APT hackers leverage macOS Flutter apps, exploiting vulnerabilities to infiltrate systems. These seemingly innocuous applications can harbor sophisticated malware, bypassing security measures and stealing sensitive data. Understanding the attack vectors, data exfiltration methods, and mitigation strategies is crucial for safeguarding macOS environments from these advanced threats.
This exploration delves into the specific security risks inherent in Flutter apps on macOS, detailing how malicious actors can exploit common flaws to gain unauthorized access. We’ll examine the techniques used to conceal malicious code, bypass security mechanisms, and exfiltrate data, alongside practical strategies for developers and users to enhance security and mitigate risks.
macOS Flutter App Security Vulnerabilities
Flutter’s cross-platform capabilities, while offering significant development advantages, introduce unique security challenges when building macOS applications. Understanding these vulnerabilities is crucial for developers to build secure and robust apps. Neglecting security best practices can leave macOS Flutter apps vulnerable to a range of attacks, from data breaches to complete system compromise.
Flutter apps, like any software, are susceptible to various security flaws. These vulnerabilities can stem from insecure coding practices, improper handling of sensitive data, or weaknesses in the underlying Flutter framework itself. Exploiting these weaknesses can lead to significant consequences, ranging from simple data leaks to full-blown application hijacking. The ease of cross-platform development can sometimes overshadow the need for platform-specific security considerations.
Common Security Flaws in macOS Flutter Apps
Several common security flaws plague macOS Flutter apps. These include insecure data storage (leaving sensitive information unprotected in easily accessible locations), improper input validation (allowing malicious input to crash the application or execute arbitrary code), and insecure network communication (failing to encrypt data transmitted over networks, leaving it vulnerable to eavesdropping). Furthermore, the use of outdated or vulnerable third-party libraries can introduce additional attack vectors. These vulnerabilities can be exploited by attackers to gain unauthorized access to user data, install malware, or even take control of the affected system.
Methods of Obfuscating Malicious Code
Attackers employ various techniques to hide malicious code within Flutter apps. One common method involves packing the malicious code within seemingly benign libraries or plugins. This obfuscation makes it difficult to detect the malicious code through simple static analysis. Another approach is to use code encryption, where the malicious code is encrypted and decrypted only at runtime, making it harder to reverse engineer. Sophisticated attackers might even use polymorphism, altering the code’s structure to evade detection by signature-based antivirus software. The dynamic nature of Flutter apps, with code compilation happening during runtime, presents additional challenges in detecting such malicious activities.
Comparison of Security Risks: Native macOS Apps vs. Flutter Apps
The security risks associated with native macOS apps and Flutter apps differ, though both are vulnerable to various attacks. A crucial difference lies in the complexity of the development ecosystem and the potential for vulnerabilities introduced by third-party libraries.
| Vulnerability Type | Native App Risk | Flutter App Risk | Mitigation Strategy |
|---|---|---|---|
| Insecure Data Storage | Medium (depends on implementation) | Medium to High (potential for cross-platform vulnerabilities) | Use Keychain for sensitive data, encrypt data at rest |
| Improper Input Validation | Medium | Medium to High (easier to introduce flaws in cross-platform code) | Validate all user inputs rigorously, sanitize data before use |
| Insecure Network Communication | Medium | Medium to High (potential for vulnerabilities in network libraries) | Use HTTPS, implement proper certificate pinning |
| Third-Party Library Vulnerabilities | Medium (depends on library choices) | High (larger attack surface due to cross-platform libraries) | Regularly update libraries, perform security audits of dependencies |
| Code Injection | Low (with proper sandboxing) | Medium (potential vulnerabilities in Dart runtime or plugins) | Secure coding practices, regular security audits |
Attack Vectors for Compromising macOS Systems via Flutter Apps: Apt Hackers Leverage Macos Flutter Apps

Source: arstechnica.net
Malicious actors are increasingly leveraging the cross-platform capabilities of Flutter to create sophisticated attacks targeting macOS users. These apps, seemingly benign, can conceal a range of attack vectors, exploiting vulnerabilities in the system and user behavior to gain unauthorized access. Understanding these attack methods is crucial for bolstering macOS security.
Flutter apps, due to their access to system resources through native plugins, offer a unique entry point for malicious code. This access, while intended for legitimate functionality, can be exploited to bypass macOS’s built-in security measures, leading to data breaches, system compromise, and other severe consequences. The seemingly innocuous nature of a well-designed Flutter app makes it an ideal Trojan horse for cybercriminals.
Exploiting Native Plugin Vulnerabilities
Malicious Flutter apps can exploit vulnerabilities within native plugins—the bridge between Flutter code and macOS system functionalities. These plugins, often developed by third-party developers, may contain security flaws that attackers can leverage. For example, a plugin designed for accessing the user’s contacts could be manipulated to grant the app access to other sensitive data, like passwords stored in the keychain. A compromised plugin can act as a backdoor, allowing the attacker remote access and control over the affected system. This highlights the importance of using vetted and regularly updated plugins.
Bypass of macOS Gatekeeper
Gatekeeper, Apple’s built-in security mechanism, is designed to prevent the execution of unauthorized or malicious software. However, sophisticated attacks can circumvent Gatekeeper. One method involves disguising the malicious code within seemingly legitimate app bundles. The attacker might embed malicious code within the app’s resources, obfuscating it to avoid detection by Gatekeeper’s static analysis. Another technique is to exploit vulnerabilities in Gatekeeper itself, if any exist, to bypass its checks altogether. Successful circumvention grants the malicious app unrestricted access to the system.
Social Engineering Tactics
Social engineering plays a critical role in the success of these attacks. Attackers often use deceptive techniques to trick users into installing malicious Flutter apps. This might involve creating apps that mimic popular or trusted applications, employing fake app store listings or employing phishing campaigns that lure users to download compromised versions. For instance, a fake “productivity app” might promise enhanced features, while secretly installing malware capable of keylogging or data exfiltration. The user’s trust becomes the attacker’s greatest weapon.
Stages of a Successful Attack (Flowchart Description)
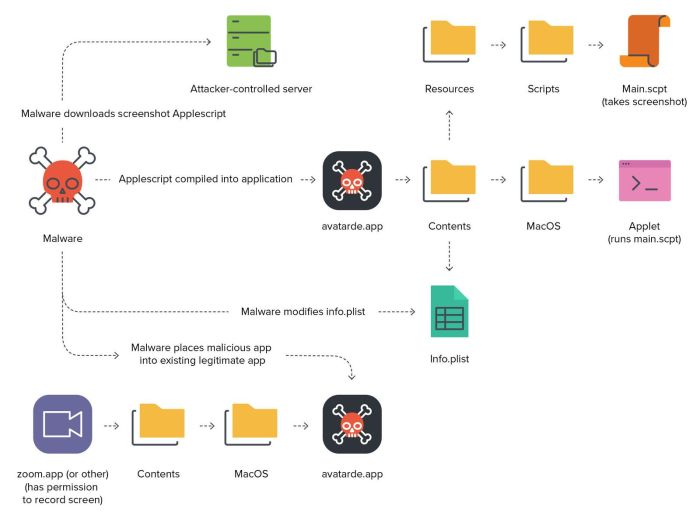
Imagine a flowchart illustrating the attack. It begins with the attacker crafting a malicious Flutter app, incorporating a compromised plugin or exploiting a Gatekeeper vulnerability. The next stage involves a social engineering campaign, like a deceptive app store listing or phishing email, to trick the user into downloading and installing the app. Once installed, the app gains access to system resources through the compromised plugin or Gatekeeper bypass. The attacker then uses this access to perform malicious actions, such as data theft, system takeover, or installing additional malware. The final stage shows the attacker exfiltrating the stolen data or maintaining persistent access to the compromised system. The entire process is designed to be seamless and undetectable to the unsuspecting user.
Malware Delivery and Execution within Flutter Apps
Flutter’s cross-platform capabilities, while beneficial for developers, unfortunately also present a tempting target for malicious actors. A seemingly innocuous Flutter app can easily conceal sophisticated malware, leveraging the platform’s architecture to achieve stealthy execution and persistence on a victim’s macOS system. This section delves into the techniques used to embed, execute, and evade detection of such malicious payloads.
The process begins with the embedding of malicious code within the Flutter application’s source code itself. This can involve modifying legitimate libraries, injecting custom code into existing functions, or even creating entirely new, hidden functionalities. Once installed, the app might appear completely normal, but its underlying code contains instructions to download and execute further malicious components. This staged approach enhances the malware’s ability to evade detection by security software.
Methods for Downloading and Installing Additional Malware Components
After initial installation, the malicious Flutter app often employs various techniques to download and install additional malware components. This might involve using compromised network requests to fetch malware from a remote server controlled by the attacker. These requests could be cleverly disguised as legitimate updates or data downloads, making them harder to identify. Alternatively, the app could use obfuscated code to decode and execute malicious payloads embedded within its resources, such as images or configuration files. This layered approach makes reverse engineering and analysis considerably more challenging.
Techniques for Evading Antivirus Software
Malware authors employ several sophisticated techniques to evade detection by antivirus software. These include polymorphism, where the malware’s code is constantly changing to avoid signature-based detection, and code obfuscation, which makes the malicious code difficult to understand and analyze. Packing the malware within encrypted containers or using advanced anti-debugging techniques further complicates detection efforts. The use of legitimate software libraries for malicious purposes – a technique known as “living off the land” – can also make the malware blend seamlessly into the system’s normal activity.
Common Payload Types Delivered Through Compromised Flutter Apps
The payloads delivered through compromised Flutter apps can vary widely depending on the attacker’s goals. However, some common types include:
- Keyloggers: These record user keystrokes, capturing sensitive information like passwords, credit card details, and personal communications.
- Ransomware: This encrypts the victim’s files, demanding a ransom for their release. Recent ransomware attacks have targeted individuals and organizations alike, causing significant financial and data losses.
- Remote Access Trojans (RATs): These provide attackers with remote control over the victim’s system, allowing them to steal data, install further malware, or manipulate system settings. RATs can be particularly devastating, providing persistent access to compromised systems.
- Information stealers: These malware variants focus on exfiltrating specific types of sensitive data, such as financial information, credentials, or intellectual property. Their actions can be highly targeted, depending on the attacker’s objectives.
- Cryptominers: These use the victim’s computing power to mine cryptocurrency, often without the user’s knowledge or consent. This can lead to performance degradation and increased electricity bills.
Data Exfiltration Methods Used by APT Hackers

Source: squarespace.com
Advanced Persistent Threat (APT) groups are sophisticated actors, and their methods for stealing data from compromised systems are equally complex. A malicious Flutter app on a macOS system provides a stealthy and effective vector for data exfiltration, allowing attackers to bypass traditional security measures. The techniques employed often leverage established infrastructure and encryption to remain undetected for extended periods.
Data exfiltration from a compromised macOS system via a malicious Flutter app typically involves several stages. First, the app gains access to sensitive data. Then, it uses various methods to transmit this data to a command-and-control (C2) server controlled by the attackers. Finally, the exfiltrated data is often concealed to hinder detection.
Command-and-Control Server Communication
The most common method of data exfiltration involves establishing a covert communication channel between the malicious Flutter app and a remote C2 server. This server acts as a central hub, receiving stolen data and providing further instructions to the compromised system. The communication channel can be established using various protocols, including HTTPS, which makes it difficult to distinguish from legitimate network traffic. Attackers might use techniques like domain generation algorithms (DGAs) to generate dynamic domain names for their C2 servers, making them harder to block. The data transmitted is often encrypted to further obscure its content. For example, the app might use AES-256 encryption before sending the data to the C2 server, making interception and decryption challenging without the decryption key.
Encrypted Channels and Tunneling
APT groups frequently employ encrypted channels to protect exfiltrated data during transit. This encryption ensures that even if the data is intercepted, it remains unreadable without the decryption key. Techniques like VPN tunneling can create a secure, encrypted connection between the compromised system and the C2 server, masking the exfiltrated data within legitimate network traffic. Furthermore, the use of steganography, which involves hiding data within other data, such as images or audio files, provides an additional layer of obfuscation. The malicious Flutter app might embed the stolen data within seemingly innocuous files before transferring them to the C2 server.
Data Concealment Techniques, Apt hackers leverage macos flutter apps
To evade detection, APT groups use various methods to conceal exfiltrated data. Data compression techniques reduce the size of the exfiltrated data, making it less conspicuous. Data can also be fragmented and sent in multiple small packets, making it harder to identify a pattern of malicious activity. Additionally, the use of decoy data or the embedding of stolen data within larger, legitimate files can further complicate detection efforts. The timing of data exfiltration is also carefully planned; data might be sent at off-peak hours or in small bursts to avoid detection by intrusion detection systems.
Data Exfiltration Channels and Detection Challenges
| Exfiltration Method | Detection Difficulty |
|---|---|
| HTTPS communication to a C2 server | High. Blends seamlessly with legitimate traffic. Requires deep packet inspection and behavioral analysis. |
| Encrypted VPN tunneling | Very High. Encrypts all traffic, making it difficult to identify malicious data within the tunnel. |
| Steganography (data hidden in images/audio) | High. Requires specialized tools and techniques to detect hidden data. |
| Data fragmentation and small packet transmission | Moderate. Can be detected by analyzing network traffic patterns. |
| Use of decoy data | High. Requires sophisticated analysis to differentiate between legitimate and malicious data. |
Mitigation Strategies and Best Practices
Securing macOS Flutter apps against sophisticated attacks requires a multi-layered approach encompassing development practices, code hardening, and robust security tools. Ignoring these best practices leaves your application vulnerable to exploitation by advanced persistent threats (APTs). Let’s explore practical strategies developers can implement to bolster their app’s security posture.
Building secure Flutter apps for macOS demands proactive measures throughout the development lifecycle. This goes beyond simply writing functional code; it necessitates a security-first mindset integrated into every stage, from design to deployment. Failing to address security vulnerabilities early can lead to costly remediation efforts later and potentially severe reputational damage.
Code Signing and Sandboxing
Code signing digitally verifies the authenticity and integrity of your application. This prevents malicious actors from tampering with your app and distributing modified versions. A digitally signed app reassures users that the software they are installing comes directly from the trusted developer. Sandboxing, on the other hand, confines the app’s operations to a restricted environment, limiting its access to system resources and preventing it from causing widespread damage even if compromised. By combining code signing with sandboxing, you create a significant barrier against malicious activity. For example, a sandboxed application might only have access to specific files or network ports, preventing unauthorized access to sensitive data or system-level operations.
Secure Data Handling Practices
Protecting sensitive user data is paramount. Implement robust encryption for data both in transit and at rest. Use established cryptographic libraries and follow best practices for key management. Avoid storing sensitive information directly within the app’s code or local storage unless absolutely necessary. If storage is unavoidable, ensure it’s encrypted using a strong, industry-standard algorithm. For example, never store passwords in plain text; always hash them using a strong one-way hashing algorithm like bcrypt or Argon2. Regularly review and update your data handling practices to stay ahead of evolving threats.
Security Tools and Techniques
A comprehensive security strategy includes proactive monitoring and detection capabilities. Utilize static and dynamic code analysis tools to identify potential vulnerabilities early in the development process. Regularly conduct penetration testing to simulate real-world attacks and assess your app’s resilience. Implement robust logging and monitoring to detect suspicious activity. Integrate security features into your app’s design, such as input validation and output encoding, to prevent common vulnerabilities like cross-site scripting (XSS) and SQL injection. Employ application monitoring services to detect anomalies in app behavior that could indicate malicious activity. Staying informed about the latest security threats and vulnerabilities is crucial for proactively addressing potential risks.
Case Studies of APT Attacks Leveraging macOS Flutter Apps (Hypothetical)
Source: arstechnica.net
The increasing sophistication of Advanced Persistent Threats (APTs) necessitates exploring potential attack vectors, including seemingly benign applications like those built with Flutter. This hypothetical case study illustrates how a compromised macOS Flutter app could be weaponized for malicious purposes.
Operation “Silent Bloom”: A Hypothetical APT Attack
Operation Silent Bloom targeted high-profile executives within a multinational technology firm. The attackers, suspected to be a state-sponsored group, aimed to steal intellectual property and sensitive business strategies. Their chosen vector: a seemingly innocuous productivity app, “TaskMaster,” developed using Flutter and distributed through a compromised software repository. TaskMaster offered features such as task management, calendar synchronization, and note-taking – functions perfectly aligning with the target executives’ professional needs.
Attacker Motives, Techniques, and Objectives
The attackers’ primary motive was industrial espionage. Their techniques involved compromising the legitimate developer’s account on the software repository, replacing the authentic TaskMaster binary with a malicious version. The objective was to gain persistent access to the victim’s systems, exfiltrate data, and maintain a covert presence for future operations. This approach leverages the trust placed in legitimate app stores and the perceived safety of well-known development frameworks like Flutter.
Impact on the Victim
The malicious TaskMaster app, upon installation, established persistence by registering a launch agent. This ensured that the app would automatically launch upon system startup. The malware then used various techniques to exfiltrate sensitive data, including screenshots, clipboard contents, and files accessed by the victim. This led to a significant breach of confidential information, impacting the company’s competitive advantage and potentially exposing sensitive customer data. The long-term impact included reputational damage, financial losses, and the disruption of ongoing projects.
Malicious Flutter App Functionality
The core malicious functionality of TaskMaster was concealed within seemingly benign features. For example, the calendar synchronization feature secretly uploaded calendar events and associated notes to a remote server controlled by the attackers. The note-taking function similarly allowed for the exfiltration of sensitive documents. The app also included a hidden command-and-control (C2) component that allowed the attackers to remotely execute commands on the victim’s system, providing complete control and the ability to install additional malware. The malicious code was obfuscated and designed to evade detection by standard antivirus software. This highlights the difficulty in identifying and mitigating attacks targeting well-established, seemingly safe platforms like Flutter.
Summary
The threat landscape is constantly evolving, and malicious actors are increasingly leveraging the versatility of cross-platform frameworks like Flutter to target macOS systems. While Flutter offers significant advantages for developers, understanding and mitigating the inherent security risks is paramount. By implementing robust security practices and staying informed about emerging threats, individuals and organizations can significantly reduce their vulnerability to APT attacks exploiting macOS Flutter applications.





