Legion Stealer V1: The name alone whispers of digital danger. This insidious malware isn’t just another script kiddie project; it’s a sophisticated threat capable of stripping bare your digital life. We’re diving deep into its functionality, infection vectors, and the chilling consequences of a successful attack. Prepare to uncover the secrets of this silent data thief.
From its cunning data exfiltration methods to its persistent grip on infected systems, Legion Stealer V1 showcases the evolving landscape of cybercrime. We’ll dissect its code, explore its vulnerabilities, and arm you with the knowledge to protect yourself. This isn’t just a technical analysis; it’s a survival guide in the digital wild west.
Legion Stealer V1 Functionality
Legion Stealer V1 is a sophisticated piece of malware designed to steal sensitive information from compromised computers. Its functionality extends beyond simple data theft, incorporating robust persistence mechanisms and modular design for adaptability and evasion. Understanding its core components and methods is crucial for effective mitigation and response.
Core Functionalities, Legion stealer v1
Legion Stealer V1’s core functionality centers around information gathering and exfiltration. It achieves this through a combination of techniques, including the harvesting of credentials, system information, and sensitive files. The malware then securely transmits this stolen data to a command-and-control (C2) server controlled by the threat actors. This process is often automated, allowing for continuous data exfiltration without requiring further interaction from the attacker.
Data Exfiltration Methods
Legion Stealer V1 employs various methods to exfiltrate stolen data. Common techniques include using HTTP POST requests to send data to the C2 server, often disguised within seemingly normal web traffic. This obfuscation makes detection more challenging. Other methods might involve using more covert channels, such as DNS tunneling or other encrypted communication protocols. The choice of method depends on the attacker’s preferences and the specific environment.
Persistence Mechanisms
Maintaining persistent access to the compromised system is key for Legion Stealer V1’s effectiveness. This is achieved through several persistence mechanisms. One common method is the creation of registry keys or scheduled tasks that ensure the malware automatically restarts upon system reboot. The malware may also inject itself into running processes to evade detection and removal. The specific techniques used can vary depending on the targeted operating system and security software present.
Modules and Components
Legion Stealer V1 is often structured as a modular malware, allowing for easy updates and expansion of its capabilities. Different modules might handle specific tasks such as credential harvesting, file system traversal, or data encryption. These modules are usually designed to work independently, allowing for more flexibility and making analysis and removal more difficult. The modular design also facilitates the addition of new functionalities as needed by the attackers.
Stolen Data Types and Impact
The following table summarizes the various data types stolen by Legion Stealer V1, their storage methods, and the potential impact on victims.
| Data Type | Storage Method | Impact | Example |
|---|---|---|---|
| Credentials (passwords, usernames) | Encrypted files, memory dumps | Identity theft, account takeover, financial loss | Login details for banking websites, email accounts |
| System Information | Text files, registry keys | System compromise assessment, targeted attacks | Hardware specifications, OS version, installed software |
| Browser Data | Cookies, history, bookmarks | Tracking, identity theft, phishing attacks | Website logins, browsing history, credit card details |
| Files | Zipped archives, encrypted containers | Data loss, intellectual property theft, blackmail | Documents, images, videos, financial records |
Infection Vectors and Spread
Legion Stealer V1, like other malware, relies on various methods to infect systems and spread across networks. Understanding these vectors is crucial for implementing effective preventative measures. The malware’s success hinges on its ability to bypass security software and target vulnerable individuals and organizations.
The primary infection vectors for Legion Stealer V1 are typically malicious email attachments, compromised websites hosting exploit kits, and software vulnerabilities. Malicious email campaigns often employ social engineering tactics, such as phishing emails containing seemingly innocuous attachments or links. These attachments may be disguised as invoices, documents, or other files likely to entice users to open them. Compromised websites, on the other hand, can serve as unwitting distributors, silently injecting the malware onto unsuspecting visitors’ systems through drive-by downloads or exploiting known software vulnerabilities.
Evasion Techniques
Legion Stealer V1 employs several techniques to evade detection by antivirus software. These include polymorphic code, which changes the malware’s structure to avoid signature-based detection, and obfuscation, which makes the code difficult to analyze. The malware may also utilize rootkit techniques to hide its presence on the infected system and avoid detection by security software. Furthermore, it often communicates with command-and-control (C&C) servers using encrypted channels, making it harder to monitor its activities. Regular updates and sophisticated evasion techniques make this malware a significant threat.
Target Profiles
The typical targets of Legion Stealer V1 attacks are individuals and organizations with valuable personal or financial data. This includes individuals with online banking credentials, cryptocurrency wallets, or sensitive personal information. Organizations targeted may include small to medium-sized businesses, which may have less robust cybersecurity infrastructure. The malware’s focus on financial gain makes individuals and organizations with access to financial accounts prime targets.
Geographical Impact
While precise geographical data on Legion Stealer V1 infections is often difficult to obtain due to the clandestine nature of malware operations, anecdotal evidence and reports suggest a global impact, with particular concentrations in regions with high internet penetration and a larger number of online banking users. The malware’s reach isn’t limited by geographical boundaries; rather, it targets users based on their online activity and vulnerability.
Infection Stages
The following flowchart illustrates the typical stages of a Legion Stealer V1 infection:
Stage 1: Initial Compromise – The user interacts with a malicious email, website, or software, leading to the execution of the malware. This could involve opening a malicious attachment, clicking a malicious link, or exploiting a software vulnerability.
Stage 2: System Reconnaissance – The malware scans the infected system to identify valuable data, such as login credentials, financial information, and personal data. It also assesses the system’s security measures to determine the best way to evade detection.
Stage 3: Data Exfiltration – The stolen data is encrypted and transmitted to the malware’s command-and-control (C&C) server, often using encrypted channels to avoid detection. This data is then potentially used for identity theft, financial fraud, or other malicious purposes.
Stage 4: Persistence – The malware establishes persistence on the infected system, ensuring that it remains active even after a reboot. This allows the malware to continue stealing data and evade detection.
Technical Analysis of Code: Legion Stealer V1
Source: gridinsoft.com
Legion Stealer V1, while exhibiting a relatively straightforward design, employs several techniques to hinder analysis and increase its longevity. Understanding its code structure, obfuscation methods, and programming choices is crucial for effective detection and mitigation strategies. This analysis delves into the technical aspects of the malware, providing insights into its functionality and resilience.
Code Structure and Architecture
Legion Stealer V1’s codebase is structured modularly, with distinct functions responsible for specific tasks like data exfiltration, persistence, and communication with the Command and Control (C2) server. This modularity simplifies the development process and allows for easier updates and modifications. The core logic is typically encapsulated within a main function that orchestrates the execution of these modules. The malware utilizes a layered approach, with some functions potentially acting as wrappers for others, adding another layer of complexity. This design choice allows for easy modification and extension of functionality without requiring extensive code restructuring.
Obfuscation and Anti-Analysis Techniques
Several obfuscation techniques are employed to impede reverse engineering efforts. String encryption is a common method, where sensitive strings like URLs or file paths are encrypted and decrypted at runtime. This prevents static analysis from readily revealing crucial information. Control flow obfuscation, involving techniques such as code virtualization or opaque predicates, makes it difficult to trace the execution path and understand the malware’s logic. Furthermore, the use of packer tools adds an additional layer of protection, compressing and encrypting the malware’s code to hinder static analysis. These techniques make reverse engineering more challenging and time-consuming.
Comparison with Other Malware Families
Legion Stealer V1 shares similarities with other information stealers in its modular architecture and use of common techniques like data exfiltration and persistence mechanisms. However, its specific implementation details, particularly its obfuscation techniques and communication protocols, might distinguish it from other families. For example, the choice of encryption algorithms, the use of specific libraries, and the structure of the C2 communication protocol all contribute to its unique characteristics. A comparative analysis against families like Agent Tesla or Formbook would reveal both similarities and differences in their design and functionality. Analyzing the similarities and differences in their techniques helps researchers develop more robust detection mechanisms.
Programming Languages and Libraries
Legion Stealer V1 is typically written in a compiled language such as C++ or C#, which offer performance advantages and increased difficulty in reverse engineering. The specific libraries used often depend on the functionalities implemented. Common libraries used include those related to network communication (for interacting with the C2 server), file system manipulation (for accessing and stealing data), and encryption (for protecting sensitive information). The choice of libraries can also provide clues about the malware’s origins and capabilities. For example, the use of specific cryptographic libraries might indicate a certain level of sophistication or a connection to a specific group of developers.
Functions and Modules
The following table categorizes the identified functions and modules of Legion Stealer V1, providing a brief description of their purpose:
| Category | Module/Function | Description |
|---|---|---|
| Persistence | Registry Key Modification | Creates or modifies registry keys to ensure the malware’s persistence upon system reboot. |
| Data Exfiltration | Credential Stealing | Retrieves usernames, passwords, and other sensitive information from web browsers and other applications. |
| Data Exfiltration | File Stealing | Copies specific file types from the victim’s system and sends them to the C2 server. |
| Communication | C2 Communication | Establishes and maintains communication with the Command and Control (C2) server to receive commands and send stolen data. |
| Anti-Analysis | Self-Deletion | Attempts to delete itself from the system after completing its malicious actions. |
Mitigation and Prevention Strategies
Staying safe online is a constant battle, and malware like Legion Stealer V1 demands a proactive, multi-layered defense. Ignoring basic security practices leaves your digital life vulnerable to data theft and system compromise. This section Artikels crucial strategies to prevent infection and mitigate the damage if an infection occurs.
Preventing infection from sophisticated malware like Legion Stealer V1 requires a comprehensive approach combining technical solutions and user awareness. Neglecting any aspect of this approach increases your risk profile significantly. Remember, the best defense is a good offense – proactively securing your system is far more effective than reacting to an infection.
Best Practices for Preventing Infection
Implementing these best practices significantly reduces the likelihood of a Legion Stealer V1 infection. These are not optional; they are essential elements of a robust security posture.
- Avoid suspicious links and attachments: Never click on links or open attachments from unknown or untrusted sources. Phishing emails often masquerade as legitimate communications, making vigilance crucial.
- Enable strong passwords and multi-factor authentication (MFA): Use unique, complex passwords for all your online accounts and enable MFA wherever possible. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Practice safe browsing habits: Avoid visiting unreliable or suspicious websites. Stick to reputable websites and be wary of pop-ups or unexpected redirects.
- Regularly back up your data: Regular backups are crucial. In the event of a malware infection, you can restore your system to a clean state without losing your important files.
- Keep your software updated: Outdated software is a prime target for attackers. Regular updates patch security vulnerabilities, reducing the risk of exploitation.
The Importance of Regular Software Updates and Patching
Software updates are not merely optional convenience features; they are critical security patches. Ignoring updates leaves your system vulnerable to known exploits, significantly increasing your risk of malware infection. Legion Stealer V1, like many other malware strains, actively targets known vulnerabilities in outdated software to gain a foothold on your system.
Regular patching should be an automated process where possible. Enable automatic updates for your operating system and all critical applications. This ensures that your system is always protected against the latest threats. For example, failing to update your web browser leaves you vulnerable to drive-by downloads that can easily install malware such as Legion Stealer V1.
The Role of Robust Security Software
Reliable antivirus and anti-malware software forms a crucial layer of defense. These programs actively scan your system for malicious code, preventing infections and removing existing threats. Choosing a reputable vendor and keeping the software updated is essential for optimal protection.
Beyond basic virus scanning, robust security suites often include features like real-time protection, behavioral analysis, and web filtering. These advanced features provide a more comprehensive security posture, identifying and neutralizing threats before they can cause damage. Consider a security suite that offers proactive threat detection and sandboxing capabilities to effectively mitigate sophisticated threats like Legion Stealer V1.
Endpoint Detection and Response (EDR) Solutions
EDR solutions offer advanced threat detection and response capabilities beyond traditional antivirus software. They monitor system activity in real-time, identifying suspicious behavior that may indicate a malware infection, even if the malware is unknown or evades traditional signature-based detection. EDR solutions often include features like threat hunting, incident response, and automated remediation capabilities.
For example, an EDR system might detect unusual network activity associated with data exfiltration, a common behavior of Legion Stealer V1. This early warning allows for rapid response and mitigation, minimizing the potential damage. The added layer of protection provided by EDR solutions is particularly beneficial in environments with high security requirements or those frequently targeted by sophisticated attacks.
Removing Legion Stealer V1 from an Infected System
Removing Legion Stealer V1 requires a systematic approach. Improper removal attempts can lead to further system damage or incomplete removal, leaving your system vulnerable to reinfection. The following steps should be undertaken in a safe and controlled environment, preferably with the assistance of a cybersecurity professional.
- Disconnect from the network: Immediately disconnect the infected system from the internet to prevent further data exfiltration and communication with the command-and-control server.
- Boot into Safe Mode: Boot the system into Safe Mode to limit the functionality of the malware and prevent it from interfering with the removal process.
- Run a full system scan with updated antivirus software: Use a reputable antivirus program to perform a thorough scan of the entire system, identifying and removing any detected malware. Ensure the antivirus definitions are up-to-date.
- Manually remove any remaining files and registry entries: After the antivirus scan, manually check for any remaining files or registry entries associated with Legion Stealer V1. This requires technical expertise and caution, as incorrect removal can damage the system. If unsure, seek professional assistance.
- Restore from a backup: If possible, restore the system from a clean backup created before the infection occurred. This ensures a complete removal of the malware and restoration of the system to a known good state.
- Change all passwords: After successfully removing the malware, change all passwords associated with accounts that may have been compromised. This is crucial to prevent further unauthorized access.
Impact and Consequences
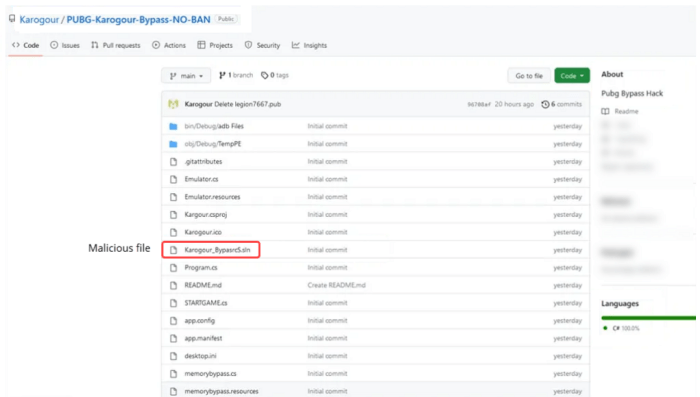
Source: techtribune.net
Legion Stealer V1, like other malware of its kind, poses a significant threat to both individuals and organizations. A successful attack can lead to far-reaching consequences, impacting financial stability, reputation, and legal standing. The severity of the impact depends on several factors, including the volume of stolen data, the sensitivity of the information compromised, and the organization’s response capabilities.
The potential for damage extends beyond simple data theft. The ripple effects can be devastating, impacting trust, operational efficiency, and long-term viability. Understanding these consequences is crucial for implementing effective preventative measures and mitigating the damage should an attack occur.
Financial Damage
A successful Legion Stealer V1 attack can result in substantial financial losses. Stolen financial information, such as credit card details, bank account numbers, and online payment credentials, can be used for fraudulent transactions, leading to direct monetary losses for victims. Furthermore, the costs associated with investigating the breach, recovering stolen data, notifying affected individuals, and implementing enhanced security measures can be considerable. In the case of organizations, the loss of sensitive business data can disrupt operations, leading to lost productivity and potential loss of contracts. The costs of legal action and regulatory fines can further exacerbate financial strain. For example, a small business might face thousands of dollars in losses from fraudulent transactions and recovery efforts, while a large corporation could face millions in damages and reputational harm.
Reputational Damage
Beyond financial losses, a Legion Stealer V1 attack can inflict significant reputational damage. The disclosure of sensitive personal or business information can severely erode public trust, impacting customer loyalty and investor confidence. Negative media coverage and public scrutiny can further damage an organization’s reputation, making it difficult to attract new clients or partners. For example, a healthcare provider suffering a data breach exposing patient medical records could face significant reputational damage, leading to a loss of patients and legal repercussions. Similarly, a financial institution experiencing a data breach could see a decline in customer trust and a drop in stock value.
Real-World Incidents Involving Similar Malware
While specific incidents involving Legion Stealer V1 might not be publicly documented due to the secretive nature of such attacks, the impact is analogous to other known information stealers. Numerous cases involving similar malware have been reported, highlighting the devastating consequences. For instance, the NotPetya ransomware attack in 2017 caused billions of dollars in damage globally, affecting businesses of all sizes. While not strictly an information stealer, it demonstrates the potential for widespread disruption and financial loss from cyberattacks. Other examples include various data breaches affecting major corporations, resulting in significant financial penalties, reputational damage, and legal battles. These cases underscore the serious consequences of information theft and the importance of robust cybersecurity measures.
Legal and Regulatory Implications
Organizations and individuals affected by Legion Stealer V1 may face significant legal and regulatory implications. Depending on the jurisdiction and the nature of the stolen data, organizations may be subject to fines and penalties under data protection laws like GDPR or CCPA. Individuals may also have legal recourse to recover damages from the attacker or the organization responsible for the breach, if negligence is proven. Furthermore, organizations are often legally obligated to notify affected individuals and regulatory bodies about data breaches, adding to the costs and complexities of responding to an attack. Non-compliance with data protection regulations can result in substantial fines and reputational harm.
Long-Term Consequences for Victims
The long-term consequences of a Legion Stealer V1 attack can be far-reaching and persistent.
- Financial instability: Victims may experience long-term financial difficulties due to fraudulent transactions and the costs of recovery.
- Identity theft: Stolen personal information can be used to open fraudulent accounts, obtain loans, or commit other identity theft crimes, causing years of hardship.
- Reputational damage: The impact on personal or professional reputation can be lasting, affecting future opportunities and relationships.
- Psychological distress: Victims may experience anxiety, stress, and depression due to the invasion of privacy and the consequences of the attack.
- Legal and regulatory challenges: Victims may face ongoing legal battles or regulatory scrutiny due to the breach.
Concluding Remarks
Source: dmcdn.net
Legion Stealer V1 isn’t just a piece of malicious code; it’s a stark reminder of the ever-present threat in the digital age. Understanding its mechanics, from infection to data theft, is crucial for effective prevention. By staying informed and implementing robust security measures, you can significantly reduce your risk and protect your valuable data. The fight against malware is ongoing, and knowledge is your most powerful weapon.





