Bypassing chromes cookie protection – Bypassing Chrome’s cookie protection isn’t just for tech-savvy rebels; it’s a rabbit hole explored by both malicious actors and curious developers. This journey delves into the various methods used to circumvent Chrome’s increasingly robust cookie security, examining the techniques, risks, and ethical implications involved. We’ll dissect how extensions, network manipulations, and even clever coding can attempt to outsmart Chrome’s defenses, ultimately revealing the cat-and-mouse game between security and circumvention.
From exploiting vulnerabilities in browser extensions to manipulating network requests, we’ll uncover the diverse strategies employed to bypass Chrome’s cookie restrictions. This exploration will also delve into the potential consequences of these actions, including security breaches and privacy violations, and examine Chrome’s countermeasures designed to thwart such attempts. We’ll also consider the ethical and legal ramifications of engaging in such activities.
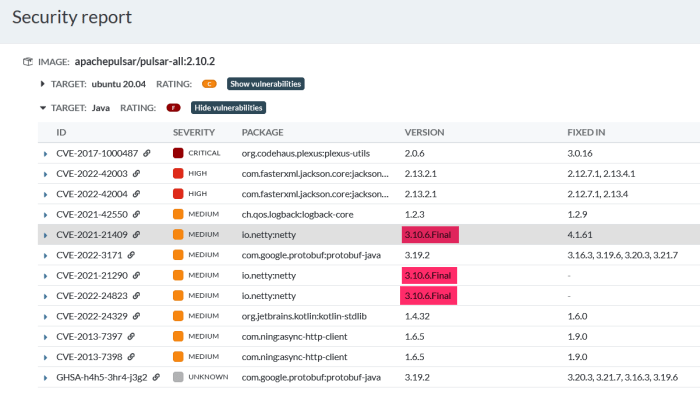
Methods of Circumventing Chrome’s Cookie Protection
Chrome’s increasingly robust cookie protection measures are designed to enhance user privacy and security. However, determined individuals and malicious actors may still seek ways to bypass these safeguards. Understanding these methods is crucial for both developers aiming to strengthen their security and users striving to maintain their online privacy.
Techniques for Bypassing Cookie Restrictions
Several techniques exist to attempt to circumvent Chrome’s cookie restrictions. These methods often involve manipulating browser settings, network requests, or exploiting vulnerabilities in extensions or third-party applications. It’s crucial to understand that many of these techniques are ethically questionable and may violate terms of service. Furthermore, attempting to bypass these security measures often exposes users to increased risks.
Manipulation of Browser Settings and Extensions
One common approach involves modifying browser settings to weaken or disable Chrome’s built-in cookie protection. This might include disabling third-party cookies, adjusting cookie lifespan settings, or utilizing extensions that claim to manage or override cookie behavior. However, these extensions themselves might pose security risks, potentially installing malware or compromising user data. Some extensions might claim to offer enhanced privacy, but they may actually collect and sell user data. Modifying browser settings directly can also lead to unexpected consequences, impacting website functionality and increasing vulnerability to tracking and malicious scripts.
Network Request Manipulation
Another method involves manipulating network requests to bypass cookie restrictions. This might involve using proxies or VPNs to mask the user’s IP address, altering HTTP headers to bypass cookie limitations, or using specialized tools to inject custom cookies into requests. These techniques can be difficult to implement and require a strong understanding of network protocols. Moreover, they are often easily detected by websites implementing robust anti-circumvention measures. The use of such methods can lead to account bans or legal repercussions.
Exploiting Vulnerabilities in Extensions or Third-Party Applications
Malicious extensions or third-party applications can sometimes exploit vulnerabilities in Chrome’s architecture to bypass cookie restrictions. These extensions may contain hidden code that manipulates cookies without the user’s knowledge or consent. Users should always exercise caution when installing extensions and only download them from reputable sources. Regular updates and security scans are essential to minimize risks associated with potentially malicious extensions.
Comparison of Methods
The following table compares the effectiveness, risk level, and detection difficulty of various methods for bypassing Chrome’s cookie protection. Note that effectiveness and detection difficulty can vary depending on the specific website and its security measures.
| Method | Effectiveness | Risk Level | Detection Difficulty |
|---|---|---|---|
| Modifying Browser Settings | Low to Moderate (depending on the setting) | Low to Moderate | Low |
| Using Extensions (legitimate or malicious) | Low to High (depending on the extension) | Moderate to High | Moderate to High |
| Network Request Manipulation (Proxies, VPNs, etc.) | Moderate to High | High | High |
| Exploiting Extension Vulnerabilities | High (if successful) | Very High | High |
Exploiting Browser Extensions and Plugins
Source: amazonaws.com
Browser extensions and plugins, while offering enhanced functionality, represent a significant security vulnerability when it comes to circumventing Chrome’s robust cookie protection. Their access to a wide range of browser data, including cookies, makes them attractive targets for malicious actors seeking to bypass security measures. Understanding how these extensions can be manipulated is crucial to maintaining online privacy and security.
Malicious extensions can compromise Chrome’s cookie handling through various methods, often exploiting the inherent trust users place in seemingly legitimate add-ons. These extensions can be designed to silently intercept and manipulate cookie data, transmitting sensitive information to external servers without the user’s knowledge or consent. This allows for unauthorized access to user accounts and sensitive data associated with those accounts.
Functionality of Malicious Extensions in Cookie Bypass
A malicious extension could contain code designed to specifically target and modify cookies. For instance, it might include a function that intercepts HTTP requests and responses, allowing it to read, modify, or delete cookies before they are processed by the browser. Another approach would be to inject JavaScript code into web pages, manipulating the document object model (DOM) to directly access and alter cookie values. This would allow the extension to bypass any client-side cookie protection mechanisms implemented by Chrome.
Security Implications of Untrusted Browser Extensions
Installing untrusted browser extensions exposes users to a wide range of security risks. These risks include, but are not limited to, data theft, malware infection, phishing attacks, and unauthorized access to sensitive information. Malicious extensions can secretly monitor browsing activity, collect personal data, and even install additional malware onto the user’s system. The consequences of such compromises can range from minor inconveniences to significant financial and reputational damage.
Hypothetical Malicious Extension: “CookieThief”
Imagine a hypothetical malicious extension called “CookieThief.” This extension would appear benign, perhaps offering a seemingly useful feature like ad blocking or password management. However, in the background, it would secretly monitor all HTTP requests and responses. When it detects a request containing login credentials or other sensitive data protected by cookies, CookieThief would extract the cookies, encrypt them, and transmit them to a remote server controlled by the attacker. The attacker could then use these cookies to impersonate the user, gaining unauthorized access to their online accounts and sensitive data. The extension might even employ techniques to hide its activity from the user, making detection difficult. This illustrates the potential for sophisticated attacks leveraging the seemingly innocent nature of browser extensions.
Network-Level Manipulation Techniques
Chrome’s cookie protection, while robust, isn’t impenetrable. Network-level manipulation offers avenues for bypassing these restrictions, leveraging the inherent complexities of internet communication. These techniques often involve manipulating the path cookies take or altering how the browser interacts with the network, effectively hiding cookie-related information from Chrome’s watchful eye. While ethically questionable and often against a website’s terms of service, understanding these methods is crucial for security professionals to identify and mitigate vulnerabilities.
By strategically employing proxies, VPNs, and HTTP header manipulation, determined individuals can potentially circumvent Chrome’s cookie controls. This is achieved by creating an intermediary layer between the browser and the target website, masking the user’s true identity and manipulating the data exchanged. This approach exploits the fact that cookie handling isn’t always consistent across different network environments.
Proxy and VPN Usage for Cookie Circumvention
Proxies and VPNs act as intermediaries, routing your internet traffic through a different server. This masks your IP address and can potentially bypass geolocation-based cookie restrictions. A VPN encrypts your connection, adding an extra layer of security and anonymity. However, websites employing advanced anti-fraud measures might still detect anomalies, especially if your behavior is inconsistent with the location claimed by the proxy or VPN. For example, a user accessing a US-based website from a VPN server in Germany might trigger suspicion if their browser language settings are English. Sophisticated systems often check for inconsistencies between the claimed location and other user-agent details.
HTTP Header Manipulation for Cookie Bypass
HTTP headers contain crucial information about the request and response between a browser and a server. Manipulating headers, such as the `User-Agent` or `Cookie` header itself, can sometimes trick the website into ignoring or misinterpreting cookie-related information. Modifying the `Cookie` header to remove or alter specific cookies could potentially allow access without triggering the expected restrictions. However, this method requires a deep understanding of HTTP protocols and the target website’s cookie handling mechanisms. It’s important to note that many websites actively check for header manipulation and will likely block requests deemed suspicious.
Weaknesses in Network-Based Cookie Protection Mechanisms
While network-based cookie protection mechanisms aim to enhance security, they are not foolproof. One potential weakness lies in the reliance on IP addresses for identification. Dynamic IP addresses, often assigned by ISPs, can make it difficult to track users consistently. Furthermore, the use of proxies and VPNs can effectively mask the user’s true IP address, potentially bypassing geolocation-based restrictions. Another vulnerability might exist in poorly implemented header validation. Websites that fail to thoroughly check HTTP headers for inconsistencies or manipulations can be vulnerable to bypass attempts. The complexity of network infrastructure also contributes to the difficulty of implementing comprehensive and robust cookie protection.
Network Configurations Exploitable for Cookie Bypass, Bypassing chromes cookie protection
Several network configurations can be exploited for bypassing cookie restrictions. These include:
The effectiveness of these configurations varies depending on the specific website’s security measures and the sophistication of the techniques employed. Successfully bypassing cookie protection often requires a combination of techniques and a thorough understanding of the target system’s vulnerabilities. It’s crucial to remember that attempting to circumvent cookie restrictions is often against a website’s terms of service and may have legal consequences.
| Configuration | Description | Potential Vulnerability |
|---|---|---|
| Public Wi-Fi Network | Shared network with multiple users. | Limited control over network traffic, potential for man-in-the-middle attacks. |
| Tor Network | Anonymizing network using multiple relays. | Masks user’s IP address and makes tracking difficult. |
| Misconfigured Proxy Server | Proxy server with weak authentication or improper configuration. | Potential for unauthorized access and manipulation of network traffic. |
Impact on User Privacy and Security

Source: pcmag.com
Bypassing Chrome’s robust cookie protection mechanisms, while seemingly offering increased control or access, opens a Pandora’s Box of privacy and security vulnerabilities. The seemingly innocuous act of manipulating cookie handling can have far-reaching consequences, impacting not only individual users but also the broader digital landscape. Understanding these implications is crucial for making informed decisions about online behavior and security practices.
The core issue lies in the fundamental role cookies play in tracking online activity. While cookies themselves aren’t inherently malicious, their manipulation can be exploited to gather sensitive information, track browsing habits with unprecedented detail, and even facilitate identity theft. By circumventing the safeguards Chrome puts in place, users essentially expose themselves to a greater risk of targeted advertising, data breaches, and other forms of online exploitation.
Privacy Implications of Bypassing Cookie Protection
Circumventing Chrome’s cookie protection significantly weakens the browser’s ability to safeguard user privacy. This allows websites and third-party trackers to collect and utilize browsing data without the user’s explicit knowledge or consent. This data can include sensitive information like login credentials, payment details, or location data, potentially leading to identity theft, financial fraud, or even physical harm. The level of intrusion depends heavily on the specific bypass method employed. For example, using a browser extension designed to manage cookies might offer slightly more control than directly manipulating network settings, but both methods ultimately compromise the inherent privacy protections of the browser. The lack of transparency inherent in many bypass methods exacerbates this issue, as users may not fully grasp the extent of data exposure.
Security Risks Associated with Compromised Cookie Handling
Compromised cookie handling directly increases the vulnerability to various security threats. Malicious actors could exploit manipulated cookies to gain unauthorized access to user accounts, inject malware, or conduct phishing attacks. A successful cookie bypass could allow a website to inject malicious scripts into a user’s browser, potentially leading to data theft, system compromise, or the installation of ransomware. Furthermore, the use of less secure bypass methods, such as those involving manipulation of network settings, increases the risk of man-in-the-middle attacks, where malicious actors intercept and alter communication between the user’s browser and the website. This can lead to the theft of sensitive information, including passwords, credit card details, and other personal data.
Comparison of Privacy Implications Across Bypass Methods
Different methods of bypassing Chrome’s cookie protection have varying levels of impact on user privacy. While using browser extensions might provide some degree of control, the inherent complexity and potential for malicious extensions introduce a significant risk. Direct manipulation of network settings, on the other hand, offers less control and significantly increases the vulnerability to man-in-the-middle attacks and other sophisticated security breaches. The most privacy-invasive methods involve directly modifying the browser’s code or using custom scripts, which can allow for extensive data collection and manipulation without any user oversight. Ultimately, any method that circumvents Chrome’s built-in protections compromises user privacy to some degree.
Potential Consequences of Successful Cookie Bypass Attempts
The following list Artikels the potential consequences of successful cookie bypass attempts:
- Identity theft: Access to cookies containing personal information can lead to identity theft and fraudulent activities.
- Financial fraud: Compromised cookies holding financial data can result in unauthorized transactions and financial losses.
- Data breaches: Bypass attempts can expose sensitive personal data to malicious actors, leading to large-scale data breaches.
- Malware infections: Manipulated cookies can be used to inject malware into the user’s system, causing significant damage.
- Phishing attacks: Compromised cookies can facilitate more effective phishing attacks, increasing the chances of successful deception.
- Loss of control over online activity: Bypass methods can lead to a loss of control over browsing habits and online interactions.
- Targeted advertising: Increased tracking capabilities can result in more targeted and intrusive advertising.
Chrome’s Defense Mechanisms Against Bypass Attempts
Chrome’s relentless battle against cookie manipulation involves a multi-layered defense system, constantly evolving to stay ahead of increasingly sophisticated bypass attempts. This intricate security architecture aims to safeguard user privacy and maintain the integrity of web browsing. Understanding these mechanisms is crucial to appreciating the complexity of modern browser security.
Chrome employs several robust strategies to thwart cookie manipulation. These range from simple checks to complex behavioral analysis, working in concert to create a formidable barrier against unauthorized access and modification of cookies. The effectiveness of these mechanisms is constantly being tested and improved upon, reflecting the ongoing arms race between browser developers and those seeking to exploit vulnerabilities.
SameSite Attribute Enforcement
The SameSite attribute, a crucial part of Chrome’s cookie security, restricts the circumstances under which cookies are sent to servers. By carefully controlling which requests include cookies, Chrome prevents cross-site request forgery (CSRF) attacks and limits the ability of malicious scripts on one site to access cookies from another. For example, a SameSite=Strict setting ensures that cookies are only sent in requests originating from the same site that set the cookie, effectively blocking many common cookie theft attempts. Less strict settings offer a balance between security and functionality, but still provide significant protection.
Cookie Isolation and Partitioning
Chrome employs sophisticated cookie isolation techniques to limit the impact of compromised sites. Cookies are often compartmentalized, preventing malicious scripts on one site from accessing cookies associated with other sites. This partitioning significantly reduces the scope of a successful attack, even if a site is compromised, minimizing the risk of widespread data theft. This architectural approach ensures that even if one part of the system is breached, the damage is contained. Think of it as a high-security building with firewalls between different sections.
HTTP Strict Transport Security (HSTS)
HSTS forces all communication with a particular website to occur over HTTPS, preventing man-in-the-middle attacks that could intercept and manipulate cookies. Once a site is registered with HSTS, Chrome will automatically redirect any HTTP requests to HTTPS, ensuring that all data, including cookies, is encrypted and protected from eavesdropping. This is a proactive measure that prevents attackers from even attempting to access cookies via unencrypted channels. Major websites often utilize HSTS to enhance their security posture.
Content Security Policy (CSP)
CSP provides a powerful mechanism for controlling the resources a website is allowed to load. By specifying allowed sources for scripts and other content, CSP reduces the risk of malicious code being injected into a page, which could then be used to steal cookies. This granular control allows website owners to define precisely what resources their pages can access, thereby limiting the attack surface and preventing unauthorized script execution. A carefully configured CSP is a strong deterrent against various forms of web attacks, including those targeting cookies.
Real-time Detection of Suspicious Behavior
Chrome incorporates sophisticated algorithms to detect and mitigate suspicious behavior in real-time. These algorithms analyze network traffic and browser activity to identify patterns consistent with cookie manipulation attempts. If suspicious activity is detected, Chrome may take action, such as blocking the request or warning the user. This proactive approach ensures that many attacks are thwarted before they can succeed. The exact mechanisms involved are often kept confidential for security reasons, but their effectiveness is demonstrated by the rarity of successful large-scale cookie theft.
Ethical Considerations and Legal Ramifications
Source: cpa.rip
Bypassing Chrome’s cookie protection, while technically achievable, treads a precarious path ethically and legally. The actions of developers and users alike are subject to scrutiny, potentially leading to significant consequences. Understanding these implications is crucial for responsible digital citizenship.
The ethical landscape is complex. On one hand, arguments could be made for bypassing cookie protection in the name of user privacy, particularly concerning aggressive tracking practices by some websites. However, circumventing security measures designed to protect user data and maintain website integrity raises serious concerns. The potential for misuse is substantial, opening doors to malicious activities like identity theft and data breaches. The balance between protecting user privacy and respecting website security protocols is delicate and necessitates careful consideration.
Ethical Implications of Bypassing Cookie Protection
Developing or using methods to bypass cookie protection raises several ethical dilemmas. The primary concern revolves around the potential for misuse. While some might argue for its use in protecting user privacy from intrusive tracking, the same techniques could be easily exploited by malicious actors for nefarious purposes. This creates a moral grey area, where the intent behind the action significantly impacts its ethical standing. The lack of transparency and potential for unintended consequences further complicate the ethical considerations. A user might believe they are enhancing their privacy, when in reality they are creating vulnerabilities for themselves and others.
Legal Ramifications of Unauthorized Cookie Access
Unauthorized access to cookies carries significant legal ramifications. Depending on the jurisdiction and the specific nature of the breach, individuals or organizations could face a range of penalties, including hefty fines, lawsuits from affected parties, and even criminal charges. Data protection laws, such as GDPR in Europe and CCPA in California, impose strict regulations on the collection, processing, and storage of personal data. Bypassing cookie protection to access sensitive information violates these laws and could result in severe consequences. For instance, a company using such methods to steal competitor’s marketing data could face antitrust violations and significant financial penalties.
Comparison of Ethical Considerations Across Bypass Methods
The ethical implications vary slightly depending on the method used. Exploiting browser extensions, for example, might be viewed as less ethically problematic than directly manipulating network traffic, as the former often involves user consent (though potentially uninformed consent). However, even seemingly innocuous methods can have unintended consequences. Network-level manipulation, being more invasive and potentially impacting multiple users, carries a significantly higher ethical burden. The potential for widespread harm increases proportionally with the scale and reach of the bypass method.
Scenario Illustrating Legal Consequences
Imagine a scenario where a disgruntled employee of a social media company develops a script to bypass cookie protection and access the personal data of users. This employee then sells this data to a marketing firm, which uses it for targeted advertising without user consent. This action violates numerous privacy laws, resulting in significant legal repercussions for both the employee and the marketing firm. They could face substantial fines, civil lawsuits from affected users, and potential criminal charges for data theft and unauthorized access. The company itself could also face legal action for failing to adequately protect user data.
Outcome Summary: Bypassing Chromes Cookie Protection
Ultimately, the battle against cookie bypass attempts is an ongoing arms race. While clever techniques can temporarily circumvent Chrome’s defenses, the browser’s security measures constantly evolve to stay ahead. Understanding the methods used to bypass cookie protection, along with the inherent risks and ethical considerations, is crucial for both developers striving for secure applications and users seeking to protect their online privacy. Remember, the digital world is a complex landscape, and navigating it responsibly requires awareness and vigilance.