SASE vs traditional network security: It’s the cybersecurity showdown of the decade. Forget dusty firewalls and complex VPNs – the cloud’s changed the game. This isn’t your grandpappy’s network protection; we’re talking about a shift as seismic as the move from floppy disks to cloud storage. One approach is clinging to the past, while the other embraces the future of secure access. Let’s dive into the battle and see which emerges victorious.
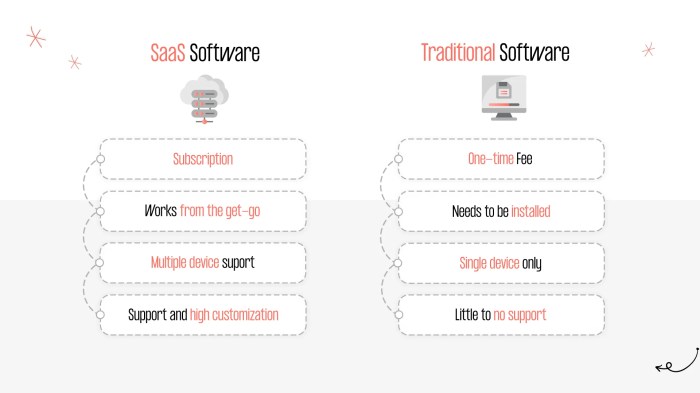
Traditional network security relies on a patchwork of on-premises solutions – firewalls, intrusion detection systems, VPNs – creating a complex, often siloed, infrastructure. SASE, on the other hand, integrates these functions into a cloud-delivered service, offering a simpler, more scalable, and potentially more cost-effective solution. This shift impacts everything from deployment and management to security capabilities and overall cost. We’ll break down the key differences, helping you decide which approach best suits your needs.
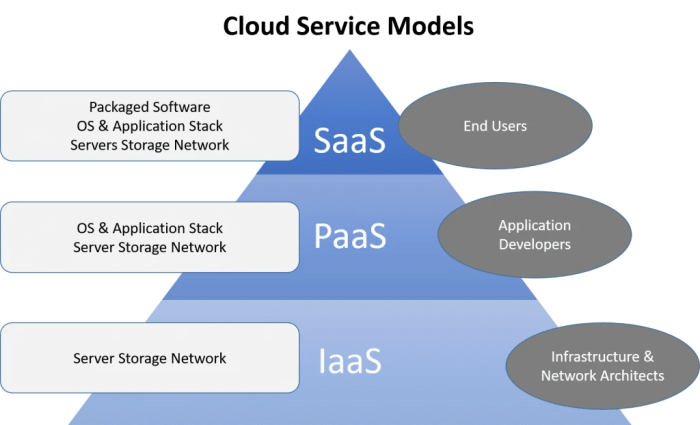
Defining SASE and Traditional Network Security: Sase Vs Traditional Network Security
Source: cloudinary.com
The digital landscape is shifting, and with it, the way we secure our networks. Traditional network security, built on a perimeter-based model, is increasingly struggling to keep pace with the rise of cloud computing, remote work, and mobile devices. Enter SASE, a cloud-native approach promising a more agile and secure future. Let’s break down the differences.
Traditional Network Security Architecture
Traditional network security relies on a perimeter-based approach. Think of it like a castle with high walls and a moat: the network is protected by a series of security appliances located at the edge of the network. This architecture typically involves a firewall, intrusion detection/prevention systems (IDS/IPS), virtual private networks (VPNs), and other security tools deployed on-premises or in data centers. The core idea is to control access to the network and protect internal resources from external threats. This approach, however, struggles with the complexities of today’s distributed workforce and cloud-based applications.
SASE Architecture Core Elements
SASE, or Secure Access Service Edge, flips the script. Instead of relying on a physical perimeter, SASE leverages cloud-delivered security services to protect users and devices wherever they are. The core elements include secure web gateways (SWG), cloud access security brokers (CASBs), zero trust network access (ZTNA), and firewall-as-a-service (FWaaS), all integrated and delivered from the cloud. This allows for consistent security policies regardless of location or device, providing a more flexible and scalable security posture. Imagine a security shield that follows the user, adapting to their location and the resources they access.
Comparing SASE and Traditional Security Deployment Models
The differences between SASE and traditional security are stark, especially when it comes to deployment. Here’s a comparison:
| Feature | Traditional | SASE | Advantages/Disadvantages |
|---|---|---|---|
| Deployment Model | On-premises, data center | Cloud-based | Traditional: Requires significant upfront investment and ongoing maintenance. SASE: Easier to deploy and scale, but relies on cloud provider availability and potentially higher ongoing costs. |
| Management | On-site management, complex configuration | Centralized cloud management, simplified configuration | Traditional: Requires specialized IT expertise. SASE: Easier to manage, potentially reducing the need for extensive in-house expertise. |
| Scalability | Limited scalability, requires significant upgrades for growth | Highly scalable, easily adapts to changing needs | Traditional: Expanding capacity can be expensive and time-consuming. SASE: Easily scales to accommodate increased user base and application needs. |
| Security Policy Enforcement | Enforced at the network perimeter | Enforced consistently across all access points | Traditional: Vulnerable to attacks that bypass the perimeter. SASE: Provides consistent security regardless of location or device, improving overall security posture. |
Security Capabilities Comparison
Source: medium.com
Traditional network security and SASE offer vastly different approaches to protecting your digital assets. While traditional methods rely on perimeter-based defenses, SASE leverages cloud-based services to provide security wherever your users and devices are. This leads to significant differences in their security capabilities.
Traditional network security typically involves a layered approach, with each layer focusing on specific threats. This often results in a complex, siloed architecture that can be difficult to manage and maintain. SASE, on the other hand, integrates these security functions into a unified cloud-delivered service, simplifying management and improving overall security posture.
Traditional Network Security Functions
Traditional network security relies heavily on on-premises infrastructure and employs various security functions to protect the network perimeter. These functions include firewalls, which control network traffic based on pre-defined rules; intrusion detection/prevention systems (IDS/IPS), which monitor network traffic for malicious activity; and virtual private networks (VPNs), which create secure connections between remote users and the corporate network. Antivirus software and data loss prevention (DLP) tools are also commonly deployed to protect endpoints and prevent sensitive data from leaving the network. However, these solutions often operate in isolation, creating gaps in security and complicating management.
SASE Security Services
SASE, in contrast, provides a consolidated set of security services delivered from the cloud. Key components include Secure Web Gateway (SWG), which filters and inspects web traffic; Cloud Access Security Broker (CASB), which monitors and controls access to cloud applications; and Zero Trust Network Access (ZTNA), which provides secure access to internal resources based on identity and context, regardless of location. SASE also incorporates other security functions such as firewall as a service, intrusion detection/prevention as a service, and DLP capabilities. The integration of these services simplifies management and improves overall security effectiveness.
Data Loss Prevention (DLP) Differences
Traditional DLP solutions typically rely on on-premises infrastructure and often struggle to protect data as it moves across multiple locations and cloud services. They might use techniques like data masking, encryption, and access control to limit data exposure. SASE, however, offers a more comprehensive approach to DLP. By integrating DLP capabilities into its cloud-based security services, SASE can monitor and control data flow regardless of location or device. This includes monitoring data in transit and at rest, across various cloud services and on-premises environments, offering more robust protection against data breaches. For example, a SASE platform can detect and prevent sensitive data from being uploaded to unauthorized cloud storage services or shared via unsecure channels.
Comparative Threat Protection
The following table compares the strengths and weaknesses of traditional network security and SASE in protecting against common cyber threats:
| Threat | Traditional Network Security | SASE |
|---|---|---|
| Phishing | Relies on user education and email filtering; can be bypassed by sophisticated attacks. | SWG and CASB can detect and block malicious links and attachments; better protection against advanced phishing techniques. |
| Malware | Antivirus and endpoint protection are crucial; can be slow to detect and respond to new threats. | Integrated threat protection and sandboxing capabilities offer faster detection and response; protection extends to cloud applications and devices. |
| DDoS | Requires robust network infrastructure and DDoS mitigation solutions; can be expensive and complex to implement. | Cloud-based DDoS mitigation services offer scalability and resilience; can effectively mitigate attacks of various sizes. |
| Insider Threats | Relies on access controls and monitoring; can be difficult to detect and prevent malicious insider activity. | ZTNA and CASB can limit access to sensitive data based on identity and context; improved visibility into user activity. |
Deployment and Management Aspects
Deploying and managing a network security infrastructure can feel like navigating a labyrinth, especially when comparing the traditional approach to the relatively new SASE architecture. Traditional setups often involve a complex web of on-premises hardware and software, requiring significant IT expertise and ongoing maintenance. SASE, on the other hand, offers a cloud-centric approach promising streamlined management and scalability. Let’s delve into the specifics.
Traditional vs. SASE Deployment Complexity
Traditional network security deployments are notoriously complex. They typically involve multiple point solutions (firewalls, VPNs, intrusion detection systems, etc.) located across various physical locations. This necessitates intricate configuration, ongoing maintenance, and specialized personnel to manage each component. Troubleshooting becomes a significant challenge as issues could arise from interactions between disparate systems. In contrast, SASE simplifies deployment by consolidating security functions into a cloud-based service. This centralized architecture reduces the complexity of management and simplifies troubleshooting. While initial setup might require careful planning, the ongoing management overhead is significantly lower. Think of it like this: managing a fleet of individual cars versus driving a single, well-maintained vehicle.
Cloud-Based vs. On-Premises Deployment: Advantages and Disadvantages
The choice between cloud-based and on-premises deployment significantly impacts both traditional and SASE architectures.
| Deployment Model | Traditional Network Security: Advantages | Traditional Network Security: Disadvantages | SASE: Advantages | SASE: Disadvantages |
|---|---|---|---|---|
| Cloud-Based | Increased scalability and flexibility; reduced capital expenditure | Dependency on internet connectivity; potential security concerns related to data sovereignty; vendor lock-in | Simplified management; improved scalability and agility; reduced operational costs; better security posture through centralized control | Dependency on internet connectivity; potential latency issues; reliance on the vendor’s security capabilities |
| On-Premises | Greater control over security policies and data; reduced dependency on internet connectivity; potentially lower latency | High capital expenditure; complex management; limited scalability; ongoing maintenance costs; requires dedicated IT expertise | Not applicable – SASE is inherently cloud-based | Not applicable |
Migrating from Traditional Security to SASE
Migrating from a traditional security model to SASE is a phased process requiring careful planning and execution. A successful migration involves several key steps:
- Assessment and Planning: Conduct a thorough assessment of your existing network security infrastructure, identifying gaps and areas for improvement. Develop a detailed migration plan outlining timelines, resources, and potential challenges.
- Proof of Concept (POC): Implement a POC to test the SASE solution in a controlled environment, validating its performance and integration with your existing systems. This helps identify and address potential issues before a full-scale deployment.
- Phased Rollout: Migrate to SASE gradually, starting with less critical applications or user groups. This minimizes disruption and allows for iterative improvements based on feedback and experience.
- Integration and Testing: Integrate the SASE solution with existing systems and thoroughly test its functionality to ensure seamless operation and security. This step is crucial to avoid any disruption in service after migration.
- Monitoring and Optimization: Continuously monitor the SASE solution’s performance and security posture, making adjustments as needed to optimize its effectiveness. This ensures ongoing security and performance.
Factors to Consider When Choosing Between SASE and Traditional Network Security, Sase vs traditional network security
The choice between SASE and traditional network security depends on several crucial factors specific to each organization. These include:
- Budget: SASE often involves a subscription model, while traditional solutions require significant upfront capital expenditure.
- IT Expertise: SASE generally requires less specialized IT expertise for ongoing management than traditional solutions.
- Scalability Requirements: SASE offers superior scalability compared to traditional solutions, making it ideal for organizations with rapidly growing networks.
- Security Requirements: Both SASE and traditional solutions can provide robust security, but the specific features and capabilities vary. A thorough comparison is essential.
- Network Complexity: For complex, geographically dispersed networks, SASE’s centralized management capabilities offer significant advantages.
Cost and Scalability Considerations
Source: gapsystudio.com
Choosing between traditional network security and SASE often boils down to the bottom line: cost. While initial investments might seem comparable, the long-term picture reveals significant differences in total cost of ownership (TCO) and scalability, particularly as your organization grows. Let’s break down the financial and operational implications of each approach.
Traditional network security solutions typically involve a patchwork of on-premises hardware and software, requiring significant upfront capital expenditure. This includes firewalls, intrusion detection/prevention systems (IDS/IPS), VPN gateways, and other security appliances. Ongoing maintenance includes hardware replacement, software licensing, and dedicated IT staff to manage and maintain the entire infrastructure. Scaling this setup involves purchasing and installing additional hardware, which can be expensive and time-consuming.
Total Cost of Ownership (TCO) Comparison
The TCO for traditional network security is generally higher than SASE, especially in the long run. Initial investment in hardware and software is substantial, and ongoing maintenance costs can quickly add up. SASE, being a cloud-based service, typically operates on a subscription model. While there are recurring costs, these are often more predictable and scalable than the unpredictable expenses associated with maintaining on-premises hardware. For example, a small business might initially find the subscription cost of a SASE solution higher than investing in a single, basic firewall. However, as the business grows and needs more advanced security features, the cost of upgrading or expanding the traditional setup far surpasses the incremental cost of scaling a SASE solution.
Scalability and Growth Accommodation
Traditional network security struggles to scale effectively. Adding new users, applications, or data often necessitates significant hardware upgrades or replacements. This process is slow, disruptive, and costly. SASE, conversely, is designed for scalability. As your organization grows, you simply adjust your subscription to accommodate the increased demands. This allows for seamless growth without the need for major infrastructure overhauls. Imagine a rapidly expanding startup. With SASE, they can easily add users and applications without worrying about capacity limitations or expensive hardware upgrades. With a traditional setup, they would likely face significant delays and expenses as they scale.
Cost-Effectiveness and Organizational Size
The cost-effectiveness of each approach varies significantly depending on the size and complexity of the organization. For small businesses with limited IT resources, the simplicity and scalability of SASE can offer significant cost advantages. Larger enterprises with complex network infrastructures might initially see higher SASE subscription fees, but the reduced operational costs, improved efficiency, and reduced risk associated with managing a distributed infrastructure can outweigh these costs. For instance, a large multinational corporation with offices globally would likely benefit significantly from the centralized management and consistent security policies offered by SASE, despite the higher initial subscription cost. The reduction in travel and on-site maintenance costs alone could easily offset the difference.
Return on Investment (ROI)
The potential ROI for both approaches depends on several factors, including organization size, existing infrastructure, and security priorities. However, we can highlight some key differences:
- Traditional Network Security: ROI is often slower and less predictable due to high upfront costs, ongoing maintenance expenses, and the potential for security breaches. The ROI is largely driven by preventing security incidents, which is difficult to quantify.
- SASE: ROI is typically faster and more easily measurable due to lower upfront costs, predictable subscription fees, and the ability to scale efficiently. The ROI includes reduced operational costs, improved security posture, and enhanced productivity.
Illustrative Examples of Use Cases
Choosing between SASE and traditional network security depends heavily on an organization’s size, structure, and specific needs. Let’s look at how different organizations might approach this decision.
Small Business: “Coffee Corner” Cafe
Coffee Corner, a small cafe with three locations and a total of 20 employees, primarily uses point-of-sale systems and a basic website for online ordering. Their security needs are relatively straightforward: protecting customer payment data and preventing unauthorized access to their internal systems. A traditional network security approach, involving a firewall, basic intrusion detection, and antivirus software on their individual devices, would likely suffice. The cost-effectiveness and ease of management of this solution outweigh the benefits of a more complex SASE architecture. Implementing SASE would be an overkill and introduce unnecessary complexity and expense for their scale. Failing to implement even basic traditional security could leave them vulnerable to data breaches and financial losses.
Large Enterprise: “TechGiant” Software Company
TechGiant, a large software company with thousands of employees across multiple offices and numerous cloud-based applications, requires a robust and scalable security solution. Their security challenges include protecting sensitive intellectual property, ensuring compliance with industry regulations, and securing access for remote employees. SASE is the far superior choice for TechGiant. Its centralized management, consistent security policies across all locations and access points (regardless of whether employees are in the office or working remotely), and advanced threat protection capabilities are essential for safeguarding their vast and complex infrastructure. Sticking with a traditional approach would struggle to keep pace with their growth, introduce significant management overhead, and increase the risk of security breaches due to inconsistencies and gaps in their security posture. The financial impact of a significant data breach for a company of TechGiant’s size would be catastrophic.
Global Corporation: “GlobalCorp” Multinational Conglomerate
GlobalCorp, a multinational conglomerate with operations in dozens of countries, faces a multitude of security challenges, including data sovereignty concerns, compliance with varying regional regulations, and the need to protect sensitive data across a highly distributed workforce. SASE is crucial for GlobalCorp. Its ability to enforce consistent security policies across diverse geographical locations, integrate seamlessly with various cloud services, and provide advanced threat protection tailored to specific regional contexts is indispensable. A traditional approach would be nearly impossible to manage effectively across such a geographically dispersed and complex environment, leading to significant security vulnerabilities and compliance risks. The potential reputational and financial damage from a security breach affecting multiple jurisdictions would be immensely significant, impacting their global operations and brand image.
Epilogue
The choice between SASE and traditional network security isn’t a one-size-fits-all. While traditional methods might still suffice for smaller, less complex organizations, the agility, scalability, and integrated security offered by SASE make it a compelling option for larger enterprises and those embracing cloud-first strategies. Ultimately, the “winner” depends entirely on your specific circumstances. By carefully weighing the factors we’ve discussed – cost, complexity, security capabilities, and scalability – you can make an informed decision that safeguards your data and future-proofs your network.





