Malware analysis: It sounds intense, right? But understanding how malicious software works is crucial in today’s digital world. From sneaky viruses hiding in your emails to ransomware locking up your files, the world of malware is constantly evolving. This deep dive explores the different types of malware, how they spread, and the techniques used to detect and analyze them. We’ll unpack the methods used by cybercriminals, the tools used by security experts, and the strategies to protect yourself.
We’ll cover everything from the historical evolution of malware, showcasing its sneaky transformations over the years, to the cutting-edge techniques used to dissect and understand these digital menaces. We’ll delve into both static and dynamic analysis, examining the pros and cons of each approach. Get ready to uncover the secrets behind malware and learn how to stay one step ahead.
Introduction to Malware

Source: fortgale.com
The digital world, while offering incredible convenience and connection, also harbors a dark underbelly: malware. From simple annoyances to devastating attacks, malware has evolved alongside technology, constantly adapting and becoming more sophisticated. Understanding its history, types, and motivations is crucial for navigating the increasingly complex cybersecurity landscape. This section provides a foundational understanding of malware, its various forms, and the reasons behind its creation.
Malware Evolution and Forms, Malware analysis
Malware’s journey began with relatively simple viruses, self-replicating programs that spread by attaching themselves to other files. Over time, however, its complexity exploded. The emergence of the internet provided a vast network for rapid propagation, leading to the development of worms, which could spread independently across networks without needing to attach to other files. Trojans, disguised as legitimate software, opened the door to more insidious attacks. The rise of ransomware, which encrypts user data and demands payment for its release, marked a significant shift towards financially motivated attacks. More recently, we’ve seen the rise of sophisticated advanced persistent threats (APTs), which are often state-sponsored and designed to infiltrate systems undetected for extended periods, stealing sensitive information. This continuous evolution demands a constant adaptation in security measures.
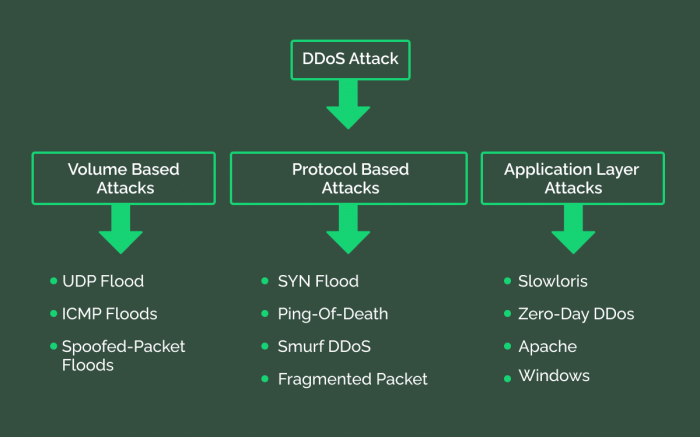
Common Malware Types
Understanding the different types of malware is crucial for effective prevention and response. The following table categorizes some of the most prevalent forms:
| Type | Description | Methods of Infection | Common Symptoms |
|---|---|---|---|
| Virus | Self-replicating program that attaches to other files. | Infected files, email attachments, infected websites. | System slowdowns, crashes, unexpected program behavior. |
| Worm | Self-replicating program that spreads independently across networks. | Network vulnerabilities, email attachments, infected websites. | Network congestion, slow internet speeds, system crashes. |
| Trojan | Malicious program disguised as legitimate software. | Deceptive downloads, email attachments, infected websites. | Unexpected program behavior, data theft, system instability. |
| Ransomware | Encrypts user data and demands a ransom for its release. | Phishing emails, infected websites, malicious software downloads. | Data inaccessibility, ransom demands, system lockouts. |
| Spyware | Secretly monitors user activity and collects personal information. | Infected websites, malicious software downloads, bundled software. | Slow computer performance, unusual pop-ups, unexplained network activity. |
| Adware | Displays unwanted advertisements. | Infected websites, bundled software, freeware downloads. | Excessive pop-up ads, browser redirects, altered search results. |
Motivations Behind Malware Creation
The creation of malware is driven by a range of motivations, often overlapping and interconnected. Financial gain is a primary driver, with ransomware attacks and cryptojacking (using a victim’s computer to mine cryptocurrency) being prime examples. Espionage is another significant factor, with APTs often employed by nation-states or corporations to steal intellectual property, trade secrets, or other sensitive information. Finally, sabotage, whether for political reasons, revenge, or competitive advantage, can also lead to the creation and deployment of malware designed to disrupt operations, damage systems, or steal data. The NotPetya ransomware attack, which caused billions of dollars in damages, is a stark example of the devastating consequences of such malicious activity.
Malware Infection Vectors
Malware, that sneaky digital gremlin, finds its way onto your system through various cunning routes. Understanding these infection vectors is crucial for bolstering your defenses and keeping your digital life safe. It’s like knowing the enemy’s tactics – only then can you effectively counter their attacks. This section explores the common pathways malware uses to infiltrate your computer or network.
The methods used by malicious actors are constantly evolving, becoming more sophisticated and harder to detect. However, many infections still rely on well-established techniques that exploit human behavior and software vulnerabilities.
Phishing Emails
Phishing emails are a classic malware delivery method. These deceptive messages often mimic legitimate communications from banks, online retailers, or other trusted sources. They typically contain malicious attachments or links designed to trick recipients into downloading malware or revealing sensitive information. For example, an email might appear to be from your bank, urging you to update your account details by clicking a link that leads to a fake login page designed to steal your credentials. This stolen information can then be used to access your accounts or to spread malware further. Sophisticated phishing campaigns may even incorporate personalized details gleaned from data breaches to increase their credibility.
Malicious Websites
Visiting compromised or malicious websites can expose your system to malware. These sites may contain hidden exploits that automatically download and install malware onto your computer without your explicit consent. Drive-by downloads are a common tactic, where simply visiting the site triggers the infection. This can happen even if you don’t click on any links or download any files. The malware may exploit vulnerabilities in your browser or operating system to gain access. Poorly maintained or outdated software is particularly vulnerable to these attacks.
Infected Software Downloads
Downloading software from untrusted sources is a risky business. Malicious actors often disguise malware as legitimate software, hiding it within seemingly harmless downloads. This can include cracked software, pirated games, or other applications obtained from unofficial sources. The malware may be bundled with the desired software or injected into the installer itself. Always download software from official websites and reputable sources to minimize this risk. Check the software’s digital signature to verify its authenticity whenever possible.
Removable Media
Infected USB drives, external hard drives, and other removable media can easily spread malware. Simply plugging an infected device into your computer can trigger an automatic infection. This is especially risky if your computer is configured to auto-run files from removable media. Many malware infections in corporate environments occur through this method, often due to employees using personal USB drives or connecting to devices from untrusted sources. Implementing strong security policies regarding removable media usage can significantly reduce this risk.
Social Engineering Tactics
Social engineering leverages psychological manipulation to trick individuals into revealing sensitive information or taking actions that compromise their security. This can involve various tactics, such as creating a sense of urgency, building trust, or exploiting emotions. For example, a scammer might pose as a tech support representative, claiming to detect a problem on your computer and guiding you through steps that actually install malware. Another tactic involves exploiting fear, such as sending an email claiming that your account has been compromised unless you immediately click a link to verify your information. These sophisticated methods rely on exploiting human psychology to bypass technical security measures.
Malware Infection Process Flowchart
Imagine a flowchart with the following stages:
1. Initial Contact: The malware makes initial contact with the target system, perhaps through a phishing email or malicious website.
2. Exploitation: The malware exploits a vulnerability in the system’s software or user behavior.
3. Installation: The malware installs itself on the system, often hiding its presence.
4. Execution: The malware executes its malicious code, carrying out its intended actions (data theft, system damage, etc.).
5. Persistence: The malware establishes persistence, ensuring it remains on the system even after a reboot.
6. Communication: The malware communicates with a command-and-control server to receive further instructions.
7. Action: The malware carries out its intended malicious actions.
Malware Detection Techniques
Unmasking malicious software requires a multi-layered approach. Effective malware detection relies on a combination of techniques, each with its strengths and weaknesses. Understanding these methods is crucial for building robust security systems. This section explores signature-based and heuristic-based detection, the vital role of sandboxing and emulation, and finally, Artikels a hypothetical, yet practical, malware detection system.
Signature-Based Detection
Signature-based detection, the oldest method in the book, works by identifying known malware through unique patterns – signatures – within its code. Think of it like a fingerprint for malware. These signatures are typically created by analyzing known malicious samples and extracting characteristic strings of code or specific file structures. Antivirus software uses these signatures to scan files and processes, flagging anything that matches a known malicious signature. The simplicity and speed of this method make it a cornerstone of many security solutions. However, it suffers from a significant limitation: it’s only effective against already known malware. Zero-day exploits, or newly created malware, easily evade signature-based detection.
Heuristic-Based Detection
Heuristic-based detection takes a different approach. Instead of relying on known signatures, it analyzes the behavior of a program to identify suspicious activities. This method focuses on identifying patterns of behavior indicative of malware, such as attempts to access system files, unusual network connections, or self-replication. Heuristic engines look for red flags – suspicious actions – rather than specific code sequences. This makes them more effective against zero-day threats than signature-based detection, but they can also produce false positives, flagging benign programs as malicious.
The Role of Sandboxing and Emulation
Sandboxing and emulation are crucial for analyzing malware safely. Sandboxing involves running a suspicious program in an isolated environment, preventing it from accessing or modifying the host system. This allows analysts to observe its behavior without risking damage to the main system. Emulation takes this a step further, creating a virtualized environment that mimics the target system’s hardware and software. This allows for the analysis of malware that might not run correctly in a standard sandbox. By combining sandboxing and emulation, analysts can gain a detailed understanding of a malware sample’s functionality and behavior, allowing for the creation of effective detection methods and countermeasures. For example, a sophisticated piece of malware might only reveal its true nature within a specific operating system version or under specific network conditions, which emulation can perfectly recreate.
Hypothetical Malware Detection System
A robust malware detection system needs multiple layers of defense. Our hypothetical system would combine signature-based and heuristic-based detection with sandboxing and machine learning. The system would consist of:
- A Signature Database: A constantly updated database of known malware signatures.
- A Heuristic Engine: An engine capable of identifying suspicious behavior patterns based on system calls, network activity, and file modifications.
- A Sandboxing Environment: A secure, isolated environment for analyzing suspicious files.
- A Machine Learning Component: A machine learning algorithm trained on both benign and malicious samples to improve the accuracy of heuristic-based detection and identify emerging threats.
- A Centralized Management Console: A console to manage the system, view alerts, and analyze results.
This multi-layered approach ensures that the system can detect both known and unknown malware, minimizing false positives and providing comprehensive protection. The machine learning component would continuously learn and adapt, improving the system’s accuracy over time. This is vital in the ever-evolving landscape of malware.
Static Malware Analysis
Static malware analysis is like a digital autopsy – you examine the malware without actually running it. This non-intrusive approach allows security researchers to get a good understanding of the malware’s capabilities and behavior without risking infection. It’s a crucial first step in the malware analysis process, providing valuable context before moving on to more dynamic techniques.
Static analysis involves inspecting the malware’s code, structure, and metadata to identify suspicious patterns and potential threats. This can reveal things like the malware’s functionality, the techniques it uses to evade detection, and the potential damage it could inflict. However, it’s important to remember that static analysis alone isn’t foolproof; it can miss certain aspects of malware behavior that only become apparent during execution.
The Process of Static Malware Analysis
Static analysis typically begins with gathering information about the sample, such as its file type, size, and timestamps. Next, the analyst uses various tools to dissect the code, looking for telltale signs of malicious activity. This might involve examining the code’s structure, identifying strings and API calls, and searching for known malicious patterns. The results of this analysis are then interpreted to form a comprehensive understanding of the malware’s capabilities and potential impact.
Performing Static Analysis: A Step-by-Step Guide
Let’s walk through a typical static analysis workflow using common tools. Remember, always perform this analysis in a controlled, isolated environment (like a virtual machine) to prevent accidental infection.
- Obtain the Malware Sample: Securely acquire the malware sample, ensuring its integrity is maintained. This often involves using a sandboxed environment.
- Hashing and Identification: Calculate the MD5, SHA1, and SHA256 hashes of the sample. These hashes can be used to quickly identify the sample in various threat intelligence databases.
- File Type and Metadata Examination: Determine the file type (e.g., EXE, DLL, PDF) using tools like `file` (Linux/macOS) or similar utilities on Windows. Examine file metadata for suspicious information such as unusual timestamps or authors.
- Disassembly: Use a disassembler like IDA Pro or Ghidra to convert the malware’s machine code into assembly language. This allows for detailed examination of the code’s instructions and logic.
- String Extraction: Employ string extraction tools (often built into disassemblers) to identify text strings within the malware. These strings can reveal clues about the malware’s purpose, targets, or communication channels.
- Import/Export Table Analysis: Examine the import and export tables (if applicable) to identify the libraries and functions the malware uses. This can reveal its capabilities and potential actions.
- Code Analysis: Manually analyze the disassembled code, looking for suspicious patterns, known malicious functions, or indicators of compromise (IOCs).
Comparison of Static Analysis Tools
Different tools offer various features and capabilities. Choosing the right tool depends on your expertise and the specific needs of the analysis.
| Tool | Features | Strengths | Weaknesses |
|---|---|---|---|
| IDA Pro | Powerful disassembler, debugger, and scripting capabilities; extensive plugin ecosystem. | Highly accurate disassembly, advanced analysis features, large community support. | Expensive, steep learning curve. |
| Ghidra | Free and open-source disassembler, debugger, and decompiler; supports multiple architectures. | Free to use, active development, growing community. | Can be less user-friendly than IDA Pro for beginners. |
| PEiD | Identifies packers, compilers, and other characteristics of PE files (Windows executables). | Fast and easy to use for initial analysis of Windows executables. | Limited analysis capabilities beyond identification of packers. |
| strings | A command-line utility that extracts printable strings from files. | Simple and effective for quickly finding potentially revealing strings. | Can produce a large number of irrelevant strings, requiring manual filtering. |
Dynamic Malware Analysis
Dynamic analysis is where the rubber meets the road in malware investigation. Unlike static analysis, which examines the malware without execution, dynamic analysis involves running the malware in a controlled environment to observe its behavior. This allows for a deeper understanding of its functionalities, network communications, and system interactions – revealing secrets that static analysis might miss. Think of it as watching a movie instead of just reading the script.
Dynamic analysis leverages several powerful tools, primarily debuggers and virtual machines (VMs). Debuggers allow step-by-step execution of the malware, providing granular control and visibility into its inner workings. VMs, on the other hand, create isolated environments where the malware can run without risking your primary system. This sandboxed approach is crucial for mitigating the risks associated with analyzing potentially harmful code.
Debugger Usage in Dynamic Malware Analysis
Debuggers are indispensable tools in dynamic analysis. They allow analysts to set breakpoints at specific points in the code, step through the instructions one by one, inspect registers and memory, and examine the program’s state at various points during execution. This detailed level of scrutiny is essential for identifying malicious actions such as registry modifications, file system alterations, or network connections. For example, a debugger can reveal exactly which API calls a malware sample uses to connect to a command-and-control server, providing critical information for understanding its operational methods. Imagine watching the malware’s every move, seeing precisely which files it accesses and what changes it makes.
Safe Malware Analysis in a Controlled Environment
Safe and effective dynamic analysis relies heavily on the use of virtual machines. VMs offer a critical layer of protection, isolating the malware from your host system. Best practices include using a dedicated, up-to-date antivirus solution within the VM, regularly creating snapshots of the VM’s state before analysis begins, and employing a network monitoring tool to observe the malware’s network activity. Furthermore, limiting the VM’s access to resources, such as network connectivity and access to sensitive files, minimizes the potential impact of a successful attack. Think of it as creating a virtual prison for the malware, preventing it from escaping and causing damage. A breach of the VM is far less damaging than a compromise of your primary system.
Tracing Execution Flow with a Debugger
Tracing the execution flow involves monitoring the order in which the program’s instructions are executed. Debuggers provide this functionality through features like stepping (executing one instruction at a time), stepping over (executing a function call without stepping into it), and stepping out (returning from a function call). By carefully observing the sequence of instructions and the changes in registers and memory, analysts can reconstruct the malware’s logic and identify key malicious actions. For instance, an analyst might set a breakpoint on a function known to write data to the disk and then step through the code to determine the exact contents of the data being written, revealing potential indicators of compromise. This detailed tracing provides a clear picture of the malware’s actions and intentions.
Reverse Engineering Techniques

Source: nixhacker.com
Reverse engineering malware is like peeling back the layers of an onion, revealing its inner workings to understand how it operates and what damage it can inflict. This process involves meticulously examining the malware’s code to identify its functions, behaviors, and ultimately, its malicious intent. By understanding its mechanics, we can develop more effective countermeasures and prevention strategies.
This process isn’t a simple task; it requires specialized tools and a deep understanding of assembly language and computer architecture. The goal is to decipher the malware’s actions, pinpoint its command-and-control servers, and ultimately, neutralize its threat. This involves several steps, from initial analysis to detailed code examination.
Disassembling Malware Code
Disassembly is the crucial first step in reverse engineering. It’s the process of converting machine code (the binary instructions a computer directly executes) into assembly language, a more human-readable representation. This allows analysts to examine the individual instructions the malware executes, tracing the flow of control and identifying key functions. Tools like IDA Pro, Ghidra, and radare2 are commonly used for this purpose. These tools provide a visual representation of the code, often displaying it in a graphical format, making it easier to follow the execution path. For example, IDA Pro’s powerful graph view allows analysts to visualize the program’s control flow, highlighting functions and call relationships, making it easier to pinpoint malicious behavior. This graphical representation helps to understand the logic behind the malware’s operations and helps to identify key functions such as network communication, file encryption, or registry manipulation. The process involves navigating through various code sections, identifying function calls, and analyzing data structures.
Identifying Key Functions
Once the malware is disassembled, the next step is to identify its key functions. This involves analyzing the assembly code to understand what each function does. Analysts look for patterns and common malware techniques. For instance, functions that make network connections might indicate communication with a command-and-control server, while functions that modify system files or registry settings could indicate attempts to compromise the system. String analysis, searching for specific text strings within the malware, can also be helpful in identifying the malware’s purpose. For example, finding strings related to specific file types or network addresses can provide valuable clues about the malware’s actions. Additionally, the use of common malware libraries or functions can be identified, indicating the use of pre-existing malware components. This can speed up the analysis process by identifying known malicious behavior.
Common Reverse Engineering Tools
Several tools aid in reverse engineering. IDA Pro, a commercial disassembler, is widely considered the industry standard, known for its powerful features and extensive plugin ecosystem. Ghidra, a free and open-source alternative developed by the NSA, offers similar capabilities and a growing community of users. Radare2, another open-source tool, is highly versatile and command-line driven, allowing for scripting and automation. These tools facilitate navigating through the code, setting breakpoints, and examining memory contents, crucial for understanding the malware’s dynamic behavior. They provide features such as debugging capabilities, allowing analysts to step through the code execution and observe changes in memory and registers. Furthermore, these tools often include powerful scripting capabilities, allowing for automation of repetitive tasks and the development of custom analysis scripts.
Malware Analysis Tools and Resources
Navigating the complex world of malware analysis requires the right tools and resources. A skilled analyst needs more than just technical expertise; they need access to powerful software and readily available information to effectively dissect malicious code and understand its behavior. This section explores a selection of both open-source and commercial tools, highlighting their strengths and weaknesses, along with key online resources that bolster a malware analyst’s arsenal.
The choice of tools often depends on the specific task at hand and the analyst’s experience level. Some tools excel at static analysis (examining the code without execution), while others are better suited for dynamic analysis (observing the malware’s behavior during runtime). A comprehensive approach typically involves a combination of both.
Open-Source Malware Analysis Tools
Open-source tools offer a cost-effective and often highly customizable approach to malware analysis. These tools are continuously improved by a global community of researchers, leading to frequent updates and feature enhancements. Their accessibility fosters collaboration and knowledge sharing within the security community.
- Ghidra: A powerful, free, and open-source software reverse engineering (SRE) suite from the NSA. Ghidra provides a comprehensive set of tools for disassembling, decompiling, and analyzing binaries. Its user-friendly interface and extensive plugin ecosystem make it a favorite among both novice and experienced analysts. Imagine a sophisticated code editor, but specifically designed to dissect malware; Ghidra offers this and more.
- Radare2: A highly versatile, command-line-based framework for reverse engineering. Radare2 is exceptionally powerful but demands a steeper learning curve. Its flexibility and scripting capabilities allow for highly customized analysis workflows. Think of it as a Swiss Army knife for malware analysis – highly adaptable, but requiring some skill to master.
- Cuckoo Sandbox: An automated malware analysis platform that executes suspicious files in a controlled environment and monitors their behavior. Cuckoo Sandbox provides detailed reports on the malware’s actions, network connections, and registry modifications. This is invaluable for understanding the malware’s full impact and potential damage.
Commercial Malware Analysis Tools
Commercial tools often offer more advanced features, automated analysis capabilities, and dedicated support. The cost can be significant, but the time saved and increased efficiency can justify the investment for organizations with substantial malware analysis needs.
- Any.Run: A cloud-based malware analysis service that provides automated and detailed reports on submitted samples. Any.Run allows for analysis of various file types and offers advanced features like behavioral analysis and network traffic monitoring, offering a streamlined approach to threat assessment.
- VirusTotal: While not strictly a malware analysis tool, VirusTotal is an invaluable resource that allows users to submit files for scanning by multiple antivirus engines. The aggregated results provide a quick overview of the file’s reputation and potential maliciousness. It acts as a first line of defense, giving a quick assessment before deeper analysis.
Valuable Online Resources for Malware Researchers
Access to information is critical for effective malware analysis. Several online resources provide crucial data, support, and collaboration opportunities for researchers.
- Malware Databases (e.g., VirusShare, Contagio Malware Dump): These repositories contain samples of malware that researchers can use for analysis and practice. Accessing these databases allows for hands-on experience with real-world threats, enabling analysts to hone their skills and stay up-to-date with the latest malware trends.
- Security Forums (e.g., MalwareTech, SANS Institute): These forums provide platforms for researchers to share information, ask questions, and collaborate on challenging analysis tasks. The collective knowledge and experience within these communities is an invaluable resource.
- Documentation and Research Papers (e.g., publications from security companies, academic institutions): These resources provide in-depth information on various malware analysis techniques, tools, and threat landscapes. Staying current with the latest research is essential for maintaining proficiency in this ever-evolving field.
Case Studies of Notable Malware
Understanding the impact and techniques employed by notorious malware families is crucial for effective cybersecurity. Analyzing these cases reveals common infection vectors, evasion techniques, and the devastating consequences they can inflict. This section delves into several prominent examples, highlighting key characteristics and analysis processes.
Several notable malware families have left their mark on the digital landscape, demonstrating a constant evolution in their sophistication and impact. Studying these cases provides invaluable insights into the ever-changing threat landscape.
Stuxnet Analysis
Stuxnet, a sophisticated worm targeting Iranian nuclear facilities, represents a landmark case in advanced persistent threat (APT) attacks.
- Malware Name: Stuxnet
- Target: Iranian nuclear enrichment centrifuges
- Method of Infection: Spread through infected USB drives and network vulnerabilities.
- Consequences: Caused significant damage to Iranian centrifuges, setting back their nuclear program.
The analysis of Stuxnet revealed a multi-stage infection process. Initially, it exploited vulnerabilities in Windows systems to gain access. Subsequently, it used a sophisticated series of modules to identify and target specific industrial control systems (ICS) hardware. The malware then subtly altered the centrifuge’s operational parameters, causing them to malfunction without immediately triggering alarms. This meticulous approach, combined with its ability to self-propagate, made Stuxnet exceptionally dangerous and difficult to detect.
Comparison of Stuxnet and WannaCry
Stuxnet and WannaCry, while both impactful, employed distinctly different techniques. Stuxnet focused on highly targeted attacks against specific industrial systems, leveraging sophisticated, custom-built exploits. In contrast, WannaCry utilized a readily available exploit (EternalBlue) to achieve widespread infection, relying on brute-force and rapid propagation. Stuxnet’s impact was precisely targeted and significant within a limited scope, whereas WannaCry’s impact was broader but less precisely targeted, causing disruption across various sectors. Both demonstrated the potential for devastating consequences, highlighting the need for robust security measures.
WannaCry Ransomware
WannaCry, a globally impactful ransomware attack, demonstrated the devastating potential of widespread exploitation of vulnerabilities.
- Malware Name: WannaCry
- Target: Computers running vulnerable versions of Microsoft Windows
- Method of Infection: Exploited the EternalBlue exploit, spreading rapidly across networks.
- Consequences: Encrypted files on infected systems, demanding ransom for decryption. Caused widespread disruption to businesses and healthcare systems globally.
The analysis of WannaCry highlighted the critical importance of patching software vulnerabilities. The rapid spread of the ransomware underscored the potential for significant damage when a widely available exploit is combined with a self-propagating mechanism. The use of EternalBlue, a leaked NSA exploit, further emphasized the risks associated with the proliferation of such tools.
Mitigation and Prevention Strategies: Malware Analysis
Malware is a persistent threat, constantly evolving to bypass security measures. Effective mitigation and prevention strategies are crucial for safeguarding computer systems and sensitive data. A multi-layered approach, combining proactive measures with reactive responses, offers the best protection. This involves staying informed about emerging threats, implementing robust security practices, and regularly updating systems and software.
Proactive measures focus on preventing infections in the first place, while reactive measures deal with containing and removing malware once it has gained access. Both are equally important in a comprehensive security strategy. The effectiveness of these strategies depends on user awareness, system configuration, and the continuous monitoring of system behavior for any suspicious activities.
Regular Software Updates and Security Patches
Regular software updates are paramount in malware prevention. These updates often include security patches that address vulnerabilities exploited by malware. Outdated software presents an easy target for attackers, as known vulnerabilities remain unpatched. For example, the WannaCry ransomware attack in 2017 exploited a vulnerability in older versions of Microsoft Windows that had been patched months earlier. Failing to update leaves systems susceptible to such attacks. Automatic update features should be enabled whenever possible to ensure timely patching. This proactive approach minimizes the risk of infection significantly.
Best Practices for Securing Computer Systems
A comprehensive approach to computer security is essential. This includes a range of practices designed to minimize vulnerabilities and prevent malware infection.
The following checklist summarizes key best practices:
- Install and maintain robust antivirus software: Regularly update antivirus definitions and scan your system frequently.
- Enable automatic software updates: Ensure operating systems, applications, and drivers are up-to-date.
- Use strong and unique passwords: Avoid easily guessable passwords and use a password manager to securely store them.
- Enable firewall protection: A firewall acts as a barrier, blocking unauthorized access to your system.
- Be cautious when downloading files: Only download files from trusted sources and verify their integrity before execution.
- Avoid clicking suspicious links or attachments: Exercise caution with emails and messages from unknown senders.
- Educate users about phishing scams: Phishing emails often attempt to trick users into revealing sensitive information or downloading malware.
- Regularly back up important data: This helps recover data in case of a malware infection or system failure.
- Practice safe browsing habits: Avoid visiting untrusted websites and use caution when entering personal information online.
- Use multi-factor authentication (MFA) whenever possible: MFA adds an extra layer of security, making it more difficult for attackers to gain access to accounts.
Network Security Measures
Network security plays a crucial role in preventing malware infections. This involves implementing measures to secure network infrastructure and control access to systems and data.
Key network security measures include:
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can block or alert on suspicious behavior.
- Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a potential breach.
- Secure Wi-Fi Networks: Use strong passwords and encryption protocols (WPA2/3) for wireless networks.
- Regular Network Audits: Periodically assess network security to identify and address vulnerabilities.
Concluding Remarks

Source: cyfirma.com
So, there you have it – a whirlwind tour through the fascinating (and sometimes terrifying) world of malware analysis. While the landscape of cyber threats is constantly shifting, understanding the fundamentals of malware analysis is key to protecting yourself and your data. Remember, staying informed and proactive is your best defense against these digital villains. Keep learning, keep adapting, and keep your systems secure!