood of success.
Robust DNS Security Practices
Maintaining strong DNS security is paramount. A compromised DNS record is the gateway to a domain hijack. This involves implementing DNSSEC (Domain Name System Security Extensions) to digitally sign DNS records, verifying their authenticity and preventing manipulation. Furthermore, utilizing multi-factor authentication (MFA) for all accounts associated with domain management – registrars, hosting providers, and any other relevant services – is critical. Imagine the chaos if a single compromised password grants an attacker full control. This is not a hypothetical scenario; it’s a real threat that robust MFA effectively neutralizes. Finally, regularly reviewing and updating DNS records, ensuring no unauthorized changes have been made, is an essential hygiene practice.
Security Tools and Technologies
Several tools and technologies can significantly reduce the risk of a sitting duck attack. DNS monitoring services, for example, provide real-time alerts on any unauthorized changes to DNS records, enabling immediate response to suspicious activity. Intrusion detection and prevention systems (IDS/IPS) can detect and block malicious traffic attempting to exploit vulnerabilities. Web application firewalls (WAFs) add another layer of protection by filtering malicious requests targeting web applications. Consider these tools as your security arsenal, each playing a crucial role in bolstering your defenses. Investing in these technologies is an investment in the security and stability of your online presence.
Best Practices Checklist for Domain Registrars and Website Owners
A proactive approach is crucial. This checklist Artikels essential steps for domain registrars and website owners to fortify their domains against sitting duck attacks.
- Enable DNSSEC: This is the cornerstone of DNS security, verifying the authenticity of DNS records.
- Implement Multi-Factor Authentication (MFA): For all accounts related to domain management, drastically reducing the risk of unauthorized access.
- Regularly Audit DNS Records: Conduct frequent checks for unauthorized changes, ensuring the integrity of your domain’s configuration.
- Utilize DNS Monitoring Services: Receive immediate alerts of any suspicious activity, enabling prompt response.
- Employ Strong Passwords and Password Management: Utilize unique, complex passwords for all accounts, ideally managed with a robust password manager.
- Keep Software Updated: Regularly update all software and applications, patching known vulnerabilities that attackers could exploit.
- Educate Staff: Train employees on security best practices and phishing awareness to minimize the risk of social engineering attacks.
- Regular Security Audits: Conduct periodic security audits to identify and address potential vulnerabilities.
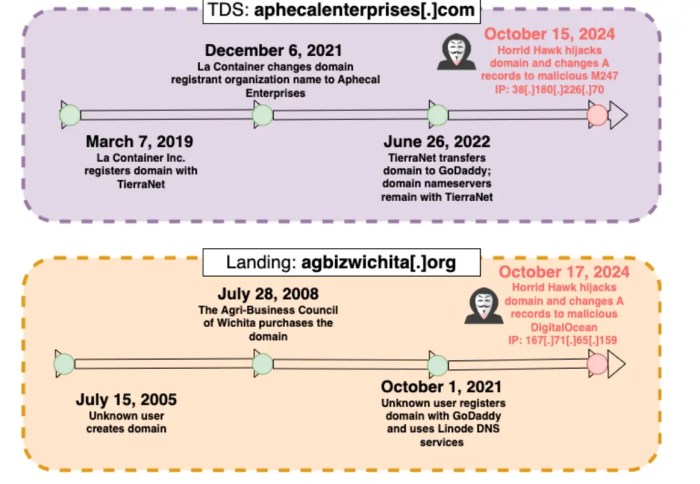
Case Studies of Successful Sitting Duck Attacks

Source: telegramevening.com
While precise details of successful sitting duck attacks are often kept confidential for security reasons, analyzing publicly available information reveals patterns and allows us to learn from past incidents. Understanding these cases helps organizations better protect themselves against this insidious form of domain hijacking. The lack of readily available specifics underscores the stealthy and effective nature of these attacks.
Successful sitting duck attacks often leverage a combination of social engineering, technical vulnerabilities, and a lack of robust security practices. Attackers exploit weaknesses in DNS systems, registrar vulnerabilities, or human error to gain control of a domain. The outcomes range from financial loss through fraudulent activities to reputational damage and disruption of services.
Analysis of a Hypothetical Case Study: The “CoffeeShop” Incident
Let’s consider a hypothetical scenario, “CoffeeShop,” to illustrate the mechanics of a successful sitting duck attack. Imagine a small coffee shop chain with a website. Their domain registrar, let’s call it “Registrar X,” suffered a security breach exposing customer data, including domain registration details. An attacker, exploiting this breach, gained access to the CoffeeShop domain’s administrative contact information. They then impersonated the legitimate contact, using sophisticated social engineering techniques (perhaps mimicking an email from Registrar X), to initiate a domain transfer request. Because CoffeeShop lacked strong multi-factor authentication and regular security audits, the transfer was approved. The attacker then redirected the domain’s DNS records to a malicious server, intercepting all website traffic and potentially stealing customer credit card information. The outcome was financial loss for CoffeeShop and reputational damage due to the data breach.
Comparison of Attack Tactics: Exploiting Registrar Vulnerabilities vs. Social Engineering
Some successful sitting duck attacks primarily exploit vulnerabilities within domain registrars, as seen in the hypothetical “CoffeeShop” case. Attackers might leverage known exploits or zero-day vulnerabilities to gain unauthorized access to domain control panels. In contrast, other attacks heavily rely on social engineering. This could involve phishing emails designed to trick domain administrators into revealing their credentials or approving fraudulent transfer requests. Both methods highlight the importance of robust security practices at both the registrar and client levels. A strong defense requires multiple layers of security to mitigate the risk posed by either approach.
Lessons Learned and Enhanced Security Measures
The key takeaway from analyzing successful sitting duck attacks (even hypothetical ones) is the crucial need for multi-layered security. This includes employing strong passwords, implementing multi-factor authentication (MFA) for all domain administrative accounts, regularly reviewing domain registration information for any unauthorized changes, and conducting security audits of both the domain registrar and internal systems. Educating employees about social engineering tactics and phishing attempts is equally vital. Regularly backing up domain registration data and having a robust incident response plan are also crucial for minimizing the impact of a successful attack. Finally, selecting a reputable and secure domain registrar with a proven track record is paramount.
The Role of Human Error in Sitting Duck Attacks
Let’s be honest, the internet’s a wild west. While sophisticated hacking techniques are terrifying, sometimes the easiest way in is through good old-fashioned human error. Sitting duck attacks, where hackers exploit vulnerable domain names, often hinge on this very thing: our mistakes. A million domains are vulnerable, and a significant portion of that vulnerability stems directly from the actions (or inactions) of the people managing them.
The reality is, even the most technically secure systems can be compromised if the human element is overlooked. A simple click on a malicious link, a misplaced password, or a failure to update software can open the door for a sitting duck attack. These aren’t necessarily signs of incompetence; they’re often the result of understandable lapses in judgment or a lack of awareness about the ever-evolving landscape of cyber threats. Think of it as leaving your front door unlocked – even the sturdiest lock won’t help if the key is left in the door.
Phishing Techniques Exploiting Human Error
Phishing attacks are a cornerstone of sitting duck attacks. Hackers craft convincing emails or messages mimicking legitimate organizations to trick individuals into revealing sensitive information like login credentials or security codes. These attacks often prey on our trust and urgency. Imagine an email appearing to be from your domain registrar, warning of an imminent account suspension unless you immediately click a link and update your information. This link, of course, leads to a fake login page designed to steal your credentials, effectively handing the attacker control of your domain. Another example involves a seemingly innocuous email with an attachment that, once opened, installs malware on the recipient’s computer, potentially giving the hacker access to the organization’s network and ultimately, the ability to seize control of their domain.
Improving Employee Awareness and Training
Addressing human error requires a multi-pronged approach focusing on proactive employee training and education.
- Regular Security Awareness Training: Implement mandatory, regular training sessions that cover various phishing techniques, including examples of real-world attacks and best practices for identifying and reporting suspicious emails or messages. Simulate phishing attacks to test employee vigilance and provide immediate feedback.
- Strong Password Policies and Multi-Factor Authentication (MFA): Enforce strong password policies and mandate the use of MFA for all accounts, significantly reducing the risk of unauthorized access even if credentials are compromised.
- Employee Education on Domain Security: Educate employees about the importance of domain security and their role in protecting company assets. This includes understanding the implications of compromised domains and the steps to take if they suspect a security breach.
- Reporting Mechanisms: Establish clear and accessible channels for employees to report suspicious activity without fear of retribution. This fosters a culture of security awareness and encourages proactive reporting.
- Up-to-Date Software and Security Patches: Regularly update all software and apply security patches promptly to minimize vulnerabilities that could be exploited by attackers.
Future Trends and Predictions
The Sitting Duck attack, while currently reliant on relatively simple techniques, is poised for significant evolution. As technology advances, so too will the sophistication and scale of these attacks, demanding proactive and adaptive security measures. The future of this threat landscape hinges on the interplay between attacker innovation and defender resilience.
The increasing reliance on automation and AI in both offensive and defensive cybersecurity will profoundly shape the future of Sitting Duck attacks. Attackers might leverage AI to identify vulnerable domains at an unprecedented scale, automating the entire process from target selection to domain hijacking. Conversely, defenders can use AI-powered systems to proactively identify and mitigate vulnerabilities before they’re exploited. This arms race will drive continuous innovation on both sides.
Evolving Attack Techniques
The basic Sitting Duck attack relies on exploiting weaknesses in domain registration and DNS management. However, future iterations could incorporate more advanced techniques, such as exploiting zero-day vulnerabilities in DNS servers or leveraging social engineering tactics to gain access to administrative accounts. We could see a rise in attacks targeting less-known TLDs (Top-Level Domains) or leveraging vulnerabilities in newer DNS protocols. Imagine a scenario where an attacker uses a sophisticated phishing campaign to trick a registrar employee into transferring a high-value domain. This would represent a significant escalation from current methods.
Impact of Evolving Technologies
The proliferation of IoT devices and the increasing adoption of cloud-based services will expand the attack surface for Sitting Duck attacks. The sheer number of interconnected devices and services creates numerous potential entry points for attackers. Furthermore, the complexity of managing these distributed systems increases the likelihood of human error, a key factor in successful Sitting Duck attacks. Consider the impact of a compromised IoT device within a company network gaining access to sensitive domain registration information. This could lead to a large-scale domain hijacking.
Future Scale and Impact
The future scale of Sitting Duck attacks is difficult to predict with certainty, but several factors suggest a potential increase in both frequency and impact. The increasing value of online assets, coupled with the growing sophistication of attack techniques, makes domains highly attractive targets. A successful attack on a major corporation’s domain could result in significant financial losses, reputational damage, and even legal repercussions. We might see coordinated attacks targeting multiple domains simultaneously, maximizing the impact and disrupting critical online services. For example, a coordinated attack targeting several financial institutions’ domains could trigger a significant market disruption.
Potential Future Attack Scenarios
A visual representation could depict a network map with numerous nodes representing various domains and services. Some nodes are highlighted in red, indicating successful Sitting Duck attacks. Arrows originating from a central, shadowy figure (representing the attacker) point towards the compromised nodes. These arrows could be labeled with different attack vectors, such as “phishing,” “exploited vulnerability,” or “social engineering.” The overall image would illustrate the interconnectedness of the internet and the potential for cascading effects from a successful Sitting Duck attack, emphasizing the wide-ranging impact of compromising even a single domain. The background could be a dark, ominous landscape to visually represent the threat.
Epilogue: Hackers Using Sitting Ducks Attack To Hijack Domains 1 Million Domains Vulnerable

Source: cnbcfm.com
The sitting duck attack isn’t just a technical vulnerability; it’s a wake-up call for businesses to prioritize robust cybersecurity practices. While the sheer number of vulnerable domains is alarming, understanding the attack vector, identifying your own vulnerabilities, and implementing effective mitigation strategies can significantly reduce your risk. Ignoring this threat isn’t an option; proactive security measures are the only way to safeguard your online presence and protect your business from the devastating consequences of a successful attack. The digital world is a battlefield, and knowing your enemy is the first step to victory.





