Lazarus APT hackers exploit Chrome zero day: That headline alone screams high-stakes digital espionage. This isn’t your average script kiddie messing around; we’re talking about a sophisticated, state-sponsored group known for their ruthlessness and precision. They leveraged a previously unknown vulnerability in Chrome, a zero-day exploit, to potentially compromise countless systems. The implications are massive, impacting everything from individual users to major corporations, and the whole thing raises serious questions about online security in today’s hyper-connected world.
This attack highlights the constant cat-and-mouse game between cybersecurity professionals and advanced persistent threats (APTs). Understanding how Lazarus pulled off this exploit, the vulnerability’s specifics, and the subsequent response from Google and other stakeholders is crucial for bolstering our defenses against future attacks. We’ll dive deep into the technical aspects, the impact, and what you can do to protect yourself.
Lazarus APT Group

Source: reporterspost24.com
The Lazarus Group, a notorious state-sponsored advanced persistent threat (APT) actor, has been a significant player in the global cyber threat landscape for over a decade. Their operations are characterized by sophisticated techniques, high-profile targets, and significant financial gains, making them a constant concern for governments and businesses alike. Understanding their history, methods, and motivations is crucial to mitigating the risks they pose.
Lazarus Group History and Operations
The Lazarus Group’s origins are shrouded in some mystery, but strong evidence points to North Korea as the group’s sponsor. Their activities have spanned numerous years, evolving from relatively simple attacks to highly complex and targeted campaigns. They’ve demonstrated a remarkable capacity to adapt their tactics and techniques, making attribution challenging but their modus operandi often reveals telltale signs. Their persistent and highly adaptable nature makes them a formidable threat. Early operations focused on financial theft, but their targets have broadened to include critical infrastructure and geopolitical objectives.
Timeline of Significant Lazarus APT Attacks
The Lazarus Group’s activities have been marked by several high-profile attacks. While precise dates are sometimes difficult to pinpoint due to the covert nature of their operations, a general timeline can be constructed based on publicly available information. A key characteristic is their ability to remain undetected for extended periods, often exploiting vulnerabilities before they’re widely known.
| Year | Attack Name/Description | Target | Outcome |
|---|---|---|---|
| 2014 | Sony Pictures Entertainment hack | Sony Pictures Entertainment | Data breach, release of sensitive information |
| 2016 | Bangladesh Bank heist | Bangladesh Bank | Theft of $81 million |
| 2017 | WannaCry ransomware | Global organizations | Widespread disruption, significant financial losses |
| 2018 | Coincheck cryptocurrency exchange hack | Coincheck | Theft of NEM cryptocurrency |
Motives and Targets of the Lazarus Group
The Lazarus Group’s motives are primarily financially driven, with a significant focus on stealing cryptocurrency and fiat currency. However, their attacks also serve geopolitical objectives, aiming to disrupt critical infrastructure and sow discord among their adversaries. Their targets range from financial institutions and cryptocurrency exchanges to media companies and government agencies, demonstrating a broad range of interests and capabilities. The financial gains often directly support the North Korean regime.
Infrastructure and Techniques Employed by the Lazarus Group
The Lazarus Group employs a sophisticated range of techniques, including malware development, spear-phishing campaigns, and exploitation of zero-day vulnerabilities. They leverage compromised infrastructure globally, often using multiple layers of obfuscation and proxies to mask their activities. Their use of custom malware, combined with their ability to adapt to evolving security measures, makes them a persistent and difficult-to-detect threat. They also frequently utilize social engineering tactics to gain initial access to their targets.
Comparison of Lazarus Attacks with Other Notable APT Groups
While the Lazarus Group shares some characteristics with other APT groups, certain aspects distinguish their operations. This comparison highlights these similarities and differences.
| Attribute | Lazarus Group | APT29 (Cozy Bear) | APT41 (Barium) |
|---|---|---|---|
| Primary Motivation | Financial gain, geopolitical objectives | Espionage, intelligence gathering | Espionage, financial gain |
| Targeting | Financial institutions, media, government | Government agencies, political organizations | Technology companies, gaming companies |
| Techniques | Malware, spear-phishing, zero-day exploits | Advanced malware, data exfiltration | Malware, supply chain attacks |
| Attribution | North Korea | Russia | China |
The Chrome Zero-Day Exploit
The Lazarus APT group’s recent attack leveraged a previously unknown vulnerability, a zero-day exploit, in Google Chrome to gain unauthorized access to target systems. This sophisticated attack highlights the ever-present threat of advanced persistent threats and the critical need for robust security measures. Understanding the mechanics of this zero-day is crucial to comprehending the scale and potential impact of such attacks.
The specific zero-day vulnerability exploited remains undisclosed by Google for security reasons. However, based on reports and the nature of the attack, it likely involved a memory corruption flaw within the Chrome rendering engine. This type of vulnerability is particularly dangerous because it can allow attackers to execute arbitrary code with the privileges of the browser process.
Remote Code Execution via Memory Corruption
This vulnerability allowed remote code execution by corrupting the memory of the Chrome browser. The attacker could inject malicious code into the browser’s memory, taking advantage of the flaw to bypass security mechanisms and execute arbitrary commands on the victim’s machine. This could range from stealing sensitive data to installing malware or gaining complete control of the system. The precision and sophistication required to successfully exploit such a vulnerability underscore the advanced capabilities of the Lazarus group.
Delivery Methods Employed by Lazarus
While the precise delivery method remains under investigation, Lazarus likely employed a phishing campaign to deliver the exploit. This could have involved malicious links embedded in emails or deceptive websites designed to lure victims into clicking and downloading the malicious payload. The payload would then contain the exploit, which, upon execution, would silently compromise the victim’s system. Alternative delivery methods, such as compromised software updates or software supply chain attacks, remain possible.
Potential Impact on Chrome Users
The potential impact of this zero-day vulnerability on Chrome users is significant. Successful exploitation could lead to the theft of sensitive information such as passwords, financial data, and intellectual property. Attackers could also install malware, enabling persistent surveillance or further attacks. In severe cases, complete system compromise could occur, granting attackers full control over the victim’s computer and potentially their entire network. The scale of potential damage depends heavily on the specific targets and the goals of the attackers. For example, targeting a financial institution could result in substantial financial losses.
Hypothetical Real-World Attack Scenario
Imagine a high-ranking executive at a major financial institution receives an email seemingly from a trusted colleague. The email contains a link to a seemingly innocuous document, perhaps a financial report. Clicking this link downloads a seemingly benign file, which actually contains the Chrome zero-day exploit. Upon opening the file in Chrome, the exploit is activated. The attacker gains control of the executive’s machine, allowing them to access sensitive financial data, potentially leading to a significant financial loss or even identity theft. This is a plausible scenario illustrating the real-world danger posed by this type of attack.
Technical Analysis of the Exploit
The Lazarus APT group’s Chrome zero-day exploit, while details remain scarce due to the sensitive nature of the vulnerability and its exploitation, likely leveraged a sophisticated combination of techniques to bypass Chrome’s robust security defenses. Understanding the technical intricacies requires piecing together fragmented information from various sources, focusing on known attack vectors and similar past exploits. The lack of publicly available code necessitates a largely inferential analysis, drawing parallels to previously disclosed vulnerabilities.
The exploit likely targeted a memory corruption vulnerability within the Chrome rendering engine, a common attack vector for browser exploits. This could involve techniques like heap overflow or use-after-free, manipulating memory allocation to execute arbitrary code. Such vulnerabilities are notoriously difficult to detect and patch, as they often involve intricate interactions within the browser’s complex codebase. By exploiting a memory management flaw, attackers can inject malicious code and gain control over the browser process, potentially leading to complete system compromise.
Exploit Code Structure (Inference)
While the precise code remains undisclosed, a plausible structure would involve several stages. First, a carefully crafted malicious payload, likely embedded within a seemingly benign webpage or document, would trigger the vulnerability. This payload would be designed to precisely overwrite memory locations, leading to the execution of shellcode. This shellcode would then perform further actions, such as establishing a reverse shell connection to a command-and-control server operated by the attackers. The entire process would need to evade Chrome’s various sandboxing and security mechanisms, making it extremely complex. Consider the sophisticated nature of past zero-day exploits; this one likely followed a similar multi-stage approach.
Techniques to Bypass Chrome’s Security Mechanisms
The exploit likely employed a combination of techniques to bypass Chrome’s defenses. This might include exploiting vulnerabilities in the browser’s sandbox, potentially using techniques to escape the sandbox and gain access to the operating system. Additionally, the attackers likely used sophisticated code obfuscation techniques to make the malicious code difficult to analyze and detect by antivirus software. Bypassing Chrome’s Address Space Layout Randomization (ASLR) would have been crucial, allowing the attackers to reliably locate and exploit the memory vulnerability. This requires precise knowledge of the internal workings of the Chrome browser.
Comparison to Other Chrome Zero-Day Vulnerabilities
This exploit shares similarities with previous Chrome zero-day vulnerabilities, particularly those involving memory corruption in the rendering engine. Many past exploits have used techniques like heap spraying to increase the chances of successful exploitation. However, the precise techniques used in this specific exploit remain unknown, highlighting the constant arms race between attackers and browser developers. The difficulty in patching these vulnerabilities underscores the need for continuous security updates and rigorous code review processes. The sophisticated nature of this exploit likely involved previously unseen techniques, requiring substantial effort to identify and mitigate.
Difficulty of Patching Such Vulnerabilities
Patching these vulnerabilities is notoriously challenging due to the complexity of modern browsers and the intricate interactions between different components. A single line of code change in a seemingly innocuous function can have unintended consequences, potentially introducing new vulnerabilities or causing instability. Furthermore, the need to maintain backward compatibility with older versions of the browser adds to the complexity of the patching process. Thorough testing and validation are essential to ensure that a patch does not introduce further problems. The time-sensitive nature of zero-day exploits requires rapid response and coordination between researchers, developers, and security teams.
Impact and Response to the Attack
The discovery of the Lazarus Group’s Chrome zero-day exploit sent shockwaves through the cybersecurity community. The immediate consequence was a scramble to understand the extent of the breach and to patch the vulnerability before it could be more widely exploited. The potential for widespread damage was significant, given the popularity of Chrome and the sophisticated nature of the exploit.
The scale of the attack remains somewhat unclear, as many victims may not even be aware of compromise. However, reports suggest that the exploit was used in targeted attacks against high-value individuals and organizations, likely focusing on espionage and data theft. While a precise number of victims is difficult to ascertain, the very existence of a zero-day targeting Chrome highlights the serious threat posed by advanced persistent threat (APT) groups like Lazarus.
Google’s Response to the Vulnerability, Lazarus apt hackers exploit chrome zero day
Google reacted swiftly to the discovery of the zero-day vulnerability. They immediately developed and released a security patch for Chrome, urging users to update their browsers as soon as possible. This rapid response minimized the window of vulnerability, limiting the potential for widespread exploitation. Beyond the patch, Google’s Threat Analysis Group (TAG) likely collaborated with other security researchers and government agencies to investigate the attack’s origins and scope, furthering their understanding of Lazarus’s tactics, techniques, and procedures (TTPs). This proactive approach underscores Google’s commitment to protecting its users from sophisticated cyber threats.
Response from Other Organizations and Governments
The vulnerability’s discovery prompted a coordinated response from various organizations and governments. Many cybersecurity firms issued advisories and guidance on mitigating the risk. Government agencies, particularly those focused on national security, likely engaged in their own investigations, aiming to identify affected entities within their jurisdictions and potentially attribute the attack to the responsible actors. International collaboration on cybersecurity issues is crucial in addressing threats like this, as APT groups often operate across borders, requiring a coordinated global response. Sharing threat intelligence and collaborating on remediation efforts is essential to effectively combat sophisticated cyberattacks.
Improving Organizational Security Posture
Organizations can significantly improve their security posture to mitigate similar threats by implementing several key strategies. A robust vulnerability management program is crucial, involving regular patching and updates of all software, including browsers. Employing a layered security approach, including firewalls, intrusion detection systems, and endpoint detection and response (EDR) solutions, can help detect and prevent malicious activity. Security awareness training for employees is vital, as human error remains a major factor in many successful attacks. Finally, organizations should consider implementing advanced threat protection solutions that leverage artificial intelligence and machine learning to detect and respond to sophisticated attacks like those carried out by APT groups. Proactive monitoring, threat intelligence integration, and incident response planning are all essential components of a strong security posture. Regular security audits and penetration testing can further identify vulnerabilities before malicious actors exploit them.
Prevention and Mitigation Strategies
Source: cloudkul.com
The Lazarus APT group’s exploitation of a Chrome zero-day highlights the critical need for robust security practices. While completely eliminating risk is impossible, proactive measures significantly reduce vulnerability. Implementing a multi-layered approach combining browser hardening, threat detection, and regular updates is crucial for individual users and organizations alike.
This section details practical strategies to prevent and mitigate similar attacks, focusing on browser security, threat detection, and the importance of continuous vigilance.
Securing Chrome Browsers
Strengthening your Chrome browser’s defenses is the first line of defense. This involves configuring browser settings to minimize attack vectors and enabling built-in security features. For example, disabling unnecessary browser extensions reduces the attack surface. Regularly reviewing and updating these extensions is also essential, as outdated extensions can contain vulnerabilities. Furthermore, enabling Chrome’s built-in sandbox feature helps isolate processes, limiting the impact of potential exploits. Finally, utilizing strong, unique passwords for all online accounts significantly reduces the risk of credential theft, a common post-exploitation tactic used by APTs.
Detecting and Preventing Similar Attacks
Effective threat detection relies on a combination of techniques. Employing robust antivirus and anti-malware software is a fundamental step. These tools can detect and block malicious files and websites attempting to exploit vulnerabilities. Beyond signature-based detection, utilizing behavioral analysis tools helps identify suspicious activities that might indicate an active attack, even if the malware isn’t yet known to traditional antivirus programs. Regular security audits and penetration testing can identify weaknesses in your systems before attackers do. These tests simulate real-world attacks, allowing for proactive remediation.
Software Updates and Security Patches
Promptly installing software updates and security patches is paramount. Software vendors regularly release patches addressing newly discovered vulnerabilities, including zero-day exploits. Failing to update exposes systems to known attack vectors. For organizations, a structured patch management system is essential, ensuring timely updates across all devices and systems. This often involves automated update processes and rigorous testing to avoid disruptions. For individuals, enabling automatic updates wherever possible simplifies the process and ensures up-to-date protection.
Endpoint Detection and Response (EDR) Solutions
EDR solutions provide advanced threat detection and response capabilities. These systems monitor endpoint devices (computers, laptops, etc.) for malicious activity, providing real-time alerts and detailed investigation tools. EDR goes beyond traditional antivirus by analyzing system behavior, identifying anomalies, and providing forensic data to understand and respond to attacks. Examples include Carbon Black, CrowdStrike Falcon, and SentinelOne. These solutions often integrate with other security tools, providing a comprehensive security posture.
Security Recommendations for Individuals and Organizations
A layered approach is crucial for optimal security. The following recommendations combine technical measures with security awareness training to create a robust defense.
- Keep software updated: Regularly update operating systems, browsers, and applications.
- Use strong passwords: Employ strong, unique passwords for all accounts and consider using a password manager.
- Enable multi-factor authentication (MFA): Add an extra layer of security to accounts whenever possible.
- Be wary of phishing attempts: Do not click on suspicious links or open attachments from unknown senders.
- Use reputable antivirus and anti-malware software: Keep it updated and regularly scan your devices.
- Regularly back up data: This mitigates data loss in case of a successful attack.
- Implement security awareness training: Educate users about phishing, social engineering, and other threats.
- Employ EDR solutions: For organizations, consider deploying endpoint detection and response systems.
- Conduct regular security audits and penetration testing: Identify and address vulnerabilities proactively.
Attribution and Future Threats
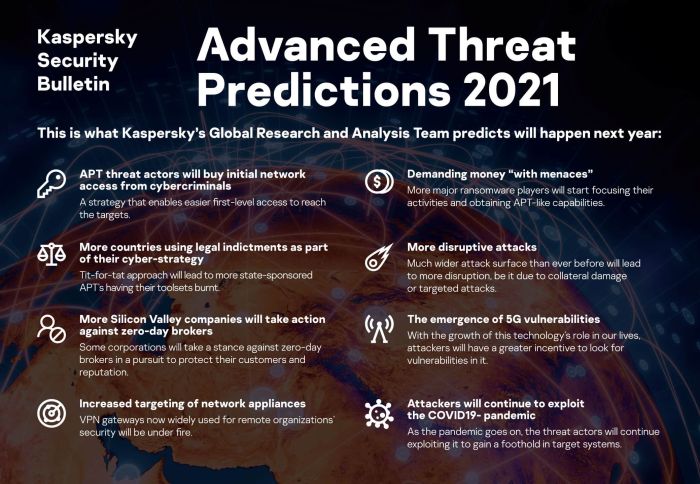
Source: kaspersky.com
The attribution of sophisticated cyberattacks like the Lazarus Group’s exploitation of the Chrome zero-day vulnerability is a complex undertaking, requiring meticulous investigation and a deep understanding of the attacker’s tactics, techniques, and procedures (TTPs). While definitive proof is often elusive, a combination of evidence can paint a compelling picture, leading to a high degree of confidence in attribution.
The challenges in accurately attributing cyberattacks are significant. The use of anonymization techniques, proxy servers, and compromised infrastructure obscures the true origin of attacks. Furthermore, advanced persistent threat (APT) groups often employ various techniques to mask their identities, making the process of tracing their activities back to a specific actor extremely difficult. Attribution often relies on circumstantial evidence, such as similarities in code, infrastructure overlaps, and operational patterns compared to previously known activities. This requires extensive analysis of malware samples, network traffic, and other digital forensic evidence.
Methods Used to Attribute the Attack to Lazarus
Attribution in this specific case likely relied on several factors. Similarities in the exploit’s code to previously observed Lazarus malware samples could be a key piece of evidence. Analysis of the command-and-control (C2) infrastructure used to communicate with compromised systems may reveal connections to known Lazarus infrastructure. Furthermore, the targets of the attack and the type of data sought could align with Lazarus’s known operational patterns, which often focus on financial institutions and government entities. The timing of the attack, in relation to geopolitical events or other Lazarus activities, could also provide contextual clues.
Challenges in Attributing Cyberattacks Accurately
The digital landscape is designed to obscure the identities of actors. The use of readily available tools and techniques makes tracing attacks back to their source extremely difficult. The sophistication of modern malware, combined with the vastness of the internet, allows attackers to easily mask their origin. False flags, where attackers intentionally leave misleading clues to point investigators towards a different actor, further complicate attribution efforts. Moreover, even with strong evidence, establishing legal proof for attribution can be a significant hurdle.
Potential Future Activities of Lazarus
Lazarus is likely to continue its operations, adapting its tactics to evade detection and maintain its operational secrecy. We can anticipate continued exploitation of zero-day vulnerabilities, targeting high-value assets in the financial sector, government agencies, and critical infrastructure. Their focus may shift depending on geopolitical events and national priorities. The development and deployment of new and more sophisticated malware is also highly probable, making future attacks more challenging to detect and mitigate. We might also see Lazarus leveraging AI and machine learning to automate aspects of their attacks, enhancing efficiency and effectiveness.
Evolving Threat Landscape Related to Zero-Day Exploits
The threat landscape surrounding zero-day exploits is constantly evolving. The high value of these vulnerabilities in the black market incentivizes their continued development and exploitation. The increasing sophistication of malware and the rise of AI-powered attack tools are further exacerbating the threat. Improved defenses are constantly being developed, but a perpetual arms race between attackers and defenders is inevitable. This requires continuous vigilance and proactive measures to mitigate the risks associated with zero-day exploits.
Visual Representation of the Attack Lifecycle
Imagine a diagram depicting a linear progression. The first stage, Initial Compromise, shows a user clicking a malicious link in a phishing email, leading to the exploitation of the Chrome zero-day vulnerability. This is depicted with an arrow pointing from an email icon to a Chrome browser icon with a red “X” indicating the exploit. The second stage, Lateral Movement, is shown as the malware spreading within the network, depicted by arrows branching out from the compromised Chrome browser to other computer icons, representing the internal network. The third stage, Data Exfiltration, is shown as data flowing out of the network, depicted by arrows moving from the network icons to a cloud icon representing the attacker’s server. Finally, Persistence, depicted by a loop back to the network, represents the malware establishing a persistent presence on the victim’s systems. The entire process is visually represented using icons and arrows, clearly indicating the sequential nature of the attack lifecycle and the techniques employed at each stage.
Last Recap: Lazarus Apt Hackers Exploit Chrome Zero Day
The Lazarus APT group’s exploitation of a Chrome zero-day vulnerability serves as a stark reminder of the ever-evolving threat landscape. While Google swiftly patched the vulnerability, the incident underscores the importance of proactive security measures. Staying updated with software patches, practicing safe browsing habits, and employing robust endpoint detection and response solutions are no longer optional; they’re essential for individuals and organizations alike. The fight against APTs is ongoing, and understanding their tactics is our best weapon in this digital arms race.





