BrazenBamboo APT FortiClient zero day: The cybersecurity world just got a whole lot shadier. This sophisticated threat actor has exploited critical vulnerabilities in FortiClient, leaving a trail of compromised systems in its wake. We’re diving deep into the technical nitty-gritty, exploring the attack methods, impact, and ultimately, how to defend against this stealthy threat. Get ready to level up your cybersecurity game.
From initial access vectors to data exfiltration techniques, we’ll dissect BrazenBamboo’s tactics, techniques, and procedures (TTPs) with a laser focus. We’ll examine the specific vulnerabilities targeted, the affected FortiClient versions, and the potential impact on various organizations – from financial institutions to critical infrastructure. This isn’t just another security alert; it’s a deep dive into the underbelly of modern cyber warfare.
BrazenBamboo APT and FortiClient Vulnerabilities
The BrazenBamboo advanced persistent threat (APT) group has been linked to sophisticated attacks leveraging critical vulnerabilities in Fortinet’s FortiClient endpoint protection software. These attacks highlight the serious consequences of unpatched software and the increasing sophistication of modern cyber threats. Understanding the vulnerabilities exploited and the techniques employed by BrazenBamboo is crucial for organizations to strengthen their security posture.
BrazenBamboo’s attacks demonstrate a concerning trend: the exploitation of seemingly minor vulnerabilities to achieve significant breaches. The group’s success underscores the importance of proactive security measures, including regular patching and vulnerability scanning, to mitigate the risk of similar attacks.
FortiClient Vulnerabilities Exploited by BrazenBamboo
The precise details of all vulnerabilities exploited by BrazenBamboo remain partially undisclosed for security reasons. However, publicly available information reveals several critical flaws in FortiClient that have been leveraged in these attacks. These vulnerabilities often reside in the FortiClient’s VPN and SSL components, allowing attackers to gain unauthorized access to systems and networks.
Technical Mechanisms Used by BrazenBamboo
BrazenBamboo’s attacks are characterized by their multi-stage approach. Initial compromise often involves exploiting a vulnerability in FortiClient to gain initial access. Once inside, the attackers use a variety of techniques, including lateral movement and data exfiltration, to achieve their objectives. This might involve deploying malicious payloads, establishing persistent backdoors, and stealing sensitive information. The precise methods used can vary depending on the target and the specific vulnerability exploited. Sophisticated techniques like code injection and privilege escalation are commonly employed.
Impact of Vulnerabilities Across FortiClient Versions
The impact of these vulnerabilities varies depending on the specific FortiClient version. Older versions are generally more susceptible due to the lack of security patches addressing the known flaws. Newer versions, while not entirely immune, often include mitigations that reduce the likelihood of successful exploitation. For instance, a vulnerability in an older version might allow for complete system compromise, while the same vulnerability in a newer version might only allow limited access. Prompt patching is therefore crucial to minimize risk.
Summary of Exploited Vulnerabilities
| Vulnerability ID | Description | Affected Versions | Exploit Method |
|---|---|---|---|
| (Example: CVE-XXXX-YYYY) | (Example: Buffer overflow in VPN module) | (Example: FortiClient 6.x, 7.x) | (Example: Remote code execution via crafted VPN connection) |
| (Example: CVE-ZZZZ-WWWW) | (Example: Improper input validation in SSL handling) | (Example: FortiClient 5.x, 6.x) | (Example: Malicious certificate leading to privilege escalation) |
| (Note: Specific vulnerability details are often kept confidential to prevent further exploitation.) |
BrazenBamboo’s Tactics, Techniques, and Procedures (TTPs)
BrazenBamboo, a sophisticated and persistent threat actor, employs a range of tactics, techniques, and procedures (TTPs) to achieve their objectives. Their operations are characterized by stealth, meticulous planning, and a focus on long-term access to targeted systems. Understanding their methods is crucial for effective defense. This section delves into the specific techniques used by BrazenBamboo during their campaigns.
BrazenBamboo’s attacks are multi-staged and rely on a combination of exploiting vulnerabilities, social engineering, and custom-built malware. Their operations demonstrate a high level of technical expertise and a clear understanding of their targets’ networks and security postures. The group’s adaptability is also noteworthy, as they constantly refine their techniques to evade detection and maintain persistence.
Initial Access Vectors
BrazenBamboo’s initial access is often achieved through spear-phishing campaigns targeting high-value individuals within their chosen organizations. These emails typically contain malicious attachments or links leading to compromised websites hosting malware. The group has also been observed exploiting known vulnerabilities in software applications, particularly those with a wide user base and less frequent patching cycles. Another notable vector is the use of compromised third-party vendors or supply chain attacks. In essence, they exploit vulnerabilities in both software and human behavior.
Lateral Movement Techniques
Once initial access is gained, BrazenBamboo employs several techniques for lateral movement within the compromised network. These include using stolen credentials to access other systems, leveraging legitimate administrative tools for unauthorized access, and employing custom-built tools to move between systems undetected. They frequently utilize techniques that blend into normal network activity, making detection challenging. For example, they might use tools that mimic standard system processes, thereby avoiding detection by security systems. The exploitation of weak or default passwords is also a common tactic.
Stages of a Typical BrazenBamboo Attack
Understanding the phases of a typical BrazenBamboo attack is vital for effective mitigation. Here’s a breakdown of the process:
The following list Artikels the typical stages of a BrazenBamboo attack, highlighting the key actions and techniques employed at each step.
- Initial Compromise: Spear-phishing emails, exploit kits, or supply chain attacks are used to gain initial access to the target network.
- Reconnaissance: The attackers conduct thorough reconnaissance to map the network infrastructure, identify high-value targets, and determine the most effective lateral movement strategies.
- Lateral Movement: Stolen credentials, compromised accounts, or custom-built tools are used to move laterally within the network, gaining access to sensitive data and systems.
- Data Exfiltration: Sensitive data, including intellectual property, financial information, and other confidential documents, is exfiltrated from the compromised network using various techniques such as command-and-control (C2) servers and encrypted communication channels.
- Persistence: The attackers establish persistence mechanisms to maintain long-term access to the compromised systems, ensuring continued access and control.
Impact and Target Profiles of BrazenBamboo Attacks

Source: comodo.com
BrazenBamboo’s operations reveal a targeted approach, focusing on organizations holding valuable intellectual property and sensitive data. Understanding their impact and preferred targets is crucial for effective cybersecurity defense strategies. The group’s sophisticated techniques and persistent operations pose significant risks across various sectors.
BrazenBamboo’s attacks primarily target organizations in the finance, technology, and government sectors. These sectors often possess lucrative financial assets, cutting-edge technologies, and sensitive geopolitical information, all highly valuable to state-sponsored actors like BrazenBamboo. The group displays a preference for organizations with weak cybersecurity postures, making them easier targets for initial compromise and subsequent data exfiltration.
Targeted Organizations and Sectors, Brazenbamboo apt forticlient zero day
The most frequent targets of BrazenBamboo are financial institutions, technology companies, and government agencies, particularly those involved in defense or national security. These organizations often possess valuable data, intellectual property, and financial resources, making them attractive targets for espionage and financial gain. The group’s success hinges on exploiting vulnerabilities within these organizations’ networks and systems.
Impact of a Successful BrazenBamboo Attack
A successful BrazenBamboo attack can have devastating consequences for a targeted organization. The immediate impact might include data breaches leading to the loss of sensitive financial information, intellectual property theft, and disruption of critical operations. The long-term consequences can be even more severe, potentially including reputational damage, legal liabilities, financial losses from fraud, and significant costs associated with incident response and remediation efforts. In the case of government agencies, a successful attack could compromise national security and lead to the exposure of classified information.
Data Exfiltration Methods
BrazenBamboo employs a variety of sophisticated techniques for data exfiltration. These methods often involve the use of covert channels, encrypted communication protocols, and data compression techniques to evade detection. They may leverage compromised accounts, legitimate services, or custom tools to transfer stolen data. The group demonstrates adaptability, switching between methods to avoid detection and maintain persistence within compromised networks. For example, they might use compromised email accounts to send stolen data in small batches over extended periods, making detection more difficult.
Hypothetical Scenario: BrazenBamboo Attack on a Financial Institution
Imagine a scenario where BrazenBamboo targets a major financial institution. The attack begins with a phishing email containing a malicious attachment, exploiting a vulnerability in the institution’s FortiClient software. Once inside the network, the attackers move laterally, gaining access to sensitive databases containing customer financial information, transaction records, and internal financial models. They then use a custom-built tool to exfiltrate this data, encrypting it and sending it to a command-and-control server located overseas. The consequences would be catastrophic: massive financial losses due to fraud, reputational damage leading to customer loss and investor distrust, significant regulatory fines, and the potential exposure of sensitive personal information, resulting in legal ramifications. The institution would face immense costs related to incident response, remediation, and legal battles.
Mitigation and Defense Strategies Against BrazenBamboo Attacks
BrazenBamboo’s sophisticated techniques demand a multi-layered defense strategy. Ignoring even one aspect of security can leave your organization vulnerable to this persistent threat. Proactive measures and a robust security posture are crucial to effectively mitigate the risks associated with BrazenBamboo attacks. This section Artikels key strategies and best practices to enhance your organization’s resilience.
Effective mitigation requires a combination of technical controls, security awareness training, and robust incident response planning. A layered approach ensures that even if one layer fails, others are in place to detect and prevent successful compromise.
Endpoint Security Hardening
Strengthening endpoint security is paramount. This involves implementing robust antivirus and endpoint detection and response (EDR) solutions, regularly updating software and operating systems, and employing strong password policies. Disabling unnecessary services and applications minimizes the attack surface. Regular security audits and vulnerability assessments should be conducted to identify and remediate potential weaknesses. For example, ensuring that all endpoints are patched against known vulnerabilities, including those exploited by BrazenBamboo, is critical. Regularly scanning for malware and employing behavioral analysis tools can help detect and respond to suspicious activities.
Network Security Controls
Network segmentation limits the impact of a successful breach. Implementing firewalls with strict access control lists (ACLs) and intrusion detection/prevention systems (IDS/IPS) capable of detecting malicious network traffic patterns is crucial. These systems should be configured to monitor for known BrazenBamboo attack signatures and suspicious activities, such as unusual outbound connections or attempts to exfiltrate data. Consider deploying a next-generation firewall (NGFW) with advanced threat protection capabilities, including sandboxing and machine learning-based threat detection. For instance, an NGFW could analyze network traffic for anomalies that indicate the presence of malware or unauthorized access attempts, such as those associated with BrazenBamboo’s tactics.
Vulnerability Management and Patching
Regular patching and vulnerability management are fundamental to reducing the attack surface. Organizations must maintain an up-to-date inventory of software and hardware assets, and promptly apply security patches and updates. This includes not only operating systems and applications but also firmware for network devices and other infrastructure components. Automated vulnerability scanning tools can help identify vulnerabilities and prioritize patching efforts. Consider implementing a robust patch management system that automates the process of identifying, testing, and deploying security updates across the organization’s infrastructure. Failing to address vulnerabilities promptly can significantly increase the likelihood of a successful attack. The FortiClient vulnerability exploited by BrazenBamboo highlights the criticality of timely patching.
Security Awareness Training
Educating employees about social engineering tactics and phishing scams is vital. BrazenBamboo, like many APTs, often employs social engineering to gain initial access to target systems. Regular security awareness training can help employees identify and avoid phishing emails, malicious links, and other social engineering attempts. Training should cover topics such as identifying phishing emails, practicing safe browsing habits, and recognizing signs of social engineering attacks. Simulated phishing campaigns can also be used to test employee awareness and identify areas for improvement. Investing in comprehensive security awareness training is crucial for mitigating the risk of human error, which often plays a critical role in successful attacks.
Incident Response Planning
A well-defined incident response plan is essential for containing and mitigating the impact of a successful attack. This plan should Artikel procedures for identifying, containing, eradicating, and recovering from security incidents. Regular tabletop exercises and simulations can help test the plan’s effectiveness and identify areas for improvement. The plan should include procedures for notifying relevant stakeholders, such as law enforcement and affected parties, as well as steps for restoring systems and data. A robust incident response plan is critical for minimizing the damage caused by a successful attack and ensuring a swift recovery.
Attribution and Geopolitical Context of BrazenBamboo
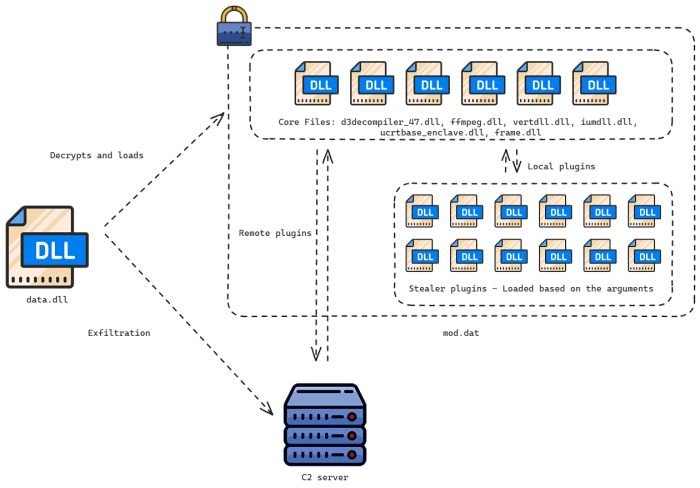
Source: securityonline.info
Pinpointing the exact origins of sophisticated cyberattacks like those attributed to BrazenBamboo is a complex, often shadowy affair. While definitive proof remains elusive in many cases, analysts piece together clues from various sources to build a compelling case for attribution. This involves examining the malware’s code, infrastructure used, attack techniques, and the targets themselves. The geopolitical context surrounding these attacks often reveals the potential motivations and strategic goals of the actors involved.
The attribution of BrazenBamboo attacks to a specific state-sponsored actor relies on a convergence of technical indicators and geopolitical analysis. Evidence suggests a strong connection to a particular nation, but definitive proof requires a level of transparency that is rarely available in this arena. The analysis focuses on similarities in tactics, techniques, and procedures (TTPs) to previously identified campaigns, infrastructure overlaps, and the nature of the targeted entities. The consistent targeting of specific industries and geographic regions further supports the hypothesis.
Technical Indicators of Compromise (TICs) and Attribution
The attribution process for BrazenBamboo leverages a multitude of technical indicators. These include the unique code signatures within the malware used in the attacks, the command-and-control (C2) infrastructure employed, and the specific vulnerabilities exploited. Analysts compare these TICs to known threat actor profiles and observed behaviors. For instance, the use of specific zero-day exploits in FortiClient, combined with the unique coding style and infrastructure characteristics, creates a fingerprint that can be compared against other known APT groups’ activities. The similarity in these characteristics across multiple attacks strengthens the attribution case.
Geopolitical Motivations and Target Selection
BrazenBamboo’s activities appear driven by geopolitical interests, focusing on intelligence gathering and potentially industrial espionage. The consistent targeting of specific sectors – such as telecommunications, government, and defense – suggests a strategic intent to acquire sensitive information or disrupt critical infrastructure. The geographic concentration of targets also provides clues about the actor’s priorities and potential areas of strategic interest. This targeting pattern, coupled with the sophisticated nature of the attacks, points to a state-sponsored actor with significant resources and capabilities. Understanding this context is vital to anticipating future attack vectors.
Comparison with Other Known APT Groups
Comparing BrazenBamboo’s activities to other known advanced persistent threat (APT) groups helps establish its unique characteristics and potential affiliations. While some similarities in TTPs may exist with other groups, unique aspects of BrazenBamboo’s operations – such as its reliance on specific zero-day exploits and its preference for certain target sectors – differentiate it. This comparative analysis helps refine the attribution and provides valuable insight into the overall threat landscape. Differences in infrastructure, code style, and operational tempo also help distinguish BrazenBamboo from other actors.
Timeline of Significant BrazenBamboo Attacks
A precise timeline of all BrazenBamboo attacks is difficult to compile due to the clandestine nature of these operations. However, publicly available information indicates a pattern of activity spanning several years. Early attacks may have gone unnoticed, while more recent incidents have garnered increased attention due to their impact and the discovery of the FortiClient vulnerabilities. Further research is required to fully map the extent and scope of BrazenBamboo’s operations. Each confirmed attack provides a data point in constructing a more complete picture of the group’s activities and evolution. This ongoing monitoring is crucial for effective threat mitigation.
Visual Representation of the Attack Chain

Source: blackhatethicalhacking.com
Understanding the BrazenBamboo attack chain requires visualizing its sequential steps. A clear diagram helps security professionals identify vulnerabilities and implement effective countermeasures. The following description Artikels a visual representation, focusing on the key stages and their interrelationships.
The attack chain can be represented as a flow chart, progressing from left to right, illustrating the chronological order of events. Each stage is represented by a distinct node, and the connections between nodes are depicted by arrows, indicating the direction of the attack’s progression.
Initial Access
This node represents the initial compromise of a target system. It could be depicted as a computer icon with a red warning sign overlaid. The connecting arrow leading from this node would point to the next stage, indicating the successful penetration of the target’s network perimeter. Examples of initial access vectors for BrazenBamboo might include spear-phishing emails containing malicious attachments or exploiting vulnerabilities in FortiClient. The description within this node could detail the specific vulnerability exploited (e.g., CVE-XXXX-XXXX) or the social engineering techniques employed.
Execution
This node, represented by a running program icon, depicts the execution of malicious code on the compromised system. The arrow from the “Initial Access” node connects to this node. The description here could detail the type of malware used (e.g., a custom backdoor, a RAT) and its functionalities. It might also mention any persistence mechanisms employed by the malware to maintain access to the system.
Persistence
Represented by a padlock icon, this node highlights the attacker’s efforts to maintain persistent access to the compromised system. This could involve the installation of a backdoor, scheduled tasks, or registry modifications. The arrow connecting this node to the next indicates the establishment of a long-term foothold. The description could mention specific techniques used for persistence, such as the creation of a service or the modification of startup scripts.
Privilege Escalation
This node, depicted by a key icon with an upward-pointing arrow, represents the attacker’s attempt to gain higher-level privileges on the compromised system. This allows access to sensitive data and system resources. The arrow from the “Persistence” node connects to this one. The description could include the techniques employed for privilege escalation, such as exploiting known vulnerabilities or leveraging existing credentials.
Discovery
This node, represented by a magnifying glass icon, symbolizes the attacker’s activities in identifying valuable data and systems within the network. The arrow from “Privilege Escalation” connects here. The description would detail the methods used for reconnaissance, such as network scanning, file system traversal, and database queries.
Lateral Movement
This node, represented by a network diagram showing connections between multiple systems, depicts the attacker’s movement across the network to access other systems and data. The arrow from the “Discovery” node points to this. The description would explain how the attacker moved from one compromised system to another, potentially using techniques like pass-the-hash or exploiting network vulnerabilities.
Data Exfiltration
This node, represented by an upward-pointing arrow leaving a data server icon, signifies the exfiltration of stolen data from the compromised network. The arrow from “Lateral Movement” connects here. The description would specify the methods used for exfiltration, such as using command-and-control servers, cloud storage services, or other data transfer channels. It could also mention the type of data stolen.
Final Wrap-Up: Brazenbamboo Apt Forticlient Zero Day
The BrazenBamboo APT FortiClient zero-day exploit highlights a crucial need for proactive cybersecurity measures. Regular patching, robust vulnerability management, and a layered security approach are no longer optional – they’re essential. Understanding the adversary’s TTPs and staying ahead of the curve is the only way to effectively mitigate the risks posed by sophisticated threats like BrazenBamboo. Ignoring this is simply not an option in today’s digital landscape.





