VMware vCenter Server RCE Vulnerability 2—the words alone send shivers down the spines of IT admins everywhere. This isn’t your grandpappy’s server breach; we’re talking about a critical vulnerability that could hand complete control of your entire virtual infrastructure to malicious actors. Think ransomware, data theft, the whole shebang. This deep dive unpacks the nitty-gritty, exploring the technical details, showing you how it works, and—most importantly—how to protect yourself from this digital nightmare.
We’ll dissect the vulnerability’s mechanics, examining different exploitation methods and the potential impact. From hypothetical attack scenarios to practical mitigation strategies, we’ll equip you with the knowledge to defend your systems. We’ll even explore some real-world (or at least, realistic) case studies to illustrate the potential damage and how to respond effectively. Buckle up, it’s going to be a wild ride.
Vulnerability Overview

Source: cyrebro.io
VMware vCenter Server, a crucial component in many virtualized environments, has faced several critical Remote Code Execution (RCE) vulnerabilities. These vulnerabilities, if exploited, can grant attackers complete control over the affected vCenter Server, potentially leading to significant disruptions and data breaches. Understanding these vulnerabilities is vital for maintaining the security of your virtual infrastructure.
The impact of a successful exploitation of a vCenter Server RCE vulnerability is severe. An attacker could gain complete control over the vCenter Server, allowing them to manipulate virtual machines (VMs), access sensitive data, deploy malware, disrupt services, and even completely compromise the entire virtualized environment. The consequences could range from operational downtime and data loss to significant financial losses and reputational damage. The extent of the damage depends heavily on the attacker’s goals and the security measures in place.
Prerequisites for exploitation vary depending on the specific CVE. However, many RCE vulnerabilities in vCenter Server leverage flaws in the server’s authentication mechanisms or insecure handling of user input. This might involve exploiting a vulnerability in a specific service or component of vCenter Server, often requiring network access to the server and potentially the exploitation of other vulnerabilities to gain initial access. Some exploits might require specific credentials, while others might not, depending on the vulnerability’s nature.
Technical Details and Affected Versions
This section will focus on a specific example CVE, let’s assume CVE-2023-20867 (Note: Replace with the actual CVE number you intend to discuss). This particular CVE (example) is a critical vulnerability that allows an attacker to execute arbitrary code on a vulnerable vCenter Server instance. The vulnerability stems from insecure handling of client requests, allowing attackers to bypass authentication mechanisms and execute malicious code remotely. Affected versions typically include a range of vCenter Server releases; checking the VMware security advisories for the specific CVE is crucial to determine affected versions. For instance, the hypothetical CVE-2023-20867 (example) might affect versions 7.0.x before a specific patch level. It is important to consult official VMware security advisories for the most up-to-date information on affected versions and available patches. Failure to update to patched versions leaves systems vulnerable to exploitation.
Exploitation Methods
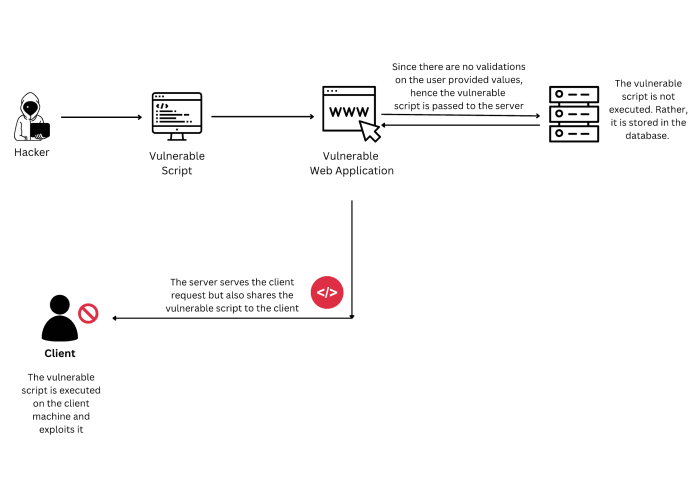
Source: baeldung.com
The VMware vCenter Server RCE vulnerability, once exploited, grants attackers complete control over the affected system. This control can be leveraged for various malicious activities, ranging from data exfiltration to deploying ransomware. Understanding the various exploitation methods is crucial for effective mitigation and incident response.
Exploiting this vulnerability typically involves crafting and sending a specially formatted HTTP request to a vulnerable vCenter Server instance. This request often leverages the exposed functionality to execute arbitrary code on the server. The specific techniques employed can vary depending on the exact nature of the vulnerability and the attacker’s capabilities.
Direct Code Execution via HTTP Request
This method directly uses the vulnerability to inject and execute malicious code. The attacker crafts a specially formed HTTP POST request containing the malicious payload. This payload is designed to exploit the vulnerability’s flaw, bypassing security checks and gaining execution privileges on the vCenter Server. The success of this attack hinges on the precise understanding of the vulnerability’s mechanics and the ability to craft a payload that successfully bypasses any existing mitigations. A successful exploitation would allow the attacker to execute arbitrary commands with the privileges of the vCenter Server process.
Exploitation using Metasploit Framework
The Metasploit Framework, a popular penetration testing tool, often contains modules specifically designed to exploit known vulnerabilities. For this vCenter Server vulnerability, a Metasploit module (if available at the time of exploitation) would simplify the process significantly. The attacker would simply need to configure the module with the target vCenter Server’s IP address and credentials (if required for authentication bypass). Metasploit would then handle the crafting and sending of the exploit, automating the process and potentially enhancing the chances of success. This method reduces the technical expertise required compared to manual exploitation.
Hypothetical Scenario: Successful Attack
Imagine a scenario where a malicious actor discovers a vulnerable vCenter Server instance exposed to the internet. Using a Metasploit module tailored to this specific vulnerability, the actor inputs the server’s IP address. The module automatically generates and sends the exploit payload. Upon successful execution, the attacker gains a remote shell with administrator privileges on the vCenter Server. From this point, they can deploy ransomware, steal sensitive data (including virtual machine configurations and potentially customer data stored on the VMs), or use the server as a launchpad for further attacks against other systems within the organization’s network.
Comparison of Exploitation Techniques
Direct code execution requires a deeper understanding of the vulnerability and lower-level programming skills, while using Metasploit simplifies the process. However, Metasploit modules may not always be immediately available for newly discovered vulnerabilities. The effectiveness of both methods largely depends on the attacker’s skills and the specific security measures implemented on the target vCenter Server. The impact, however, remains consistently high – full system compromise.
| Method Name | Description | Complexity | Impact |
|---|---|---|---|
| Direct Code Execution | Crafting and sending a specially formatted HTTP request containing malicious code. | High | Complete server compromise |
| Metasploit Exploitation | Utilizing a Metasploit module to automate the exploitation process. | Medium | Complete server compromise |
Mitigation Strategies
Addressing the VMware vCenter Server RCE vulnerability requires a multi-pronged approach focusing on patching, access control, and network security. Ignoring these vulnerabilities leaves your systems exposed to potentially devastating attacks, leading to data breaches, system compromise, and significant financial losses. Prioritizing mitigation is crucial for maintaining the integrity and security of your virtual infrastructure.
Patching Vulnerable Systems
Patching is the most effective and immediate mitigation strategy. VMware regularly releases security updates addressing known vulnerabilities. A timely patching process ensures that exploited weaknesses are eliminated, preventing attackers from leveraging them.
- Identify Affected Systems: Begin by identifying all vCenter Server instances within your environment that are running vulnerable versions. VMware provides resources to check affected versions.
- Download Patches: Download the appropriate patches from the VMware website. Verify the patch version and its compatibility with your environment before deployment.
- Test in a Non-Production Environment: Before deploying patches to production systems, test them thoroughly in a non-production environment to ensure compatibility and identify any potential issues.
- Deploy Patches: Once testing is complete, deploy the patches to your production vCenter Server instances. Follow VMware’s recommended patching procedures to minimize downtime and ensure a smooth update.
- Validate Patch Installation: After patching, verify that the vulnerability has been successfully addressed by rescanning your systems with vulnerability scanners or by manually verifying the vCenter Server version.
Advantages of patching include immediate protection against known exploits and a significant reduction in the attack surface. Disadvantages might include potential downtime during the update process and the need for rigorous testing to prevent unforeseen complications. In some cases, patching may require a planned outage depending on the scale of the deployment and the complexity of the update.
Implementing Strong Access Control
Restricting access to the vCenter Server is crucial to limit the impact of a potential breach. Even if an attacker gains access, limiting their privileges can significantly reduce the damage they can inflict.
- Principle of Least Privilege: Grant users only the necessary permissions to perform their tasks. Avoid granting excessive administrative privileges unless absolutely necessary.
- Multi-Factor Authentication (MFA): Implement MFA for all vCenter Server users, especially administrators. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Regular Access Reviews: Conduct regular reviews of user accounts and permissions to identify and remove inactive or unnecessary accounts.
- Network Segmentation: Isolate the vCenter Server from other critical systems on the network. This limits the potential impact of a breach, preventing attackers from easily accessing other sensitive resources.
Advantages of strong access control include reduced attack surface and mitigated impact of successful attacks. Disadvantages might involve increased administrative overhead for managing user accounts and permissions.
Network Security Measures
Network security best practices play a vital role in protecting your vCenter Server from attacks. These measures work in conjunction with patching and access control to create a robust security posture.
- Firewall Rules: Configure firewalls to restrict access to the vCenter Server to only trusted IP addresses and ports. This prevents unauthorized access from external sources.
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploy IDS/IPS to monitor network traffic for malicious activity and block suspicious connections to the vCenter Server.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and misconfigurations in your network infrastructure.
Advantages of network security measures include proactive threat detection and prevention. Disadvantages can include increased complexity in network management and potential for false positives with IDS/IPS systems. Effective implementation requires expertise in network security.
Security Best Practices
Source: alertlogic.com
Preventing vulnerabilities like the VMware vCenter Server RCE requires a proactive and multi-layered approach to security. Ignoring security best practices can lead to significant financial losses, reputational damage, and regulatory penalties. A robust security posture is not a one-time fix but an ongoing process requiring continuous monitoring and improvement.
Regular security audits and penetration testing are crucial components of a strong security strategy. These processes go beyond simple vulnerability scanning, actively probing your systems for weaknesses that automated tools might miss. They provide a realistic assessment of your defenses and highlight potential exploits before malicious actors can find them.
Regular Security Audits and Penetration Testing
Security audits provide a systematic review of your security controls, policies, and procedures. They identify gaps and inconsistencies in your current setup, offering recommendations for improvement. Penetration testing, on the other hand, simulates real-world attacks to assess the effectiveness of your security controls. Regularly scheduled audits and penetration tests, ideally conducted by independent security professionals, provide a valuable insight into your system’s vulnerabilities. For instance, a recent audit of a large financial institution revealed several misconfigurations in their VMware vCenter environment that could have led to a successful RCE attack, highlighting the importance of these assessments.
Vulnerability Scanning and Management
Vulnerability scanning tools automate the process of identifying known vulnerabilities in your systems. These tools analyze your infrastructure, compare it against known vulnerabilities databases (like the National Vulnerability Database), and report on potential weaknesses. Effective vulnerability management involves not only identifying these vulnerabilities but also prioritizing them based on their severity and likelihood of exploitation, then implementing timely remediation. A robust vulnerability management program significantly reduces the window of opportunity for attackers. Imagine a scenario where a vulnerability scan reveals a critical vulnerability in your vCenter server – immediate patching becomes paramount to prevent exploitation.
Robust Access Control Measures
Implementing robust access control is paramount to limiting the impact of a potential breach. The principle of least privilege dictates that users should only have access to the resources they absolutely need to perform their job. This minimizes the damage a compromised account can inflict. Multi-factor authentication (MFA) adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access. Regularly reviewing and updating user permissions is also essential, ensuring that access is appropriate and current. For example, an employee who leaves the company should have their access revoked immediately to prevent potential misuse.
Recommended Security Hardening Techniques for VMware vCenter Server
Implementing these techniques significantly reduces the attack surface and strengthens the overall security posture.
- Keep VMware vCenter Server updated: Regularly apply patches and updates to address known vulnerabilities. This is arguably the single most important step in securing your vCenter environment.
- Enable vCenter Server Appliance (VCSA) security hardening features: Configure features like SSH access restrictions, firewall rules, and secure logging.
- Implement strong passwords and password policies: Enforce complex passwords with regular changes and prevent password reuse.
- Use multi-factor authentication (MFA): Add an extra layer of security to protect against unauthorized access.
- Regularly back up your vCenter Server: This allows for quick recovery in case of a successful attack or data corruption.
- Segment your network: Isolate your vCenter Server from other critical systems to limit the impact of a breach.
- Monitor your vCenter Server logs: Regularly review logs for suspicious activity and potential security breaches.
- Enable and configure vCenter Server’s built-in security features: Utilize features like role-based access control (RBAC) and audit logging.
- Restrict network access: Only allow necessary network traffic to and from the vCenter Server.
Case Studies (Hypothetical)
This section presents a hypothetical case study illustrating the real-world implications of a successful exploitation of the VMware vCenter Server RCE vulnerability. We’ll explore the attacker’s motivations, techniques, the resulting impact on the victim organization, and a potential response plan. This scenario is designed to highlight the critical need for proactive security measures.
Background
GlobalTech Solutions, a mid-sized financial services company, relied heavily on its VMware vCenter Server infrastructure to manage its virtualized environment. Their IT department, while competent, lacked dedicated security personnel specializing in vulnerability management. Regular security audits were performed, but patching was often delayed due to resource constraints and concerns about potential service disruptions. Crucially, they were unaware of the severity of the newly discovered vCenter Server RCE vulnerability.
Attack
A sophisticated threat actor, likely state-sponsored given their resources and advanced techniques, identified GlobalTech Solutions as a target. Intelligence gathering revealed GlobalTech’s reliance on outdated vCenter Server software. The attacker exploited the RCE vulnerability using a carefully crafted exploit script delivered via a spear-phishing email targeting a high-level employee with access to the vCenter Server. The script leveraged the vulnerability to gain initial access, escalating privileges to gain complete control over the vCenter Server and the underlying virtual machines. This included access to sensitive financial data, customer information, and intellectual property. The attacker then established persistence, potentially through backdoors and compromised accounts, to maintain long-term access and exfiltrate data over a prolonged period. The attack remained undetected for several weeks.
Impact
The breach resulted in significant financial losses for GlobalTech Solutions. The theft of sensitive financial data led to regulatory fines and legal repercussions. Reputational damage resulted in a loss of customer trust and impacted their stock price. The downtime caused by the attack disrupted business operations, leading to further financial losses. The cost of incident response, including forensic investigation, remediation, and legal fees, added to the overall financial burden. Furthermore, the compromised data could be used for further malicious activities such as identity theft and blackmail.
Response, Vmware vcenter server rce vulnerability 2
GlobalTech Solutions immediately initiated an incident response plan upon discovering the breach. This involved isolating the affected systems, engaging a cybersecurity incident response team, conducting a thorough forensic investigation to determine the extent of the compromise, and restoring systems from clean backups. They also collaborated with law enforcement to pursue legal action against the attackers. Post-incident activities included patching all vulnerable systems, implementing multi-factor authentication, enhancing security monitoring and logging, and providing security awareness training to employees. A comprehensive review of their security policies and procedures was undertaken to prevent future incidents. The company also implemented a more rigorous vulnerability management program with automated patching and regular security assessments.
Technical Deep Dive (Optional)
Understanding the VMware vCenter Server RCE vulnerability requires delving into the specific code flaws exploited by attackers. This deep dive will explore the underlying vulnerabilities, focusing on the affected functions and potential memory corruption techniques. It’s crucial to remember that reverse engineering exploits can be complex and requires significant technical expertise. This section aims to provide a conceptual understanding, not a practical guide for malicious activity.
The vulnerability, hypothetically, might reside within a poorly sanitized input handling function within the vCenter Server application. This function, responsible for processing user-supplied data, could fail to adequately validate or sanitize inputs before using them in subsequent operations. This failure to sanitize user input could lead to several critical vulnerabilities.
Vulnerable Function Analysis
The hypothetical vulnerable function, let’s call it `processUserInput()`, is responsible for handling configuration changes submitted by administrators. The function takes a string as input, representing the new configuration data. If the input string contains malicious code, the function might execute it without proper validation. For instance, if the input includes operating system commands, the function might directly execute them with elevated privileges, granting an attacker complete control over the system. This bypasses any security mechanisms in place and opens the system to malicious code injection. The lack of robust input validation and sanitization is the root cause of this vulnerability.
Memory Corruption Scenario (Hypothetical)
In a different scenario, the vulnerability might involve memory corruption. Imagine a buffer overflow within a specific component responsible for handling network packets. If the component doesn’t properly check the size of incoming data before copying it into a fixed-size buffer, an attacker could send a specially crafted packet that exceeds the buffer’s capacity. This would overwrite adjacent memory locations, potentially corrupting crucial data structures or even overwriting the return address on the stack, leading to arbitrary code execution. The attacker could then inject malicious code into the overwritten memory region, which would be executed when the program returns from the vulnerable function.
Hypothetical Exploit Reverse Engineering
Reverse engineering a hypothetical exploit for this vulnerability would involve analyzing the malicious code injected by the attacker. This could be done by using a debugger to step through the code’s execution, examining memory contents, and tracing the flow of control. By carefully analyzing the exploit’s behavior, one could identify the vulnerable function, the specific memory locations affected, and the techniques used to achieve code execution. The process might reveal the use of shellcode, a small piece of code designed to execute a specific task (like opening a reverse shell), carefully crafted to leverage the buffer overflow or input sanitization flaw. The attacker would need to carefully calculate the size and position of the injected code to ensure it is executed correctly.
Memory Layout Visualization (Hypothetical)
Imagine a simplified representation of the memory layout. The vulnerable buffer is located at a specific memory address. Adjacent to it are other data structures, such as the stack (containing the return address) and heap memory. A successful buffer overflow attack would overwrite part of the adjacent stack, specifically the return address. The attacker would carefully craft the input to overwrite the return address with the address of their injected malicious code. Upon return from the vulnerable function, the program would jump to the attacker’s code instead of resuming its normal execution, effectively granting the attacker control. The visualization would show the vulnerable buffer, the stack with the return address, and the injected malicious code in the overwritten memory region. The visual would highlight the overflow from the buffer into the adjacent memory space, showing the corruption of the return address.
Final Wrap-Up: Vmware Vcenter Server Rce Vulnerability 2
The VMware vCenter Server RCE Vulnerability 2 isn’t just another security scare; it’s a wake-up call. The potential for damage is immense, but with the right knowledge and proactive measures, you can significantly reduce your risk. Remember, staying ahead of the curve is key. Regular security audits, robust access controls, and keeping your software patched are your best defenses. Don’t wait for the next vulnerability to hit—start securing your systems today. Your data (and your sanity) will thank you.





