Evasive Panda Attacking Cloud Services: Picture this: a stealthy panda, surprisingly agile and cunning, infiltrating the seemingly impenetrable defenses of your cloud infrastructure. This isn’t some whimsical children’s story; it’s a chilling metaphor for the sophisticated cyberattacks targeting cloud services today. The “evasive” aspect highlights the attacker’s ability to slip past security measures, while the “panda” – unexpected yet powerful – represents the surprising source of the threat. We’ll dissect this analogy, exploring the types of attacks, the techniques employed, and ultimately, how to fortify your defenses against this digital predator.
This exploration delves into the reality of advanced persistent threats (APTs) and other sophisticated attacks targeting cloud environments. We’ll examine the motivations behind these attacks, the challenges in attribution, and the crucial defensive strategies needed to protect your valuable data and services. From understanding the attacker’s methods to implementing robust security measures, this deep dive equips you with the knowledge to safeguard your digital assets in this increasingly complex threat landscape.
Understanding the Metaphor

Source: boredpanda.com
The phrase “evasive panda attacking cloud services” immediately conjures a striking image: a seemingly innocent, cuddly panda, unexpectedly turning into a sophisticated and stealthy attacker targeting the digital infrastructure of the cloud. It’s a paradoxical image, highlighting the deceptive nature of modern cyber threats. The unexpectedness of the attack, coupled with the surprising agent, makes the metaphor particularly memorable and effective.
The metaphor cleverly combines seemingly contradictory elements. “Evasive” suggests the panda’s ability to skillfully avoid detection, employing advanced techniques to remain hidden within the system. “Panda,” usually associated with peacefulness and cuteness, ironically represents the threat actor – a hidden, potentially devastating force. “Attacking” underscores the malicious intent and the disruptive potential of the cyber threat. Finally, “cloud services” specifies the target: the vast, interconnected digital world where sensitive data and critical applications reside. The overall effect is a memorable and impactful image that transcends the technical jargon typically associated with cybersecurity.
Comparison with Other Cybersecurity Metaphors
Many metaphors are used to describe cybersecurity threats. The “virus” metaphor, for example, is prevalent, likening malware to a biological agent that infects and spreads. While effective in conveying the contagious nature of malware, it lacks the nuance of the “evasive panda” metaphor, which better captures the sophistication and stealth of advanced persistent threats (APTs). Other metaphors, like “digital warfare” or “cyberattack,” are more generic and less evocative. The strength of the “evasive panda” metaphor lies in its unexpected juxtaposition of seemingly harmless imagery with the severity of the threat, creating a memorable and impactful image. The weakness, perhaps, is its limited applicability to all types of cyber threats; it’s particularly apt for describing highly sophisticated, stealthy attacks.
A Narrative Illustrating the Metaphor
Imagine a seemingly innocuous email, appearing to be a routine update from a trusted vendor. This is our panda, disguised as something benign. Within the email, a seemingly harmless attachment contains a zero-day exploit, expertly crafted to bypass all existing security measures. This is the panda’s evasion technique. Once opened, the exploit silently infiltrates the cloud infrastructure, granting the attacker (the panda) access to sensitive customer data. The panda, undetected, moves laterally across the cloud environment, accessing databases, servers, and applications, carefully avoiding any security traps. The data exfiltration happens subtly, with small amounts of data being stolen over a long period. The attack is only discovered months later, after significant damage has already been inflicted, demonstrating the true potency of this “evasive panda” attack.
Types of Attacks Implied
The evasive panda metaphor, while whimsical, cleverly encapsulates the stealthy and persistent nature of sophisticated cyberattacks targeting cloud services. The “panda” represents the seemingly innocuous nature of the attack, often hiding in plain sight, while “evasive” highlights the attacker’s ability to bypass traditional security measures. Let’s dissect three specific attack types this metaphor could represent.
These attacks are characterized by their ability to remain undetected for extended periods, mirroring the panda’s camouflage in its natural habitat. The persistence of these attacks, much like a panda’s determination, makes them particularly dangerous and difficult to mitigate.
Advanced Persistent Threats (APTs)
Advanced Persistent Threats are precisely what their name suggests: highly sophisticated, long-term attacks often carried out by state-sponsored actors or highly organized criminal groups. The “evasive” aspect is evident in their use of advanced techniques like polymorphic malware, zero-day exploits, and living-off-the-land techniques to avoid detection. The “panda” element comes from their ability to blend into the environment, quietly accessing and exfiltrating data over an extended period without raising significant alarms. Think of it as a panda subtly munching on bamboo in a digital forest, unnoticed until the damage is significant.
Supply Chain Attacks
These attacks target vulnerabilities within the software supply chain, compromising third-party vendors or open-source libraries that cloud services rely upon. The attacker doesn’t directly target the cloud provider but instead infiltrates a trusted component, gaining access indirectly. The “evasive” nature is clear; the attack vector is hidden within legitimate software updates or dependencies. The “panda” aspect manifests in the seemingly benign nature of the compromised component – it’s like a panda cleverly hiding amongst a group of seemingly harmless bamboo shoots. The SolarWinds attack is a prime example, demonstrating the devastating potential of this type of attack.
Insider Threats
While not always malicious, insider threats represent a significant risk. These involve compromised or disgruntled employees with legitimate access to cloud resources who misuse their privileges. The “evasive” element stems from the attacker’s legitimate credentials and access, making detection challenging. The “panda” element lies in the attacker’s ability to blend seamlessly into the organization’s workflow, gradually exfiltrating data or sabotaging systems without immediate detection. This attack type often involves social engineering or exploiting vulnerabilities in access control mechanisms.
Attack Type Categorization
The following table summarizes the three attack types, highlighting their methods, targets, and typical defenses.
| Attack Type | Methods | Targets | Typical Defenses |
|---|---|---|---|
| Advanced Persistent Threats (APTs) | Zero-day exploits, polymorphic malware, living-off-the-land techniques, social engineering | Cloud infrastructure, data, intellectual property | Advanced threat detection, endpoint detection and response (EDR), security information and event management (SIEM), regular security audits |
| Supply Chain Attacks | Compromised software updates, malicious code in open-source libraries, exploiting vulnerabilities in third-party vendors | Cloud services relying on compromised components | Secure software supply chain management, vulnerability scanning, code signing, rigorous vendor vetting |
| Insider Threats | Misuse of privileges, social engineering, data exfiltration, malware installation | Cloud resources accessed by compromised employees | Access control lists (ACLs), multi-factor authentication (MFA), data loss prevention (DLP), employee training and awareness programs, regular security audits |
The impact of these attacks on cloud service availability and data integrity can be severe. APTs can lead to prolonged outages and data breaches, while supply chain attacks can cascade across multiple cloud services, causing widespread disruption. Insider threats can result in data loss, system compromise, and reputational damage. The long-term consequences of these attacks can significantly impact business operations and customer trust.
The “Evasive” Aspect: Evasive Panda Attacking Cloud Services
Our mischievous panda, it turns out, isn’t just any clumsy cloud-muncher. This is a sophisticated operator, employing a range of advanced techniques to avoid detection and wreak havoc undetected. Think of it as a digital ninja, silently infiltrating and manipulating systems with precision and stealth. Understanding these evasion tactics is crucial to building robust cloud defenses.
The panda’s evasiveness relies on a combination of clever techniques and powerful tools, allowing it to blend seamlessly into the cloud environment and evade even the most vigilant security measures. These methods go beyond simple brute-force attacks; they represent a level of sophistication that requires a proactive and adaptive security strategy.
Polymorphic Malware and Obfuscation
Polymorphic malware is a chameleon in the digital world. It constantly changes its code signature, making it incredibly difficult for traditional antivirus software to identify and neutralize. Think of it like a virus that continuously alters its genetic makeup, rendering existing vaccines ineffective. Obfuscation techniques further complicate matters by disguising the malware’s true nature, making its malicious intent almost impossible to discern through simple code analysis. This is achieved through techniques like packing, encryption, and code virtualization, all designed to make reverse engineering extremely difficult. Imagine a treasure map that constantly rearranges itself – you’d need more than just a compass to find the X.
Advanced Persistent Threats (APTs)
APTs represent a long-term, stealthy attack strategy. Instead of a quick hit-and-run, APTs focus on persistent infiltration and data exfiltration over an extended period. The panda, in this scenario, doesn’t just grab a few bamboo shoots and run; it sets up a long-term residence, quietly collecting information and resources without raising suspicion. This requires sophisticated techniques like social engineering to gain initial access, followed by lateral movement within the cloud environment to access sensitive data. The attacker uses various tools to maintain persistence, often leveraging legitimate system tools and processes to blend in with the normal activity. This low-and-slow approach is extremely difficult to detect, making APTs one of the most challenging cyber threats.
Attacker Technologies and Tools, Evasive panda attacking cloud services
The tools used by attackers to achieve evasion are constantly evolving, reflecting the arms race between security professionals and cybercriminals. These tools range from readily available open-source utilities to highly specialized, commercially available penetration testing suites. Powerful scripting languages like Python and PowerShell are frequently used to automate attacks and evade detection. The capabilities of these tools are extensive, allowing attackers to perform complex tasks like code injection, privilege escalation, and data exfiltration with ease. However, their limitations lie primarily in the expertise required to operate them effectively and the potential for detection if not used carefully. A skilled security team can often identify the tell-tale signs of these tools being used, even if the attack itself is sophisticated.
Steps to Remain Undetected
Understanding the steps an attacker might take to remain undetected is crucial for effective security. Here’s a possible sequence of actions a determined panda might employ:
- Initial Access: Gaining entry through phishing emails, exploiting vulnerabilities, or using compromised credentials.
- Lateral Movement: Moving undetected through the cloud environment using techniques like exploiting misconfigurations, leveraging shared resources, or using compromised accounts.
- Privilege Escalation: Gaining higher-level access to sensitive systems and data.
- Data Exfiltration: Secretly transferring stolen data outside the cloud environment using techniques like covert channels or encrypted communication.
- Persistence: Maintaining access to the compromised systems for long-term operations, often using backdoors or rootkits.
- Obfuscation and Anti-forensics: Employing techniques to hide their activities and make forensic analysis difficult.
The “Panda” Aspect

Source: com.tr
The evasive panda’s bamboo-chewing isn’t just about snacking on cloud data; it’s about who’s doing the munching and why. Unmasking the actors behind these sophisticated attacks is a crucial piece of the puzzle, revealing the motivations driving this digital predation. Understanding the “panda” – the attacker – requires delving into the complex world of attribution and the diverse landscape of cybercriminal motivations.
Attribution in these cases is a thorny issue. Pinpointing the perpetrators of these attacks is akin to tracking a ghost through a digital maze. The attackers employ advanced techniques to obscure their tracks, making definitive attribution extremely challenging. Sophisticated methods are needed to unravel the digital breadcrumbs they leave behind.
Attribution Challenges and Methods
The difficulty in attributing these attacks stems from the use of advanced techniques designed to mask the attackers’ true identities and locations. These include the use of anonymizing networks like Tor, compromised machines (botnets) as stepping stones, and the exploitation of zero-day vulnerabilities. Attribution analysis relies on a combination of technical indicators of compromise (IOCs), such as malware signatures, network traffic patterns, and code similarities. Researchers also analyze the attackers’ tactics, techniques, and procedures (TTPs) to identify patterns and link them to known actors. Geolocation data, although often unreliable due to masking techniques, can provide clues. Finally, analysis of the target’s industry and the nature of the stolen data can offer insights into the potential motivations of the attackers. For example, a successful attack on a defense contractor is more likely to be state-sponsored than an attack on a small e-commerce site.
Hypothetical Cybercriminal Profile: “Cloud Shadow Syndicate”
Imagine a group we’ll call the “Cloud Shadow Syndicate.” This hypothetical group consists of highly skilled individuals, possibly operating across multiple countries. Their resources include a robust infrastructure of compromised servers, a dedicated team of malware developers, and access to advanced penetration testing tools. They specialize in evasive techniques, utilizing custom-built malware and sophisticated anti-forensics methods to avoid detection. Their operational methods are highly organized, with specialized teams handling reconnaissance, exploitation, data exfiltration, and money laundering. Their financial motivation is likely substantial, targeting high-value data for sale on the dark web or for use in extortion schemes. They could also be motivated by political or ideological goals, potentially acting on behalf of a state actor, though maintaining plausible deniability. The syndicate’s operational security is impeccable, constantly adapting their TTPs to stay ahead of cybersecurity defenses. Their attacks are meticulously planned, leveraging vulnerabilities in cloud infrastructure and exploiting human error to gain initial access. The data they steal is carefully selected for maximum impact and resale value, showcasing a high level of sophistication and planning. Their success hinges on their ability to blend into the digital noise, making attribution an exceptionally difficult task. This illustrates the potential for both financially and politically motivated groups to utilize such highly evasive tactics.
Defensive Strategies and Mitigation
Protecting cloud services from evasive panda attacks requires a multi-layered, proactive approach. Simply relying on a single security measure is akin to using a bamboo fence against a determined panda – ultimately ineffective. A robust defense necessitates a combination of preventative measures, sophisticated detection mechanisms, and well-rehearsed incident response plans.
Cloud providers must adopt a holistic security posture, moving beyond traditional perimeter-based defenses to embrace more dynamic and adaptive strategies. This means proactively identifying and mitigating vulnerabilities before they can be exploited, constantly monitoring for suspicious activity, and having a rapid and effective response plan in place for when attacks inevitably occur. The cost of inaction far outweighs the investment in robust security measures.
Preventative Security Measures
Implementing preventative measures is the first line of defense. This involves strengthening the foundational security of the cloud infrastructure and applications. This includes regularly patching systems and applications to address known vulnerabilities, employing strong access controls and multi-factor authentication to limit unauthorized access, and rigorously validating all code and configurations before deployment. Regular security audits and penetration testing, simulating real-world attacks, help identify weaknesses before malicious actors can exploit them. For example, regularly scanning for vulnerabilities using tools like Nessus or OpenVAS can significantly reduce the attack surface. Employing code signing and static analysis techniques helps prevent malicious code from being deployed.
Detection Mechanisms
Evasive attacks aim to blend in with legitimate traffic, making detection challenging. Sophisticated detection mechanisms are crucial. This involves leveraging security information and event management (SIEM) systems to aggregate and analyze security logs from various sources. Intrusion detection and prevention systems (IDPS) can identify malicious network traffic patterns. Anomaly detection techniques, which identify deviations from established baselines, are also vital in spotting unusual activity. Behavioral analysis, which monitors user and system behavior to identify anomalies, can be particularly effective in detecting evasive attacks. Imagine a SIEM system flagging unusual login attempts from unexpected geographical locations – a clear indicator of a potential breach.
Incident Response Plans
Even with robust preventative measures and detection mechanisms, successful breaches can still occur. A well-defined incident response plan is crucial for minimizing the impact of an attack. This plan should include clear roles and responsibilities, communication protocols, escalation procedures, and recovery strategies. Regular drills and simulations help ensure the plan is effective and that teams are prepared to respond quickly and efficiently. For example, a pre-defined communication plan ensures that relevant stakeholders, including customers, are informed promptly and accurately in the event of a breach. A comprehensive recovery plan Artikels steps for restoring affected systems and data.
Comparison of Security Architectures
Zero trust architecture and micro-segmentation offer distinct advantages against evasive attacks. Zero trust operates on the principle of “never trust, always verify,” requiring strict authentication and authorization for every access request, regardless of location. Micro-segmentation divides the network into smaller, isolated segments, limiting the impact of a breach. While both offer strong protection, zero trust is particularly effective against lateral movement within the cloud environment, a common tactic employed by evasive attackers. Micro-segmentation excels at containing the spread of an attack, preventing it from impacting the entire system. A hybrid approach, combining the strengths of both architectures, provides a highly resilient defense.
Layered Security Approach
A layered security approach is paramount. This isn’t about simply stacking different security tools; it’s about creating a multi-layered defense where each layer complements the others.
- Network Security: Firewalls, intrusion prevention systems, and web application firewalls form the initial barrier, filtering malicious traffic before it reaches the cloud environment.
- Host Security: Operating system hardening, anti-malware software, and regular patching protect individual servers and virtual machines.
- Application Security: Secure coding practices, input validation, and vulnerability scanning protect applications from exploitation.
- Data Security: Encryption at rest and in transit, access control lists, and data loss prevention (DLP) tools protect sensitive data.
- Identity and Access Management (IAM): Strong authentication, authorization, and regular access reviews prevent unauthorized access.
- Security Monitoring and Response: SIEM systems, security orchestration, automation, and response (SOAR) tools, and incident response plans enable detection and rapid response to threats.
This layered approach ensures that even if one layer is compromised, others remain in place to mitigate the attack. Imagine a castle with multiple walls, moats, and guards – each layer adding to the overall defense.
Final Conclusion
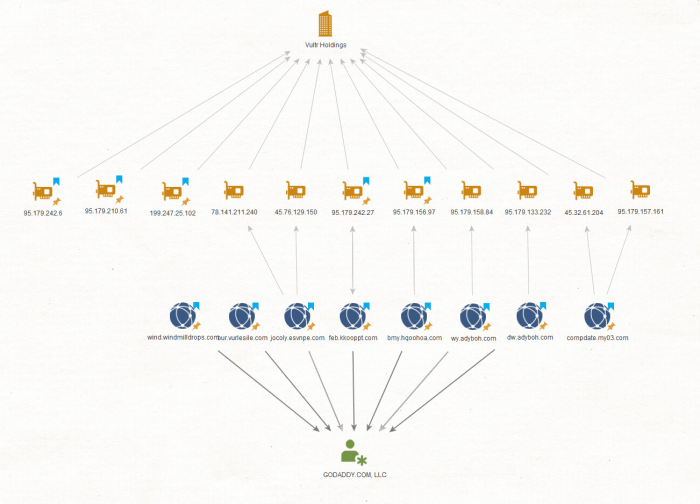
Source: checkpoint.com
The “Evasive Panda” metaphor perfectly encapsulates the stealth and unexpected nature of modern cyberattacks targeting cloud services. While the image of a cuddly panda might initially seem incongruous with a serious security threat, it serves as a potent reminder that danger can come from unexpected sources. By understanding the techniques used by these sophisticated attackers, recognizing the potential motivations behind their actions, and implementing a layered security approach, organizations can significantly improve their resilience against these increasingly prevalent threats. The fight against the digital panda requires constant vigilance, adaptation, and a proactive security posture. Don’t get caught napping.





