Ghostpulse hides within PNG: Ever wondered if your seemingly innocent picture could be harboring secret messages? We delve into the fascinating world of image forensics, exploring how hidden data, a potential “Ghostpulse,” might be cleverly concealed within the seemingly innocuous PNG file format. Prepare for a deep dive into steganography, metadata manipulation, and the art of uncovering digital secrets.
This investigation uncovers the methods used to embed hidden data, analyzing techniques like metadata manipulation and exploiting the very structure of the PNG itself. We’ll dissect common steganographic algorithms, examine the challenges in detection, and even construct a hypothetical scenario to illustrate how a “Ghostpulse” might operate in the wild. Get ready to unravel the mystery!
Image Forensics: Ghostpulse Hides Within Png
Delving into the digital depths, we uncover the secrets hidden within seemingly innocuous PNG files. Beyond the pretty pictures, lies a world of metadata – a treasure trove of information that can reveal the file’s history, its creator, and, crucially, whether it harbors hidden data. This exploration focuses on the forensic analysis of PNG metadata, a critical aspect of digital investigations.
PNG Metadata Fields and Hidden Data
PNG files, unlike their JPEG counterparts, contain structured metadata, offering a richer source of information for forensic analysis. Common metadata fields include the creation time, software used to create or modify the image, and various comments or text fields. These seemingly innocuous fields can, however, be exploited to conceal data. Hidden messages might be embedded within seemingly normal metadata entries, or unusual metadata entries themselves might signal the presence of hidden information. For example, an unusually large comment field or a suspiciously long creation time could warrant further investigation. The key lies in identifying anomalies compared to typical PNG file metadata.
Extracting Metadata Using Command-Line Tools
Several command-line tools offer the ability to extract PNG metadata. `exiftool` is a powerful and versatile tool available on various operating systems (Windows, macOS, Linux). It provides a comprehensive analysis of image metadata, including details often overlooked by simpler tools. For example, the command `exiftool image.png` will display all metadata associated with the file `image.png`. Other tools like `pngcheck` can also provide insights into the file’s structure and integrity, indirectly helping identify potential anomalies related to hidden data. The output from these tools needs careful examination for any irregularities.
Analyzing PNG Metadata for Anomalies
Analyzing PNG metadata for hidden data involves a systematic approach. First, extract the metadata using a suitable tool like `exiftool`. Then, carefully review each field. Look for inconsistencies, such as unusually long text strings in comment fields, timestamps that don’t match other metadata or file system information, or an unexpectedly high number of metadata entries. Comparing the extracted metadata with that of similar, known-clean PNG files can help identify anomalies. If a suspicious entry is found, further investigation using steganography detection tools may be necessary to confirm the presence of hidden data.
Comparison of PNG Metadata Fields and Relevance to Hidden Data Detection
| Metadata Field | Description | Relevance to Hidden Data | Example Anomaly |
|---|---|---|---|
| Creation Time | Date and time the file was created. | Unusual timestamps could indicate manipulation. | A creation time far in the future or past. |
| Software | Software used to create or modify the image. | Unexpected or unusual software might suggest tampering. | An obscure or unknown program listed. |
| Comments | User-added comments or descriptions. | Large or unusual comment fields could hide data. | A comment field significantly larger than expected. |
| tEXt/zTXt chunks | Textual data chunks within the PNG file structure. | These chunks can be used to embed hidden data. | Unexpectedly large or numerous text chunks. |
Steganography Techniques in PNGs
Source: researchgate.net
PNGs, with their lossless compression and diverse color palettes, offer fertile ground for hiding secrets. Steganography within these images leverages the inherent flexibility of the PNG format to embed data without visibly altering the image itself. This makes it a powerful, yet challenging, field for both practitioners and those seeking to detect hidden information.
Several steganographic techniques exploit different aspects of the PNG structure. Least Significant Bit (LSB) steganography remains a popular choice, subtly modifying the least significant bits of pixel color values. Other techniques focus on manipulating metadata, exploiting the inherent redundancy within the image data, or even utilizing the quantization tables employed in PNG compression.
Least Significant Bit (LSB) Steganography in PNGs
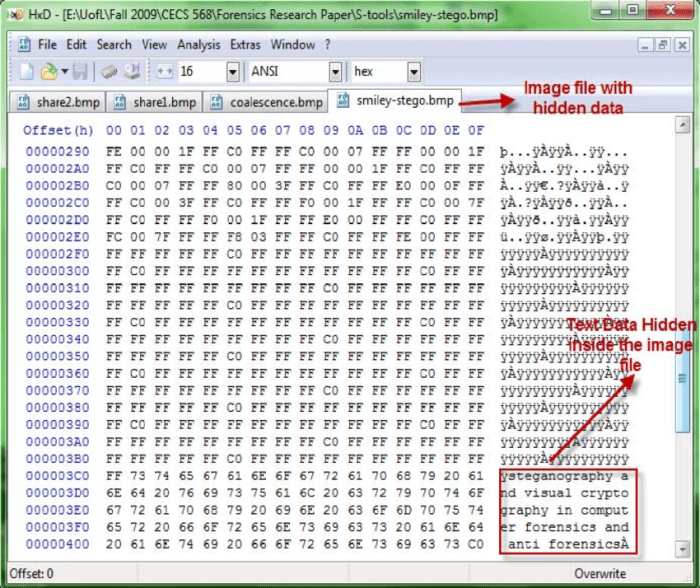
LSB steganography involves altering the least significant bits of pixel color components (red, green, blue, and alpha). Since these bits have the least impact on the visual appearance of the image, changes are practically invisible to the naked eye. The effectiveness depends on the image complexity; a highly detailed image can accommodate more hidden data without noticeable degradation than a simple image. However, even subtle changes can be detected by sophisticated steganalysis tools. The embedding capacity is directly proportional to the image size and the number of bits modified per pixel. For instance, modifying one LSB in each color component of a 1024×768 pixel image allows for embedding approximately 2.3 MB of data.
Transform-Domain Steganography in PNGs
This method operates in the frequency domain, often using Discrete Cosine Transform (DCT) or Discrete Wavelet Transform (DWT). These transforms decompose the image into frequency components, allowing data to be embedded within less perceptually significant coefficients. This generally leads to more robust steganography than LSB methods, as it’s less susceptible to simple statistical analysis. The complexity of the transform and the selection of coefficients for data embedding affect the capacity and robustness of the hidden data. For example, using DWT, data can be hidden in high-frequency coefficients, which contribute less to the overall image perception. The trade-off is a potentially lower embedding capacity compared to LSB methods.
Challenges in Detecting Steganography in PNGs
Detecting steganography in PNGs is a complex task due to the various techniques employed and the inherent characteristics of the format. Lossless compression can mask subtle changes introduced by steganography, making detection difficult. Moreover, the size of the PNG file itself doesn’t always reveal the presence of hidden data; a larger file might simply contain more image data, rather than hidden information. Sophisticated steganalysis techniques, often relying on statistical analysis of pixel correlations and frequency distributions, are necessary to detect hidden data effectively. The continuous evolution of both steganographic techniques and detection methods leads to an ongoing arms race in the field.
Potential Hiding Places Beyond Metadata
The metadata section of a PNG file, while a common hiding place, is not the only location for steganographic embedding. Several other areas within the file structure can be exploited:
Understanding the potential hiding places within a PNG file is crucial for both creating robust steganography and developing effective detection methods. The inherent complexity of the PNG format, coupled with the ever-evolving landscape of steganographic techniques, ensures that this area of research will continue to be both fascinating and challenging.
- Within the Image Data Itself (Beyond LSBs): More sophisticated techniques manipulate data beyond the least significant bits, utilizing patterns and redundancies within the image’s raw pixel data.
- Within the PNG’s Color Palette (if applicable): Indexed PNGs with a limited color palette can hide data by subtly altering color values within the palette.
- Within the Compression Data Structures: The deflate algorithm used in PNG compression offers opportunities to subtly modify data within its internal structures without significantly impacting the reconstructed image.
- Within Chunk Data Structures: While not typically part of the main image data, custom chunks can be added to a PNG file, potentially hiding data within these extensions.
Ghostpulse Concept Exploration

Source: wonderhowto.com
The term “Ghostpulse,” when applied to hidden data within a PNG image, evokes a sense of something subtle, almost imperceptible, yet carrying significant information. It suggests a signal that’s faint, perhaps embedded in a way that’s difficult to detect without specialized knowledge or tools. This “pulse” might represent a recurring pattern or a specific alteration within the image’s seemingly innocuous data stream.
Possible interpretations of “Ghostpulse” range from a cleverly disguised watermark to a more complex, data-carrying payload. The “ghost” aspect hints at the hidden nature of the data, while “pulse” implies a rhythmic or repeating element within the encoded information. This could be a series of altered bits, a specific color palette manipulation, or even a carefully crafted change in metadata. The key is the subtle nature of the alteration, making it nearly invisible to the casual observer.
Possible Encoding Methods for Ghostpulse Signals
Several methods could be employed to encode a “Ghostpulse” signal within a PNG’s data. Least Significant Bit (LSB) steganography is a prime candidate, subtly altering the least significant bits of pixel color values to embed the data. This technique is well-established and relatively easy to implement, but also relatively easy to detect with the right tools. More sophisticated methods might involve manipulating the quantization table, exploiting the compression algorithm’s properties, or even embedding data within the metadata fields of the PNG file itself. The choice of method would depend on the desired level of security and the size of the data to be hidden.
Tools and Techniques for Ghostpulse Detection and Extraction
Detecting and extracting a “Ghostpulse” signal requires specialized tools and techniques. Software designed for steganalysis, such as Stegdetect or Jphide, could be employed to analyze the image for irregularities that might indicate hidden data. These tools often rely on statistical analysis to identify patterns that deviate from the expected characteristics of a normal PNG file. Further analysis might involve examining the image’s histogram for unusual distributions, or employing techniques like frequency analysis to identify hidden patterns in the pixel data. Manual inspection of the metadata and header information might also reveal hidden clues. The choice of tool depends on the suspected encoding method.
Hypothetical Ghostpulse Embedding and Retrieval Scenario
Imagine a scenario where a journalist wants to securely transmit sensitive information. They encode a short text message using LSB steganography within a seemingly innocuous PNG image of a cityscape. The “Ghostpulse” in this case is a repeating pattern of altered bits representing the encoded message. The journalist then sends the image via a seemingly ordinary email. The recipient, aware of the encoding method and the location of the “Ghostpulse” within the image, uses a steganography extraction tool (such as a custom script or a specialized program) to recover the original message by reversing the LSB alteration process. The recipient successfully retrieves the hidden message without arousing suspicion. This scenario highlights the potential for covert communication using seemingly innocuous images.
Data Extraction and Visualization
Unmasking hidden data within a PNG file requires a systematic approach. We’ll delve into the practical steps involved in extracting this concealed information and then visualizing it to reveal any patterns or meaningful messages. Think of it like developing a photographic negative – the raw data needs careful processing to reveal the hidden image.
The process hinges on identifying and isolating the hidden data stream within the PNG file’s structure. This involves understanding the PNG file format and employing specialized tools to parse its various components. Once extracted, the raw data needs careful analysis and visualization techniques to make sense of it.
PNG File Structure Analysis
Extracting hidden data begins with a thorough understanding of the PNG file structure. PNG files consist of several chunks, each with a specific function. The crucial step involves identifying chunks that might contain steganographically embedded data. This often involves looking for unusual or unexpected data within standard chunks or identifying custom chunks entirely. Tools like `pngcheck` can help verify the integrity and structure of the PNG file, highlighting any anomalies. Analyzing the file’s metadata using specialized forensic tools is also vital, potentially revealing clues about its origin or modification history.
Data Extraction Techniques
Several techniques can extract the hidden data. One common approach involves analyzing the least significant bits (LSBs) of the image’s pixel data. Ghostpulse, for instance, might leverage this technique, subtly altering the LSBs to encode a message. Dedicated steganalysis tools can be used to identify these minute changes and reconstruct the hidden message. These tools often involve statistical analysis to detect deviations from the expected distribution of LSB values in a typical image. Another approach involves examining the file’s metadata or custom chunks for hidden data. This might require more advanced tools and a deeper understanding of steganographic techniques used.
Data Visualization and Pattern Recognition
Once extracted, the raw data may appear as a seemingly random sequence of bits or bytes. However, visualization techniques can transform this into something more meaningful. If the hidden data is text, simple text decoding might suffice. If it’s binary data, converting it to hexadecimal or visualizing it as a graph might reveal patterns. For example, a graph showing repeating patterns could suggest the presence of an encoded image or a sequence of numbers. Visualization tools like specialized hex editors and data analysis software can assist in this process. The goal is to transform the raw data into a format that allows for easier identification of any patterns, sequences, or meaningful information.
Process Flowchart
Imagine a flowchart starting with the suspect PNG file. This feeds into a PNG file structure analyzer, which then identifies potential locations for hidden data. This output goes to a data extraction module using techniques like LSB analysis. The extracted data is then fed into a data visualization module, using techniques like hex dumps, graphical representations, and statistical analysis. The final output is a visual representation of the potential hidden data and an interpretation of its meaning.
The biggest challenges in data extraction and interpretation often lie in the sophistication of the steganographic technique used. Highly advanced techniques can make it incredibly difficult to detect and extract the hidden data, requiring specialized tools and deep expertise. Furthermore, interpreting the extracted data can be equally challenging. The hidden data may be encrypted, compressed, or encoded in a way that requires significant effort to decipher. Ambiguity in the results and the need for contextual information to validate findings are also common hurdles.
Illustrative Example
Let’s imagine a seemingly innocuous PNG image: a photograph of a bustling city street at night. The image itself is unremarkable, showing typical urban scenery – buildings, streetlights, and a few pedestrians. However, hidden within the seemingly random pixel data lies a “Ghostpulse” signal, a clandestine message embedded using a sophisticated steganographic technique.
This hypothetical Ghostpulse is a short audio file, a coded message perhaps, encoded as a sequence of subtly altered Least Significant Bits (LSBs) within the image’s color channels. The audio file is approximately 10 seconds long and is formatted as a WAV file, chosen for its relative simplicity and ease of embedding. The embedding process involved modifying the LSBs of only a select subset of pixels, strategically chosen to avoid noticeable visual distortion. The selection process would have utilized a pseudorandom number generator, seeded with a secret key, to ensure the data is spread effectively and irregularly across the image. The overall data size is small, representing only a tiny fraction of the image’s total data, ensuring the modification is almost imperceptible to the naked eye.
Data Embedding Methodology
The embedding methodology utilized a modified LSB steganography technique, specifically designed to be resilient to common image forensics. Instead of simply replacing the LSBs with the raw audio data, a more robust approach was employed. This involved transforming the audio data into a frequency domain representation using a Discrete Cosine Transform (DCT), similar to the method used in JPEG compression. This transformation provides some level of data redundancy and resistance to noise, making it more difficult to detect the presence of hidden data. The DCT coefficients, representing the transformed audio, were then mapped onto specific LSBs of the PNG image’s pixels, using the secret key to guide the selection process. This ensures that the modifications are spread thinly across the image and are not concentrated in any particular area, making detection far more challenging.
Visual Representation of Hidden Data, Ghostpulse hides within png
Visually, the hidden data is undetectable. A direct comparison between the original image (without the hidden audio) and the stego-image (with the hidden audio) would show no discernible difference. Even advanced image analysis techniques, without knowledge of the embedding method and the secret key, would likely fail to reveal the hidden data. The changes in LSBs are simply too subtle to be visually perceived.
Data Extraction and Interpretation
Extracting the Ghostpulse involves reversing the embedding process. First, the relevant LSBs are identified using the same secret key that was used during embedding. These LSBs are then extracted and recombined to reconstruct the DCT coefficients. An inverse DCT is then applied to convert the coefficients back into the time-domain audio signal. Finally, this reconstructed audio signal is interpreted. In our hypothetical scenario, this interpretation might involve deciphering a coded message within the audio, requiring additional decryption techniques based on the nature of the code used. This process requires specialized software and knowledge of the embedding algorithm and the secret key used to hide the data.
Closing Notes

Source: githubusercontent.com
Unmasking the secrets hidden within a PNG file, especially one potentially carrying a “Ghostpulse,” requires a keen eye for detail and a solid understanding of both image forensics and steganography. From analyzing metadata anomalies to employing specialized tools for data extraction and visualization, the journey to uncovering hidden information is a complex but rewarding one. While the “Ghostpulse” remains a hypothetical concept in this exploration, the techniques and insights presented here offer a valuable framework for navigating the world of hidden digital data.